Beyond Fake INEC Portal, Threat Actor Targeting Users In 3 African Countries

Just some days ago, a fake INEC recruitment portal shows up in our space. And several media houses have reported INEC issuing a disclaimer around the authenticity of the platform and advising Nigerians not to fall prey to such gimmicks from malicious threat actors which is after their Personally Identifiable Information (PII) for further social engineering attacks.
https[:]//yournewclaims[.]com/Inec-Recriutment/ >>>>>>>>>>> If you check well, there is a spelling error with the word “Recriutment“

But we did a deeper analysis of the recruitment portal, considering our prediction of related campaigns against elections in the 2022 CyberPlural Annual Report; here is what we came up with.
First, we want to understand the actor’s motivation and possible action on objectives when a user intends to follow up with the form but in the process, we came across something huge.
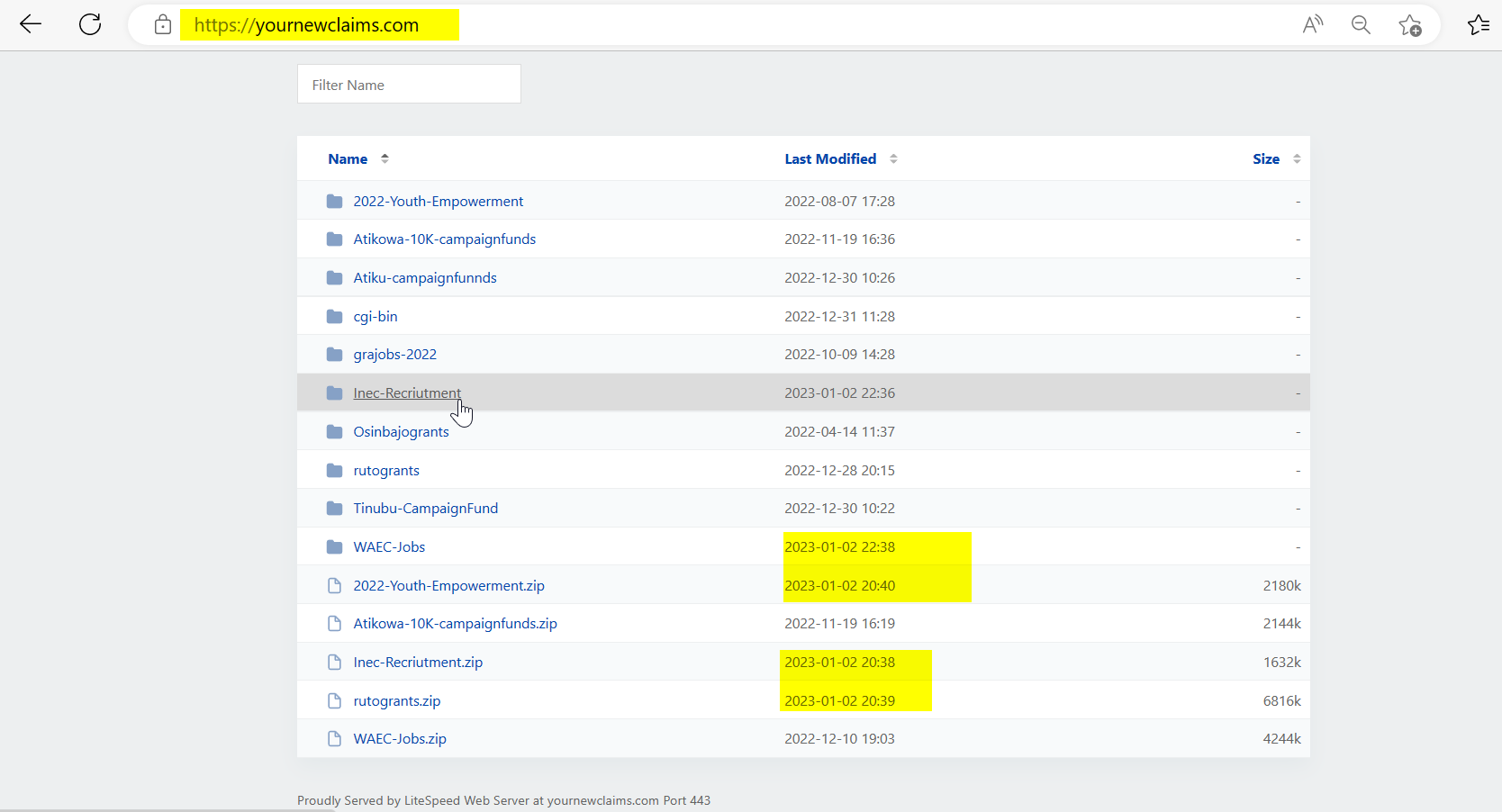
The domain that was hosting this malicious portal was found to have been hosting similar fake platforms since 2022 templating fake youth empowerment, fake jobs in Nigeria and Ghana, visa sponsorship and fake grants from presidential aspirants as contained in the above image and the actor just recently updated it with the fake INEC portal, WAEC-Jobs and rutogrants for his 2023 campaign.
What was common among all fake page setups was that the malicious actor has been following up with the trends of events and activities in three (3) different countries Nigeria, Ghana and Kenya on which all of the pages got implemented to phish unsuspecting users.

