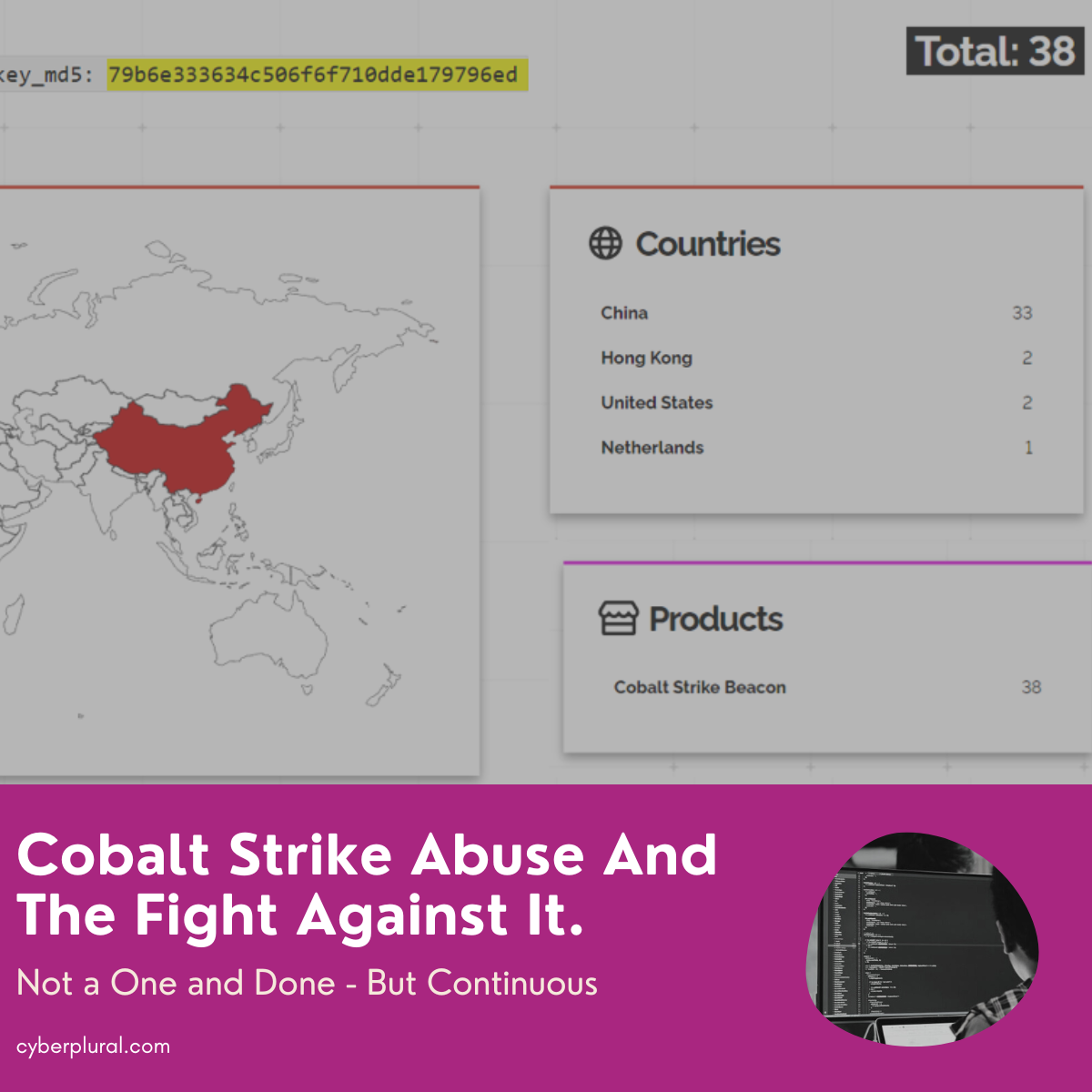
Just last week Microsoft’s DCU, Fortra and Health-ISAC moved to go legal and technical to disrupt cracked, legacy copies of Cobalt Strike and abused Microsoft […]
Category: Malware
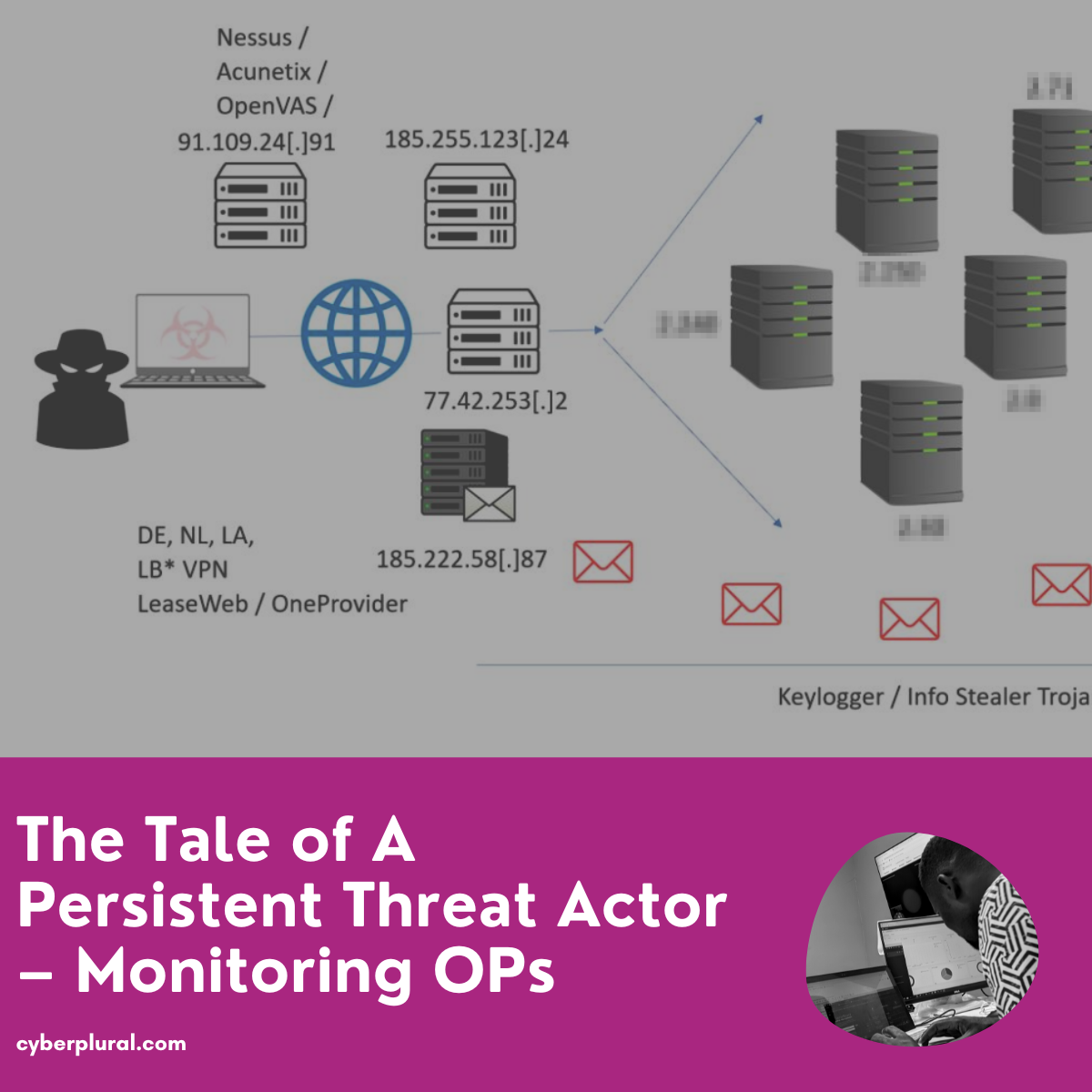
The Tale of A Persistent Threat Actor – Monitoring OPs
