How Scammers Are Frustrating Vulnerability Disclosure for Cyber Researchers!
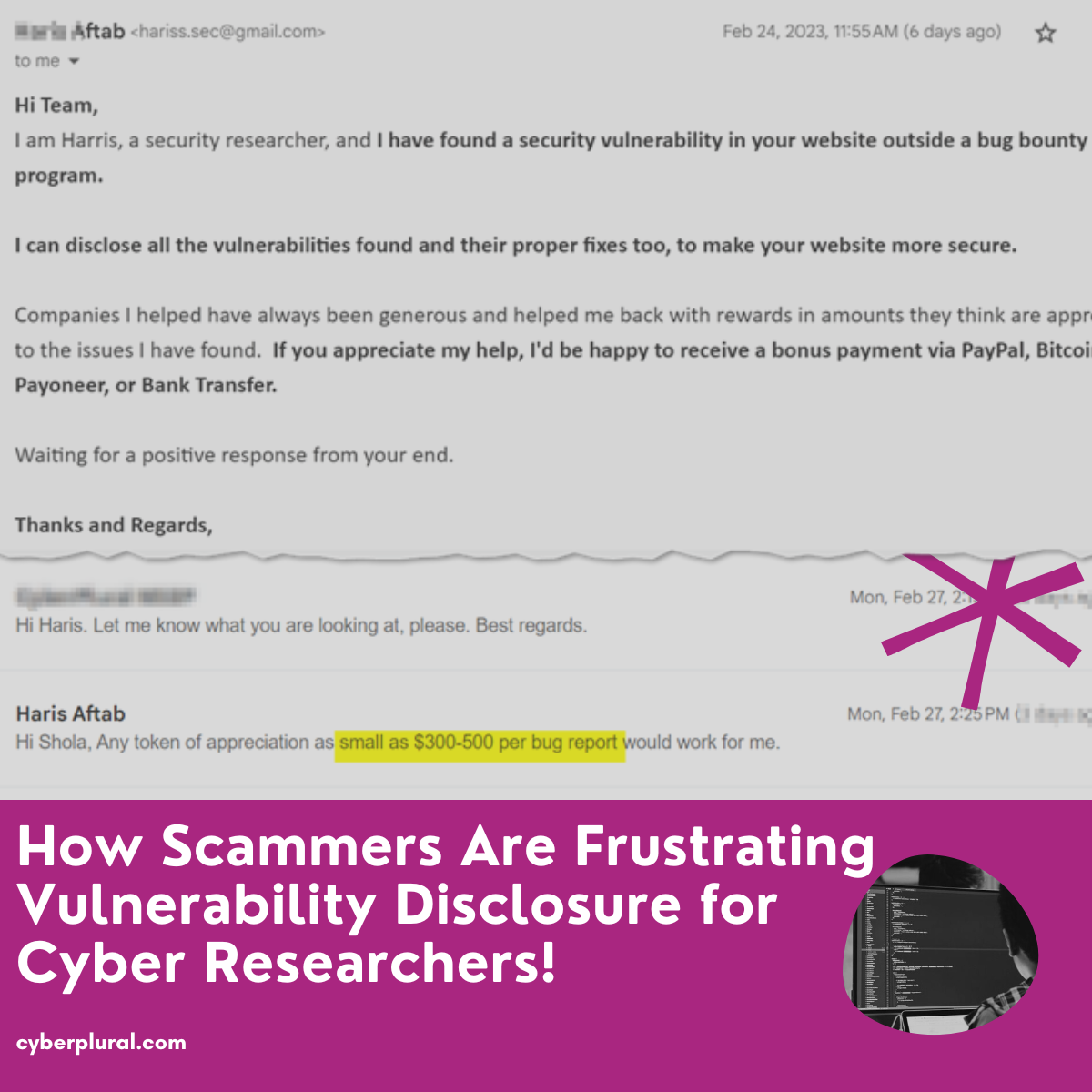
How would you react if you found this in your company inbox? You may want to ignore and many will take the fear bait and want to follow up with the sender to find out more about this vulnerability.
