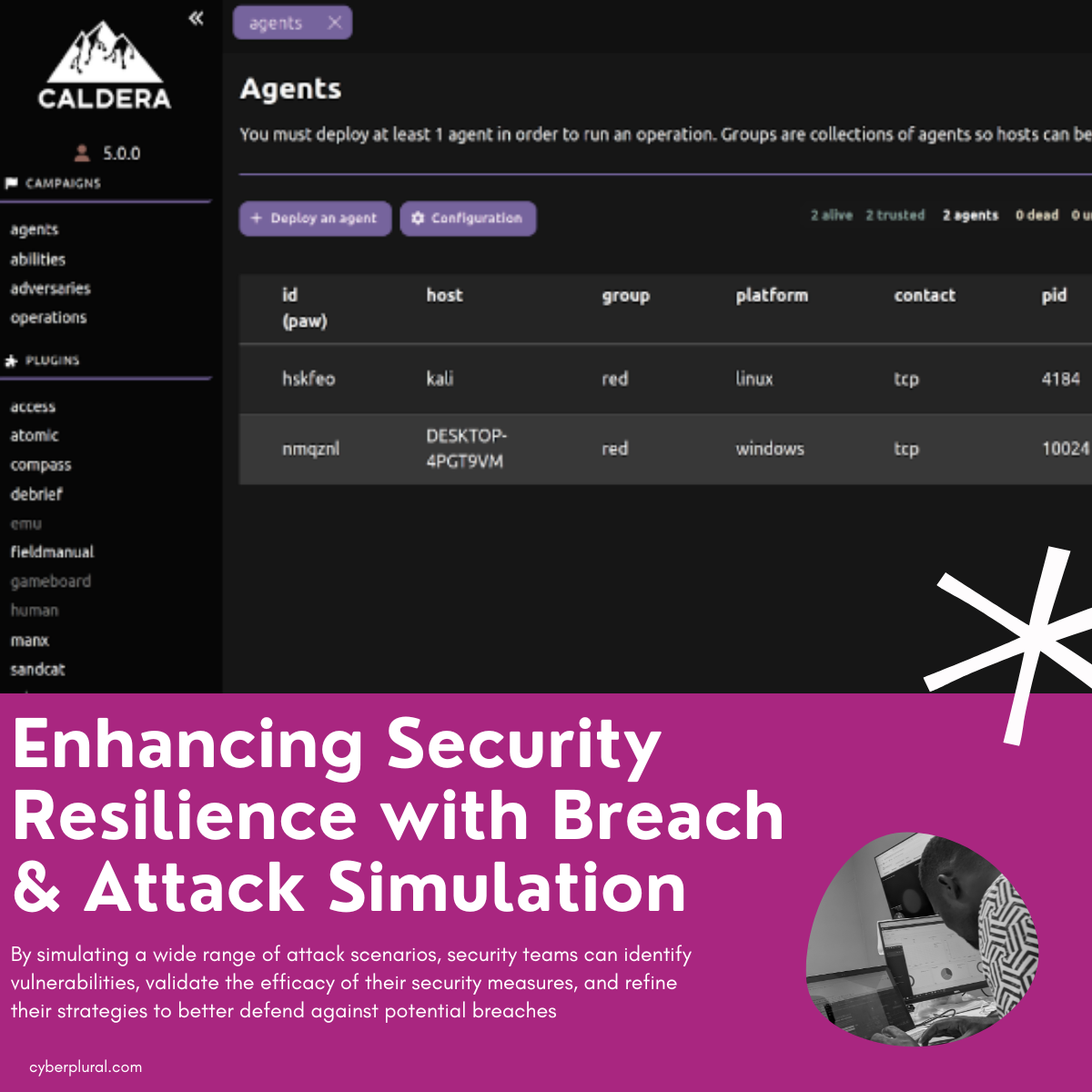
In the ever-evolving landscape of cybersecurity, organisations face an ongoing battle to stay one step ahead of threat actors. Traditional security approaches often fall short […]
Category: Breach
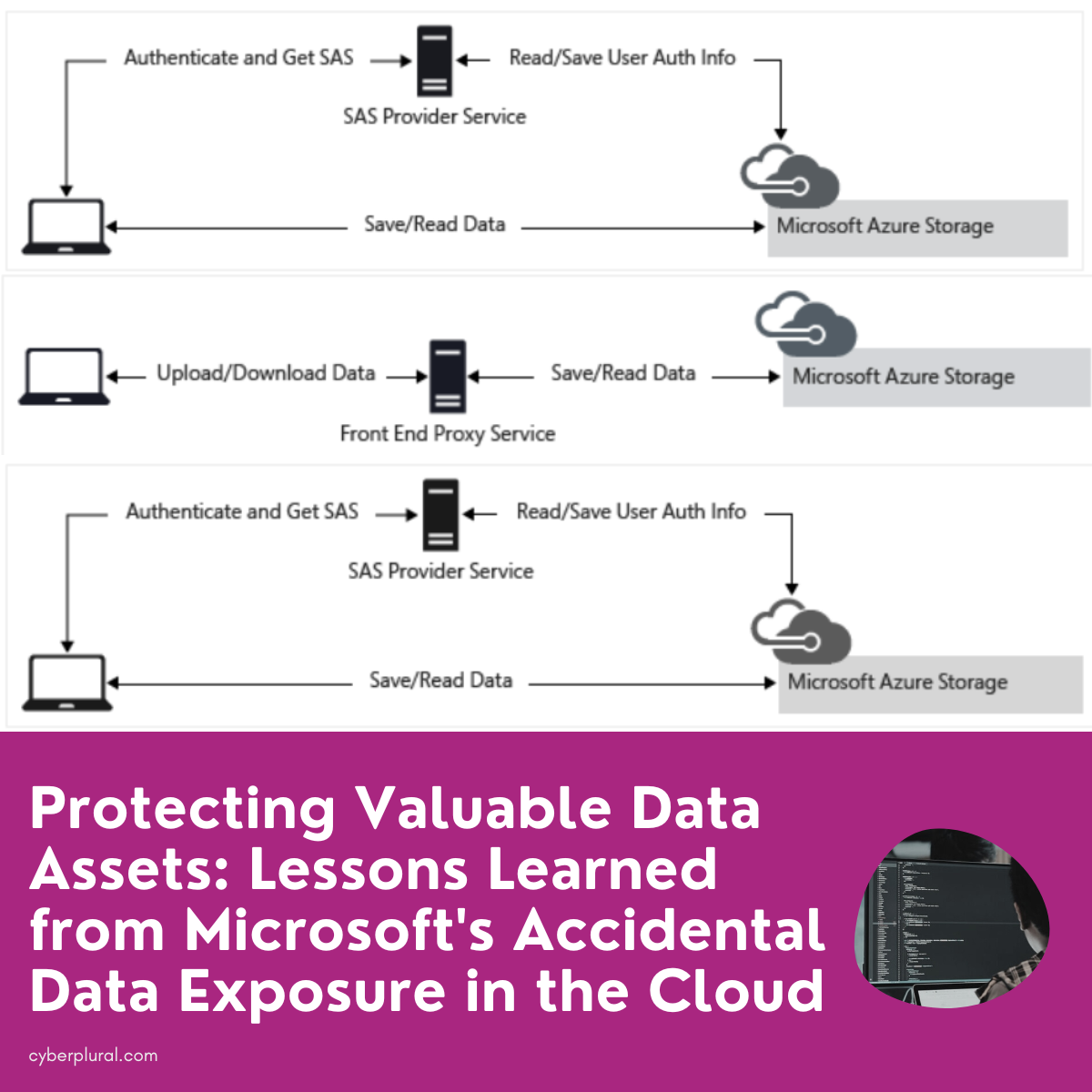
Protecting Valuable Data Assets: Lessons Learned from Microsoft’s Accidental Data Exposure
