Zero-day vulnerabilities literally have no remediation at the time of discovery and or exploitation. Think about it: They are called zero-day vulnerabilities for a reason, […]
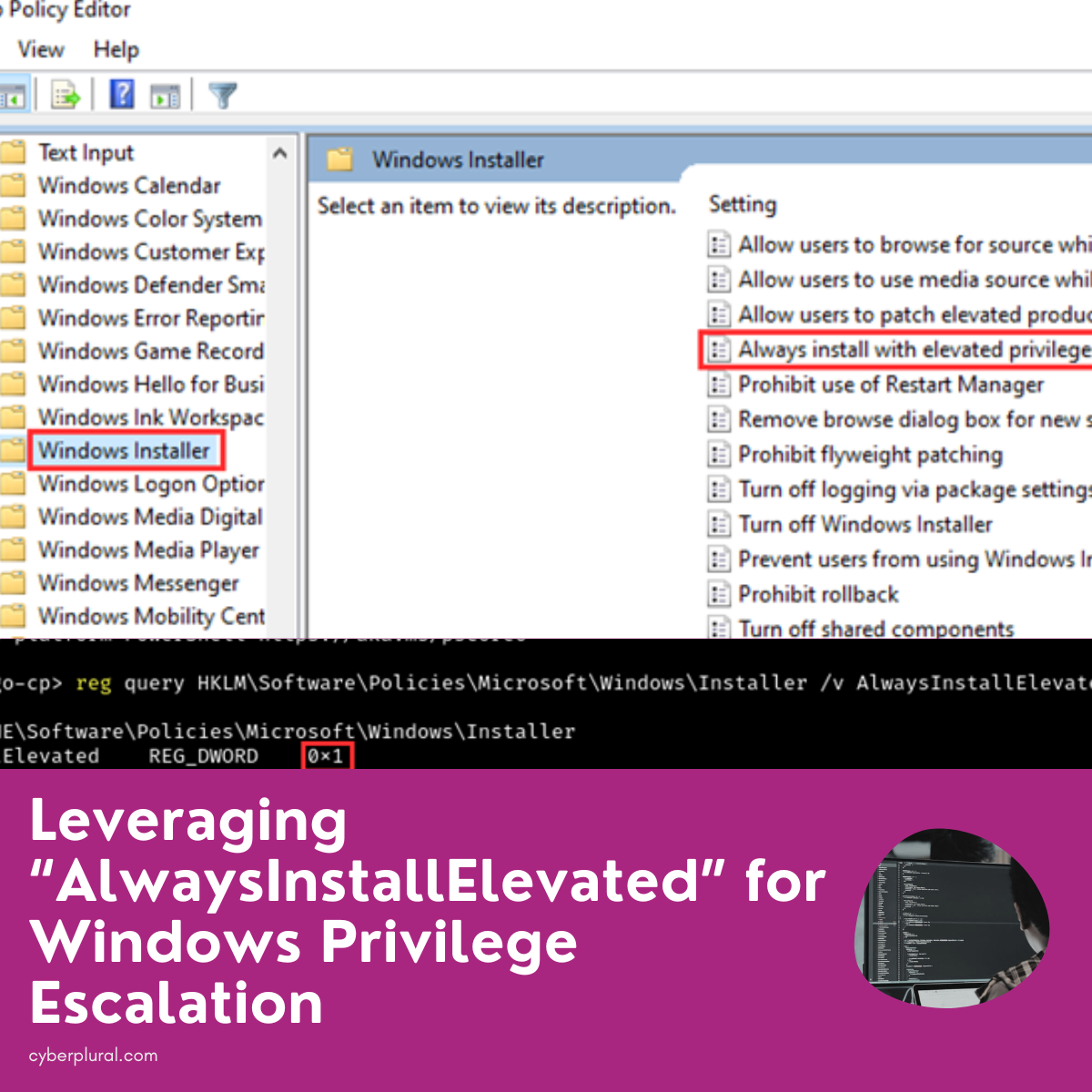
Leveraging “AlwaysInstallElevated” for Windows Privilege Escalation
The “AlwaysInstallElevated” setting in Windows is a misconfiguration that allows low-privileged users to escalate privileges to SYSTEM by installing MSI packages. This setting is often […]
How to Build a Robust Defense in Depth with Snort and pfSense
What is Defense in Depth Defense in Depth is a cybersecurity strategy that employs multiple layers of security controls throughout an organization’s IT environment to […]
AD Explained: Part 4 – Fine-Tuning Controls for Privileged Accounts
Highly privileged accounts (Domain Admins, Administrators, Enterprise Admins, etc.) are the ultimate goal for every threat actor or hacker out there. These accounts are sought […]
Role of Digital Forensics in Incident Response
Understanding Digital Forensics Digital forensics is critical in cybersecurity because it allows investigators to reconstruct digital events, trace the source of attacks, and provide evidence […]
Advisory: Exploitation of CVE-2023-27532 on Veeam by Ransomware Groups
Recommendation It has been reported that the Estate Ransomware Group and the Phobos Ransomware Group have been exploiting the CVE-2023-27532 vulnerability in Veeam Backup & […]