In the era of digital interconnectedness, Nigeria’s digital landscape is witnessing rapid growth, accompanied by a surge in cyber security threats. As the most populous […]
Category: Incident Response
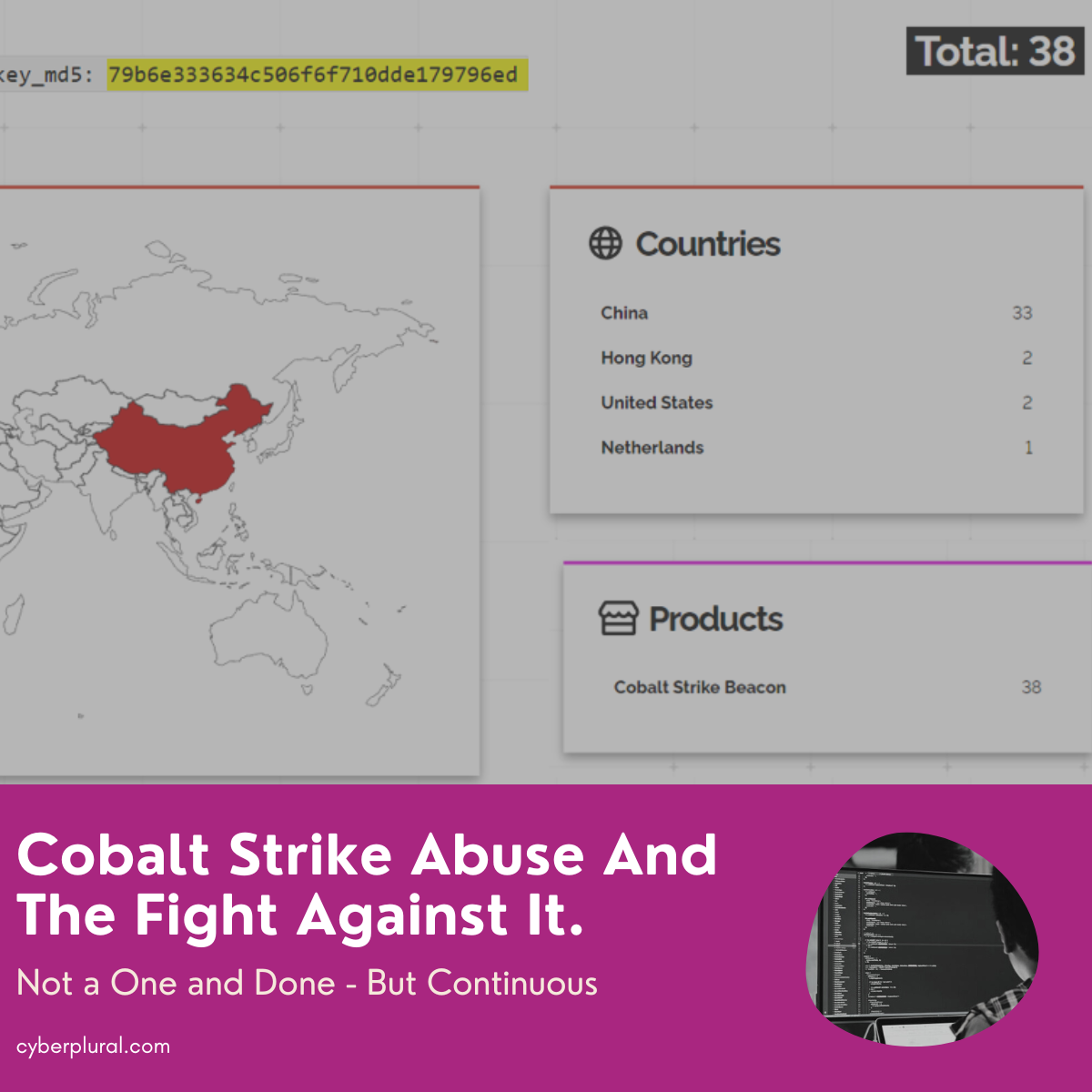
Cobalt Strike Abuse And The Fight Against It