In the ever-evolving landscape of cloud technology, data security remains paramount. Recent events have shed light on the critical importance of safeguarding sensitive information, and […]
2023 | Q1 Report – Incident reports, Major CVEs & Threat Intel
Here is our 2023 Q1 Report speaking to incident reports, major CVEs and threat intel as captured in the first 3 months of 2023. Capturing […]
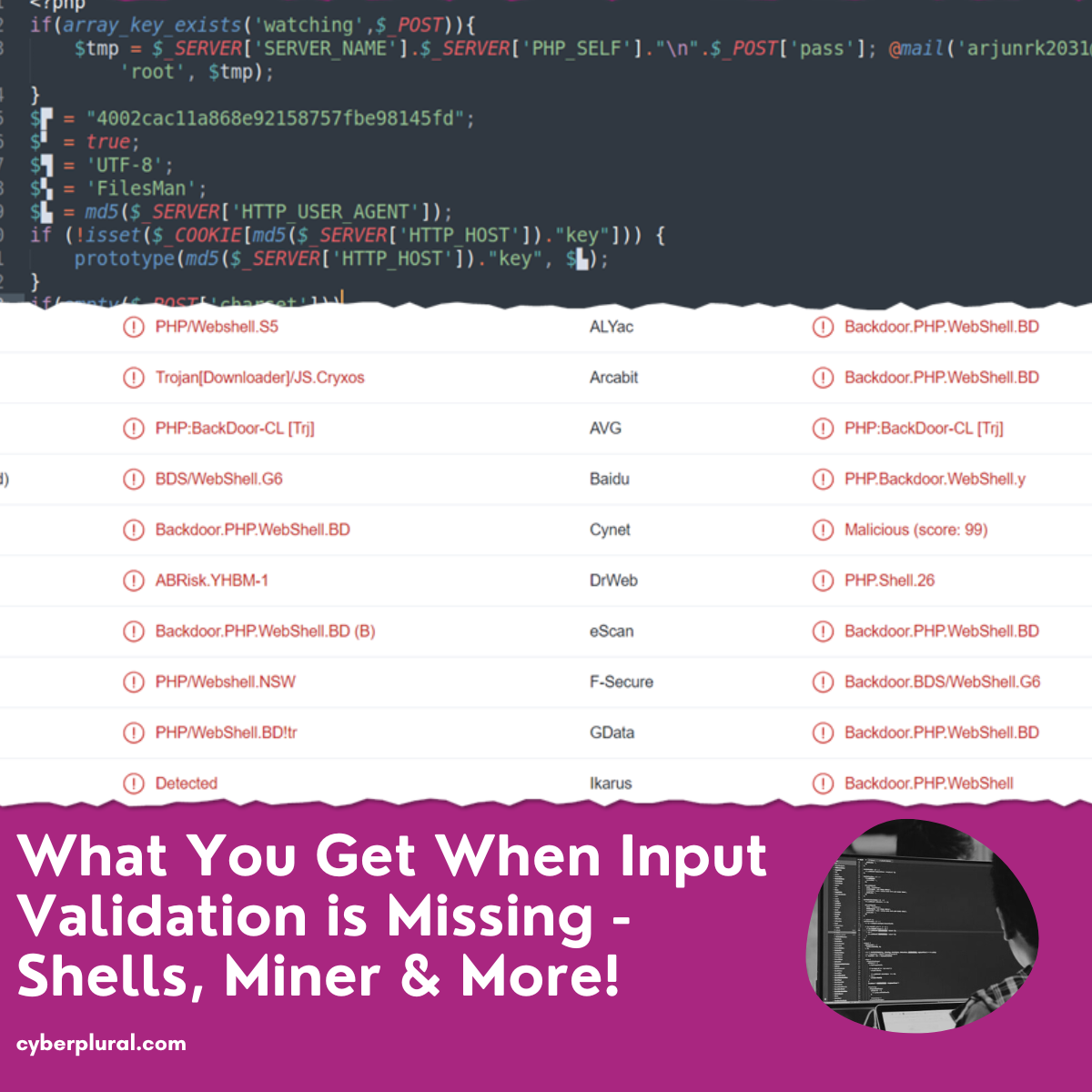
What You Get When Input Validation is Missing – Shells, Miner & More
Web applications and software frequently need user interaction to function properly. Users must be able to provide their email addresses and other personal information at […]
2022 | Q2 Report – Lessons Learnt
Our 2022 | Q2 Report takes a look at the #lessons learnt from significant #cyber incidents reported in this quarter, reported CVEs and Threat #Intel and what we can do better […]
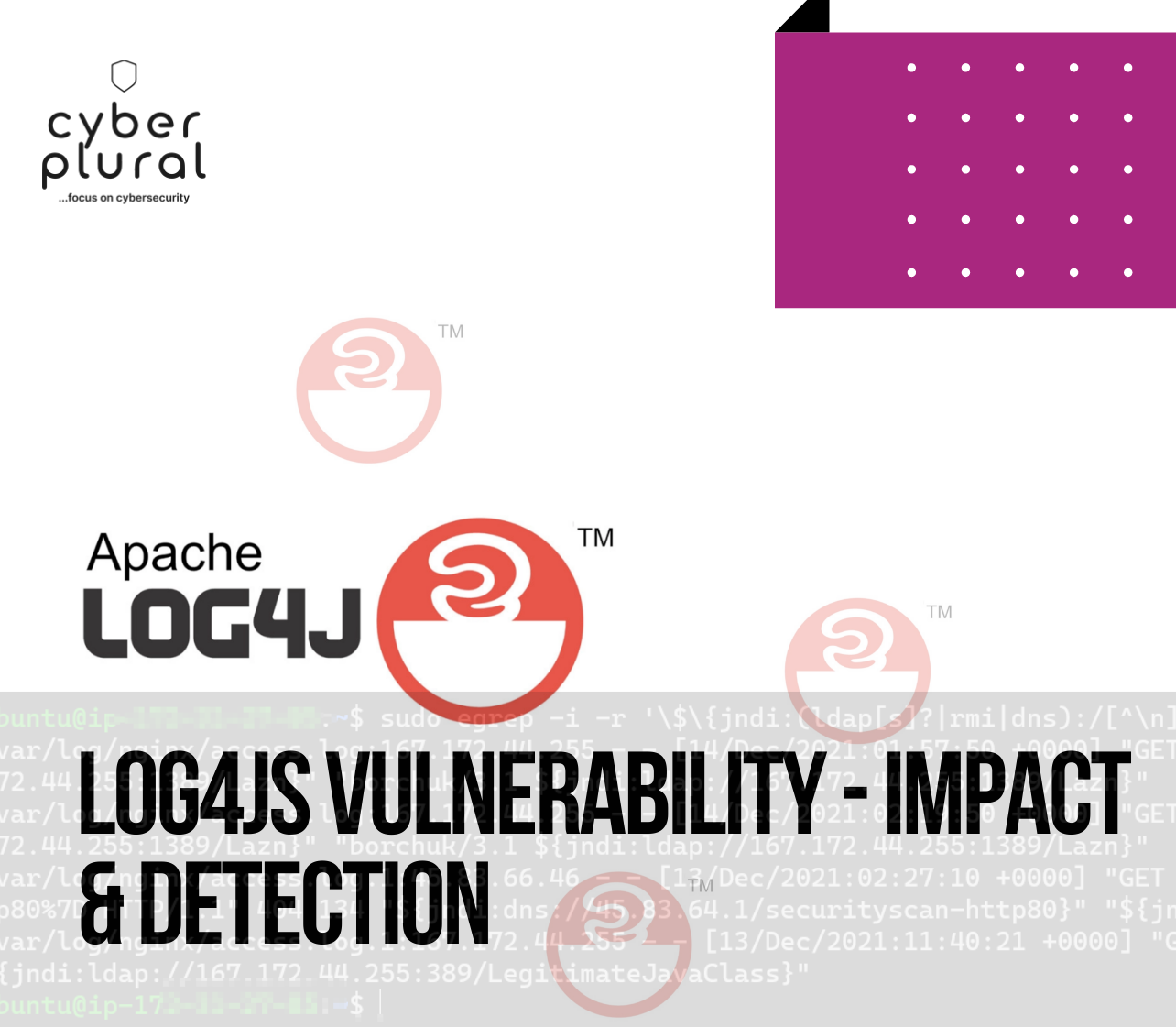
Log4j Vulnerability: Impact & Detection
By now, you’ve likely heard of the latest Java-based vulnerability CVE-2021-44228, a critical zero-day vulnerability related to Apache Log4j Java logging library. Affecting everything from […]