We did follow up on this case and here is what we found out;
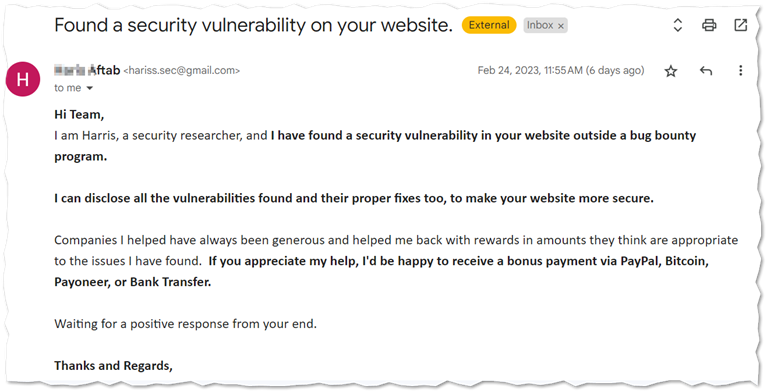
Because the email is an unsolicited attempt to get a response using fear. It’s the fact that the sender ultimately left out the details of what the issue is. You have to contact them to get a response and already stated that they expect a token of appreciation.
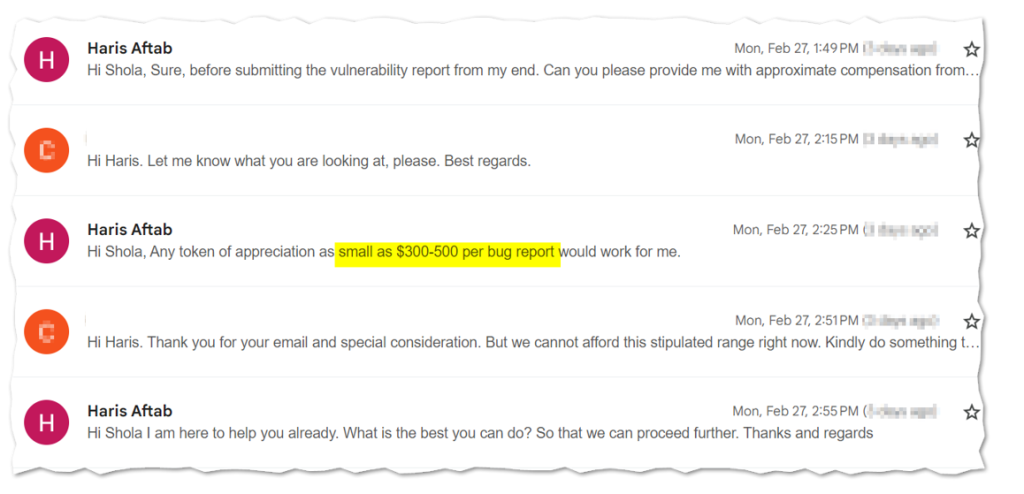
We also noticed a quick start from the TA stating his price for the bug report, imagine a sum of $300-$500 as a token of appreciation. At this point, we don’t even have an idea of what bug he is trying to report, which made him think the criticality of the finding is worth that range.
This is to reinforce the fear but we have one hypothesis at this point which is that he might not have even checked the site as it is just an informational-based website, meaning the website is not housing any sensitive information and there are no issues with configuration.