Just last week Microsoft’s DCU, Fortra and Health-ISAC moved to go legal and technical to disrupt cracked, legacy copies of Cobalt Strike and abused Microsoft […]
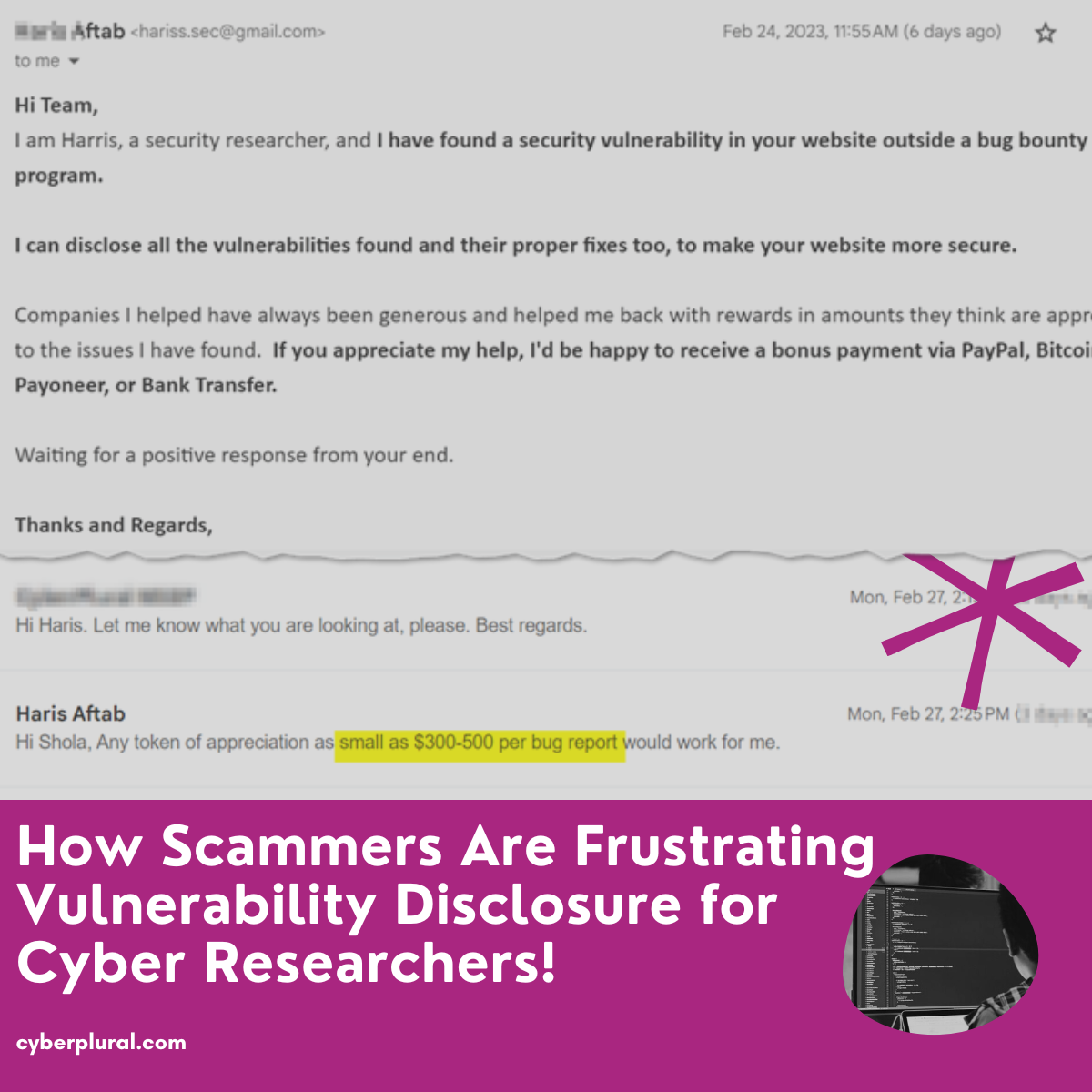
How Scammers Are Frustrating Vulnerability Disclosure for Cyber Researchers!