The benefit that comes with having visibility (proactive monitoring) in and around your organization’s network perimeter cannot be underestimated in cyber defense and understanding the […]
Crypto Stealer Campaign – Targeting Crypto Platforms Extension in Browsers
What an unbelievable event for this user, who became a victim of a crypto stealer campaign when a sum of $900 worth of USDT meant […]
Threats Targeting Linux-Based Multi-Cloud Environments
In this blog post, we will be looking at the VMware Threat Analysis Unit Report which is focused on exposing malware in Linux-based multi-cloud environments. […]
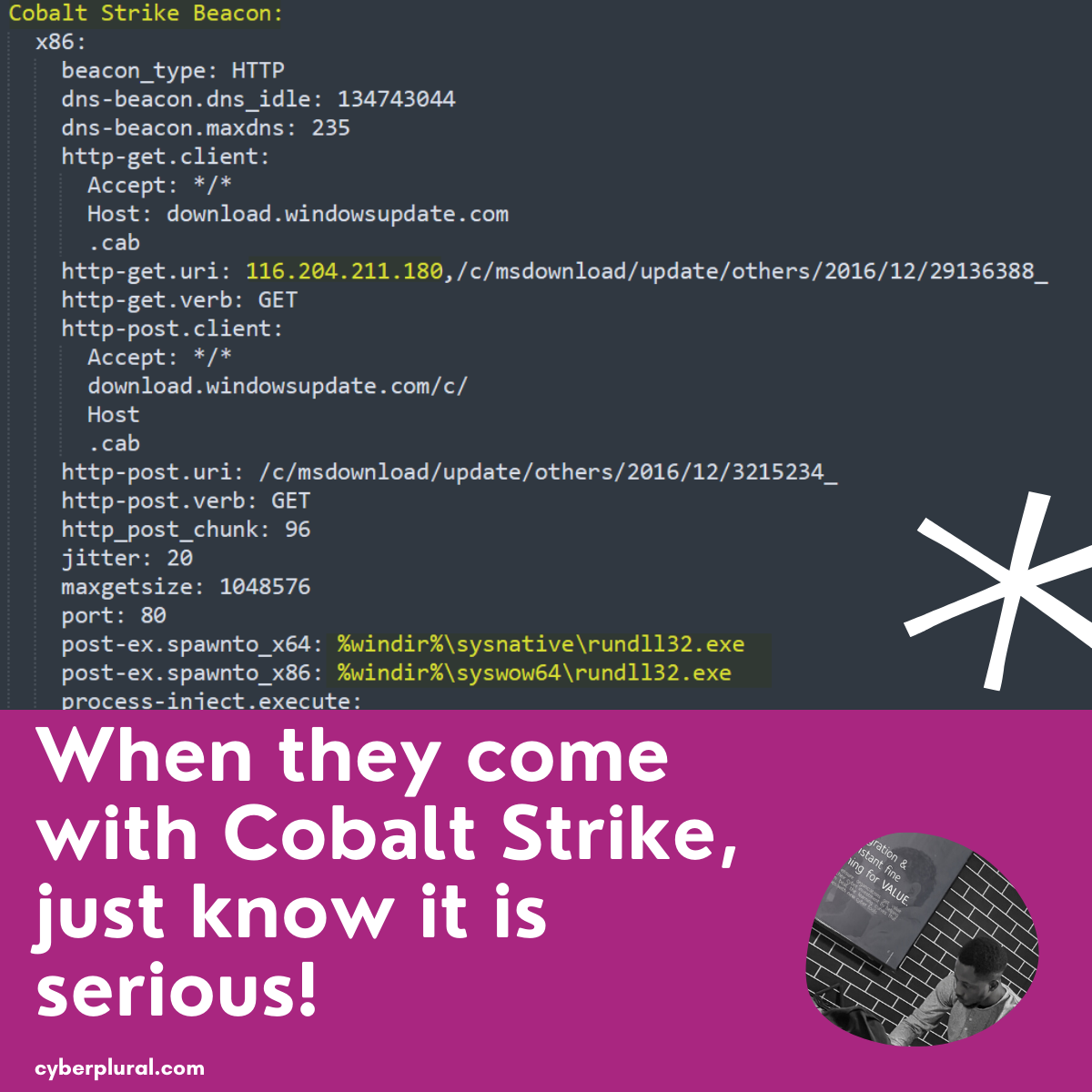
When they come with Cobalt Strike, just know it is serious!