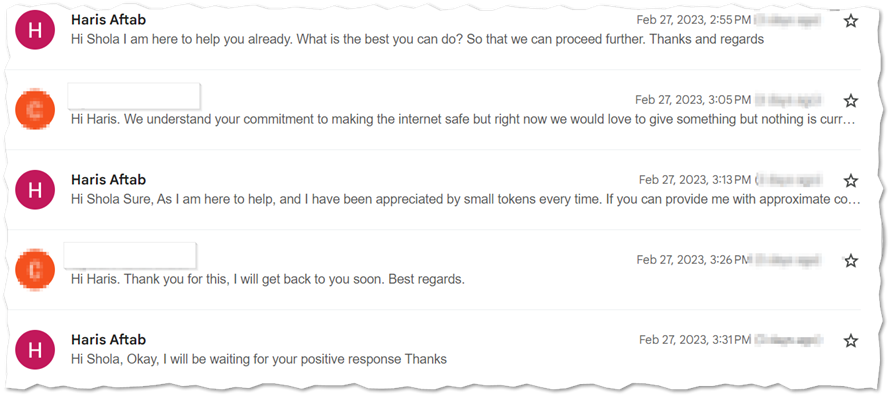
Further negotiation made the TA change the price range back to $100-$150. At this point, we insisted on opting in at a range lower than $100 which he is not willing to do but opted in for $100 as the least with the option of sending the Wise account or a generated Payoneer request for payment
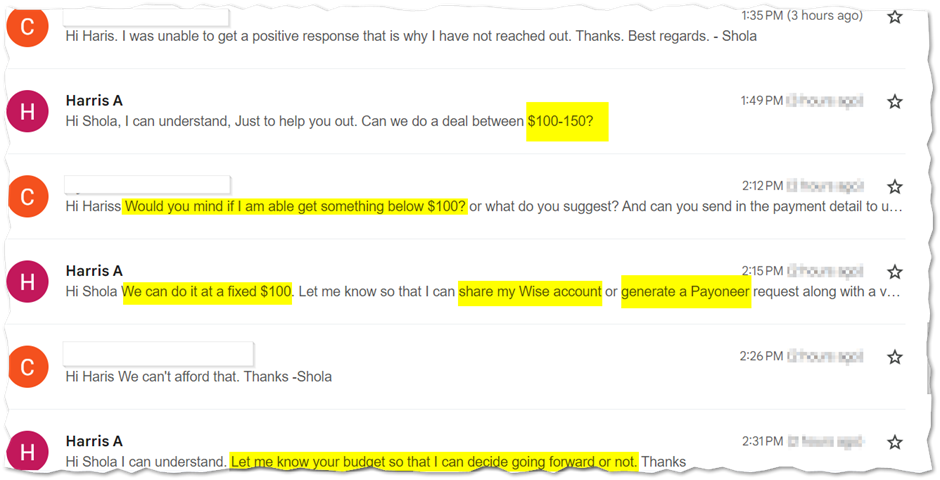
Here are a couple of what we observed –
- TA relies on the fear factor for the attempt to succeed.
- Lack of information about the website the TA is claiming he had found a vulnerability.
- Inconsistent email signature and name on the part of the TA over time
- Drastic cutdown of appreciation token cost! Pointing down to no criticality at heart in costing appreciation tokens.
- Email addresses targeted are mostly info, hello, support and general organizational inbox as they may apply to org. (Might have sent it to multiple email addresses waiting for those who will follow up)
- The focus was on the payment and not on the vulnerabilities he found (no single hint of what that could be all through the conversation)
- We have a feeling that only when you agree to commit to the payment TA will start scanning the website using an automated tool, just to present you with a report. Or at worst you might get a malware-laced document in return to compromise the recipient system.
- Replying to such emails can provide the TA opportunity to steal your organizational branding on the part of your email signature and others. Which can be used to further other social engineering campaigns.
- A true professional security advisor would have provided full contact details, mailing address and phone number of their consulting services.
On a good day, some cyber researchers might have something important to share with your organization but malicious TAs like this will scuttle their chances of being attended to as many might want to ignore such conversations and delete them from their inboxes.
Now that we can separate these red flags, we should give real researchers the chance to help us in the process.

Leave a Reply