The Tale of A Persistent Threat Actor – Monitoring OPs
The benefit that comes with having visibility (proactive monitoring) in and around your organization’s network perimeter cannot be underestimated in cyber defense and understanding the concept of normal and abnormal activities within your visibility context will always put the defense team a step ahead of the bad guys.
It is the case with the activities of the threat actor (TA) / group that our team observed for almost 3 weeks in the month of November. During this period (starting from the second week of November), our observations revealed the interest of the threat actor/group which was to gain initial access leveraging possible vulnerabilities on the Internet-facing assets. Other than just looking for vulnerabilities that could be leveraged, the threat actor/group was also pushing through social engineering. By sending phishing emails to some list of curated users within the target users’ space, which were found to contain info stealers malware (malware designed to steal user credentials on browsers, in files and generally all that could be found on the infected system) when analyzed.
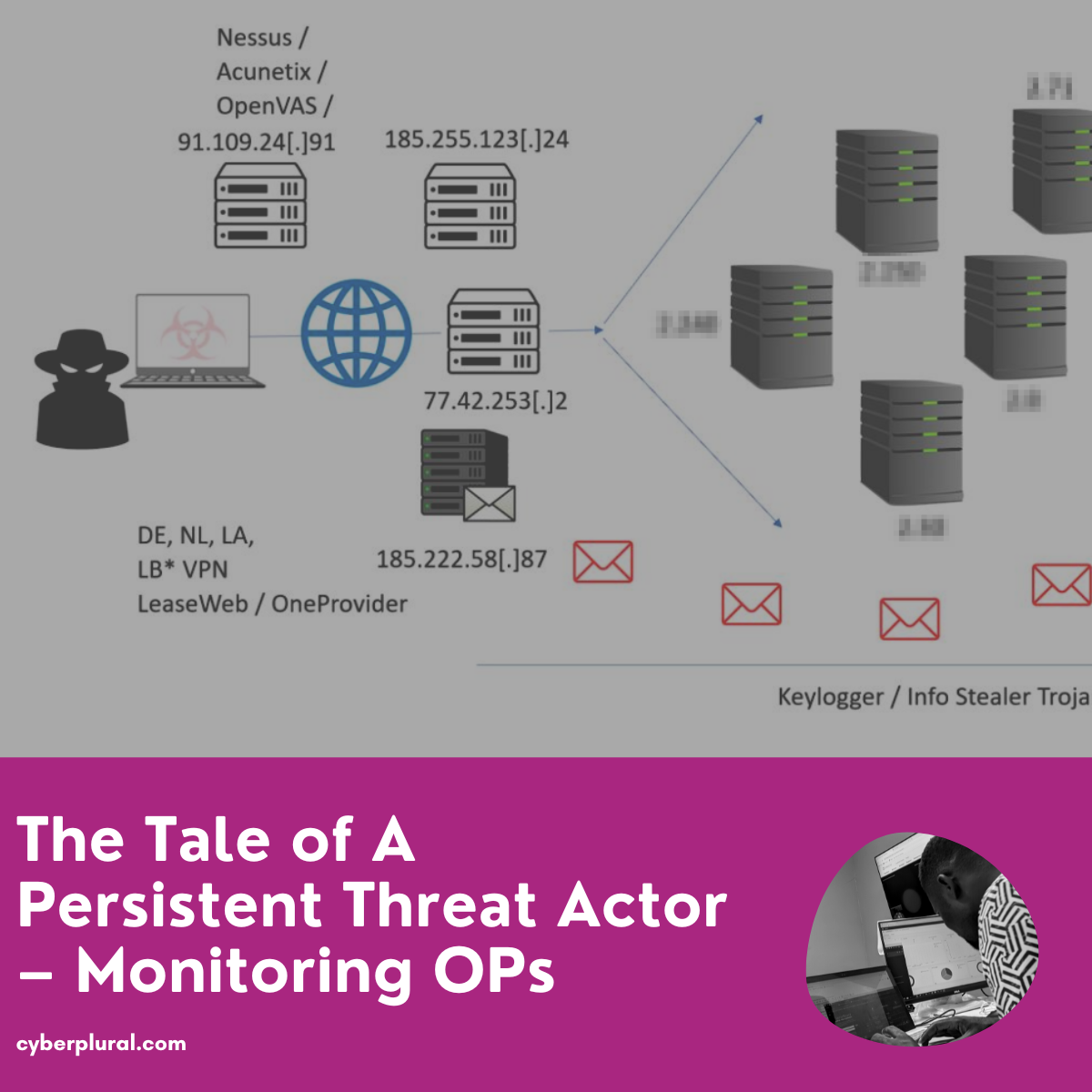
The monitoring OPs took a careful look at all activities in the first week and they started drafting what the attacker infrastructure might look like by trying to connect all related activities, alongside a possible tempo that might give out a trend to watch out for going forward.