A few weeks back we put out a tweet indicating there were an ongoing campaign targeting organisations’ networks in #Nigeria. This blog post will be […]
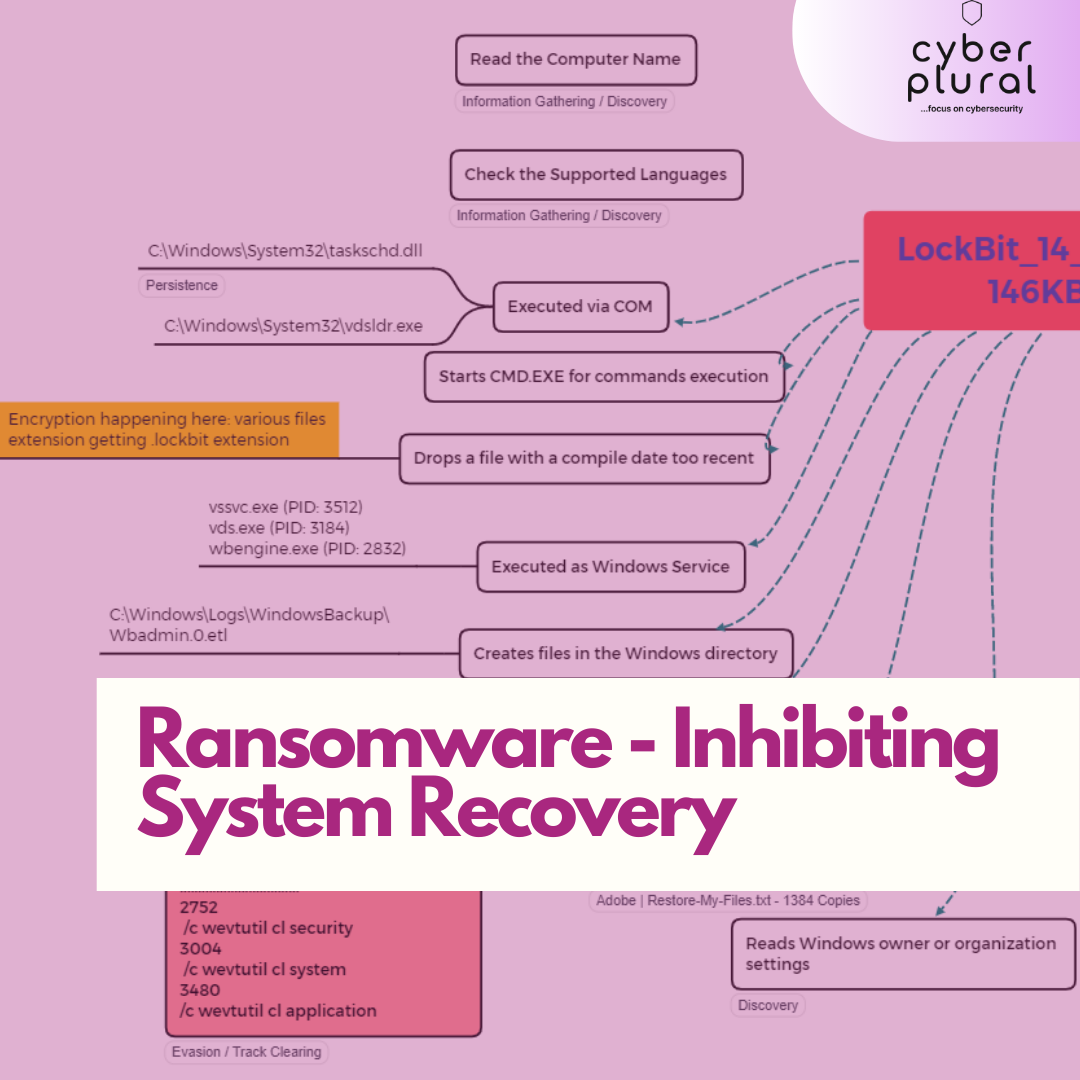
Ransomware – Inhibiting System Recovery.
We saw a lot of incidents that caught major headlines in 2021 to be ransomware. And not just that, many ransomware RAAS operators groups emerged […]