The medium of distribution has been WhatsApp Groups as shown below using the Lyupz Shortner to hide/masquerade the threat actor’s main domain. For you to know whether a group you belong to has received such a message, you can search for lyupz.com in your WhatsApp to identify malicious URLs abusing the Lyupz Shortner
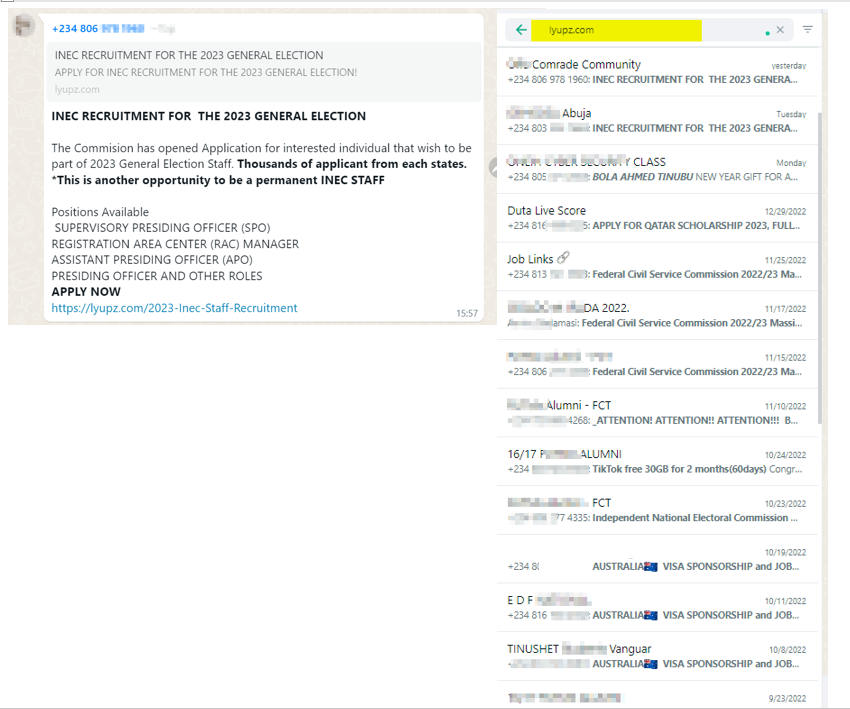
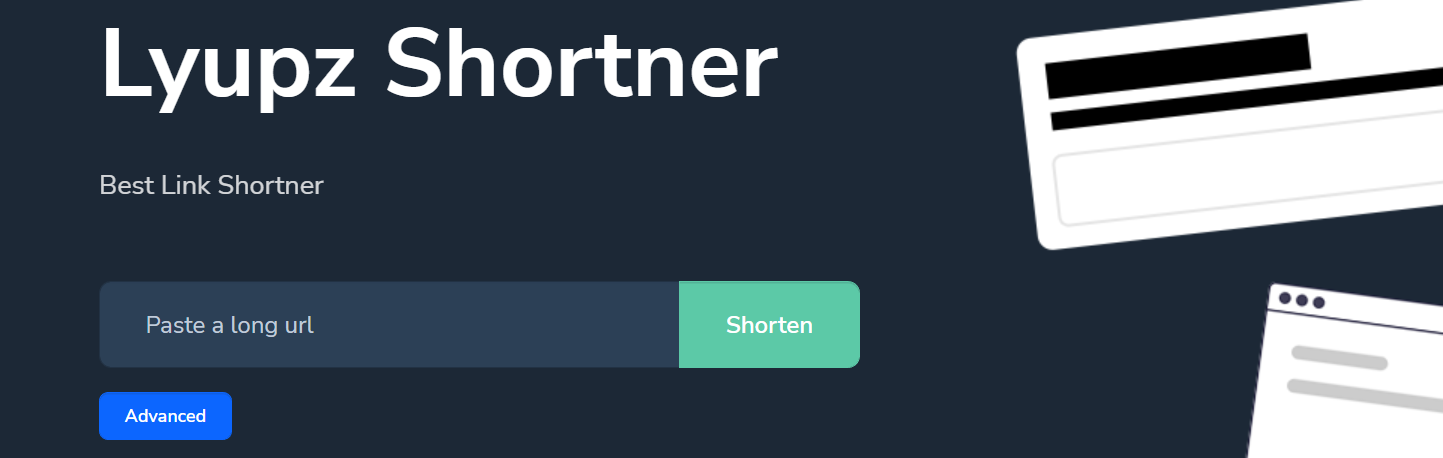
The most interesting thing about this campaign is that unsuspecting users are always the ones helping to distribute/share the link around for the threat actor. As many believe they are helping others to get to know of new opportunities but unknowingly helping the threat actor to possibly succeed by amplifying the campaign.
We recommend that any link users cannot verify its sources should not be amplified on social platforms like Facebook, and WhatsApp to prevent unsuspecting users from falling into traps of the threat actors who are hell bend at collecting users’ PII and other sensitive information that can be leveraged in social engineering to either defraud victims or impersonate them.
Note that other technical information about this infrastructure is currently being documented, and all further changes observed will be updated as IoC / IoB going forward.
Indicators of Observations (IoBs)
https[:]//yournewclaims[.]com/
https[:]//yournewclaims[.]com/Inec-Recriutment/
https[:]//yournewclaims[.]com/2022-Youth-Empowerment/
https[:]//yournewclaims[.]com/Atikowa-10K-campaignfunds/
https[:]//yournewclaims[.]com/Atiku-campaignfunnds/
https[:]//yournewclaims[.]com/grajobs-2022/
https[:]//yournewclaims[.]com/Osinbajogrants/
https[:]//yournewclaims[.]com/ rutogrants/
https[:]//yournewclaims[.]com/
https[:]//lyupz.com/ – Lyupz Shortner to masquerade main domain.
206.72.205[.]68

2 Comments
Awesome report! This will help enlighten People who share these links to people to do due diligence in checking such links for of suspicious activities or share information from authentic links only.