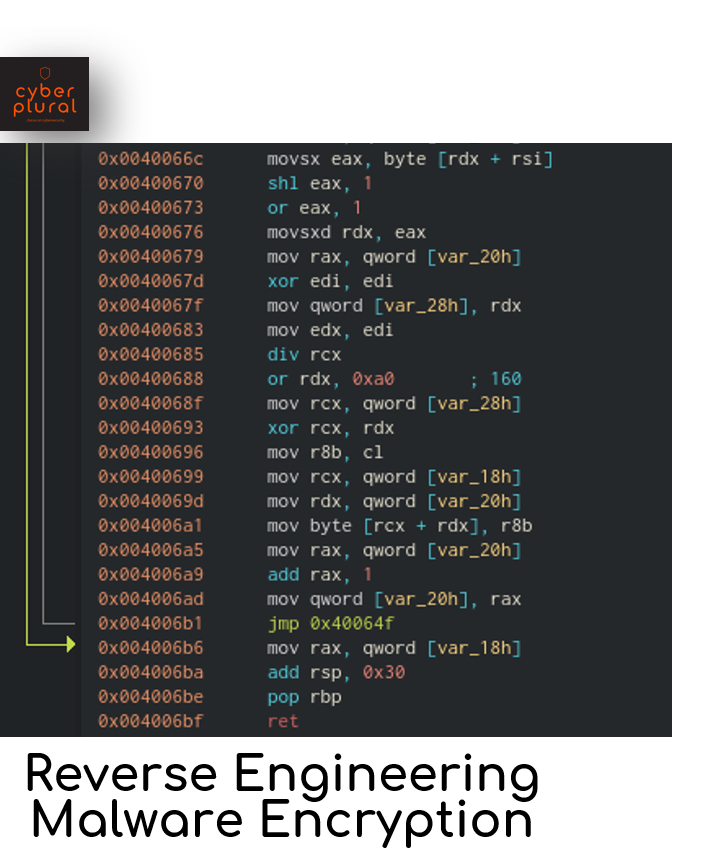
This is an analysis of the file malware201 in the RE101 reverse engineering challenge and the custom encryption algorithm it uses to hide strings. Though […]
Category: Malware
How Legacy Systems have become Soft Landing for Threat Actors.
A legacy VPN system gave access to the ransomware gang that breached Colonial Pipeline and made them pay a whooping sum of $4.4 million dollar […]
Defense Evasion – Malware In Bitmap
Defense Evasion consists of techniques that adversaries use to avoid detection throughout their compromise. Techniques used for defense evasion include uninstalling/disabling security software or obfuscating/encrypting […]
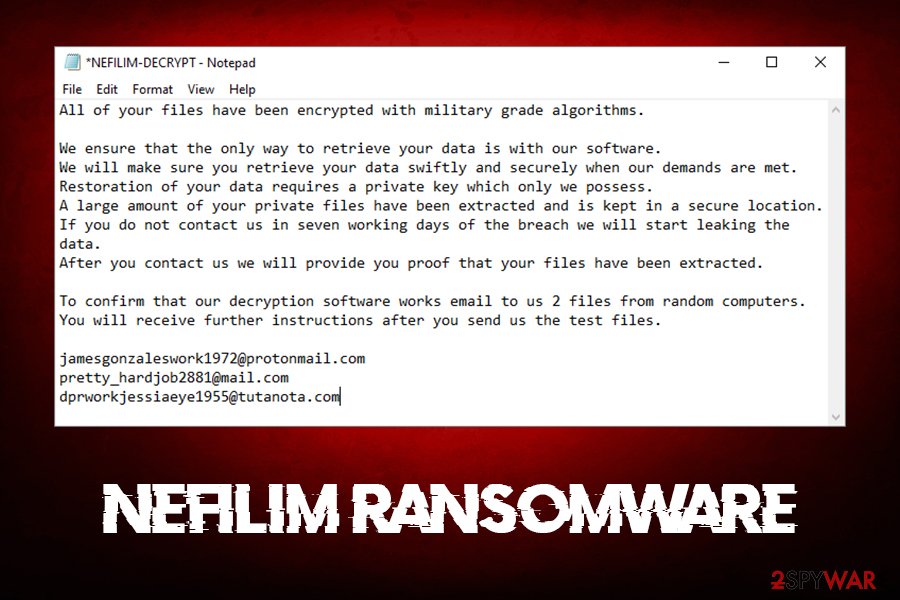
An Analysis of the Nefilim Ransomware From TrendMicro
Nefilim is among the notable ransomware variants that use double extortion tactics in their campaigns. First discovered in March 2020, Nefilim threatens to release victims’ stolen data to coerce them into paying the ransom. Aside from its use […]
Apple M1 Chip First Malware Discovered in the Wild
One of the first malware samples tailored to run natively on Apple’s M1 chips has been discovered, suggesting a new development that indicates that bad […]
A New Wormable Android Malware Spreading Through WhatsApp
A newly discovered Android malware has been found to propagate itself through WhatsApp messages to other contacts in order to expand what appears to be […]