How would you react if you found this in your company inbox? You may want to ignore and many will take the fear bait and […]
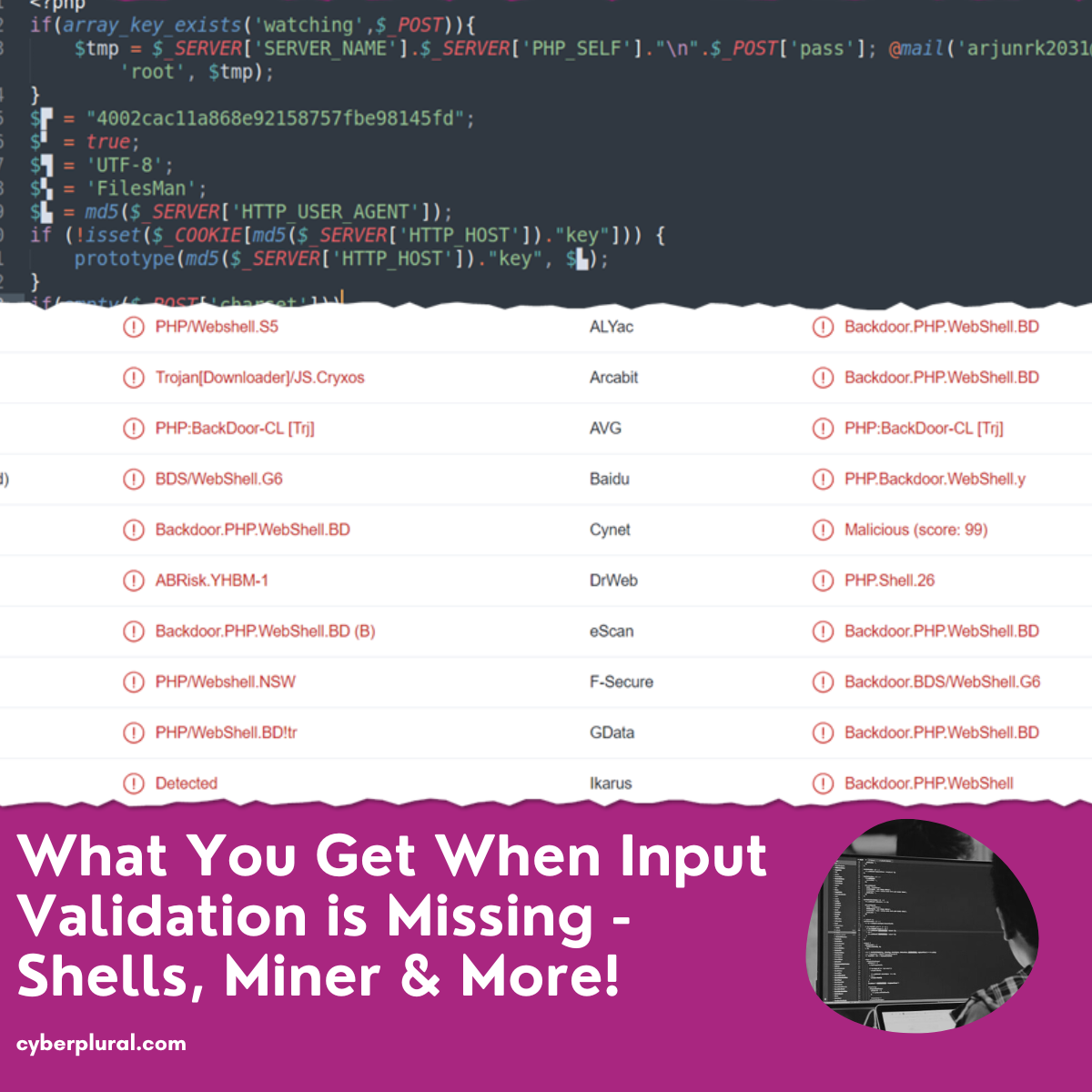
What You Get When Input Validation is Missing – Shells, Miner & More
Web applications and software frequently need user interaction to function properly. Users must be able to provide their email addresses and other personal information at […]
CyberPlural Annual Report 2022
We started into the year by providing quarterly reports of what was happening with the cyber threat landscape based on what we are seeing across the globe. […]
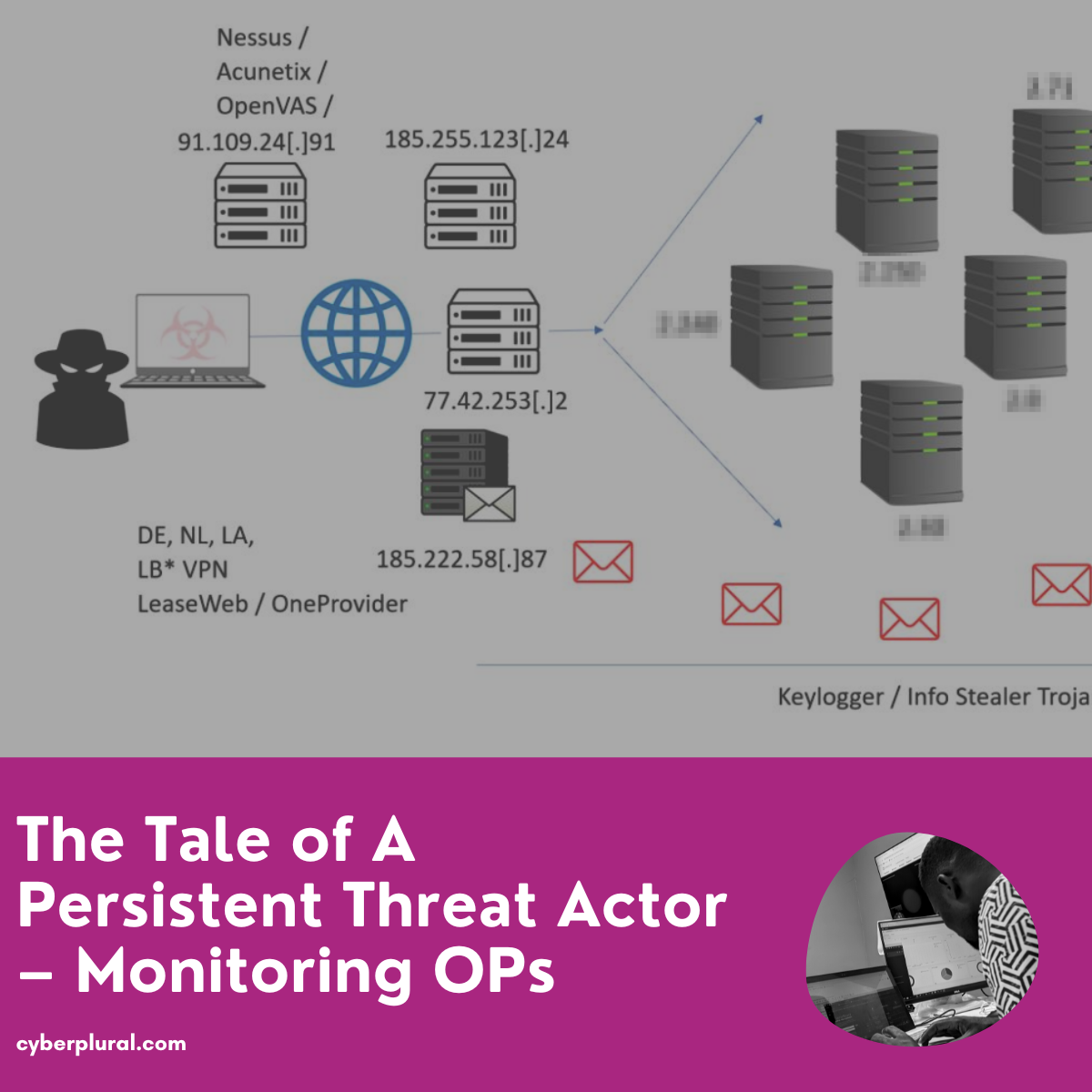
The Tale of A Persistent Threat Actor – Monitoring OPs
The benefit that comes with having visibility (proactive monitoring) in and around your organization’s network perimeter cannot be underestimated in cyber defense and understanding the […]