Week One
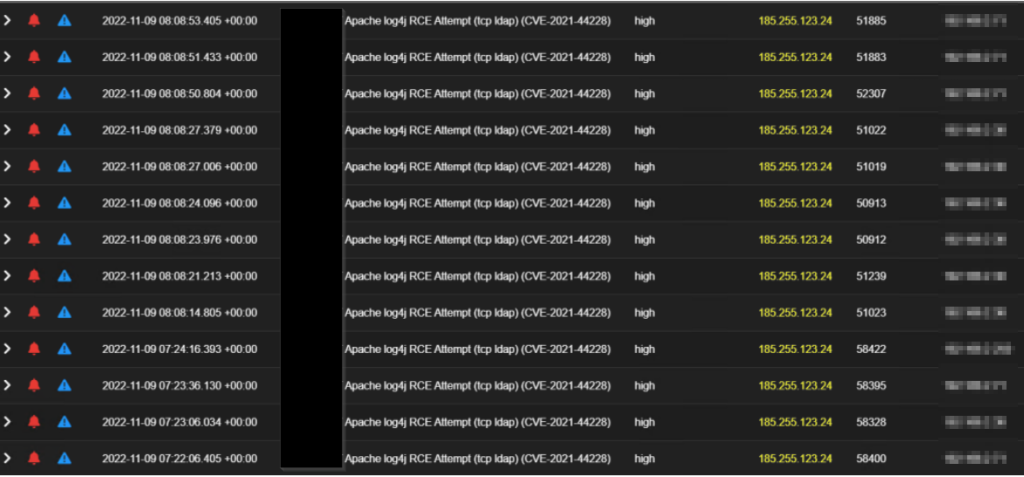
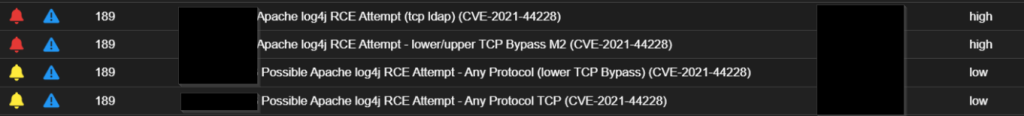
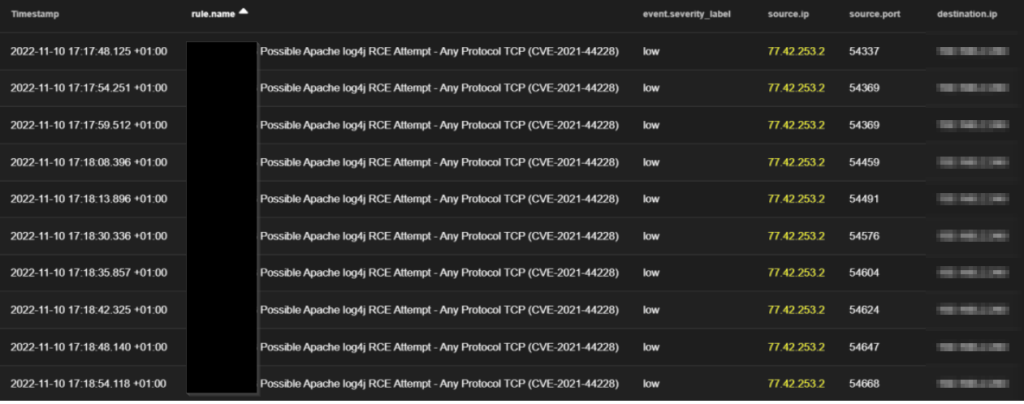
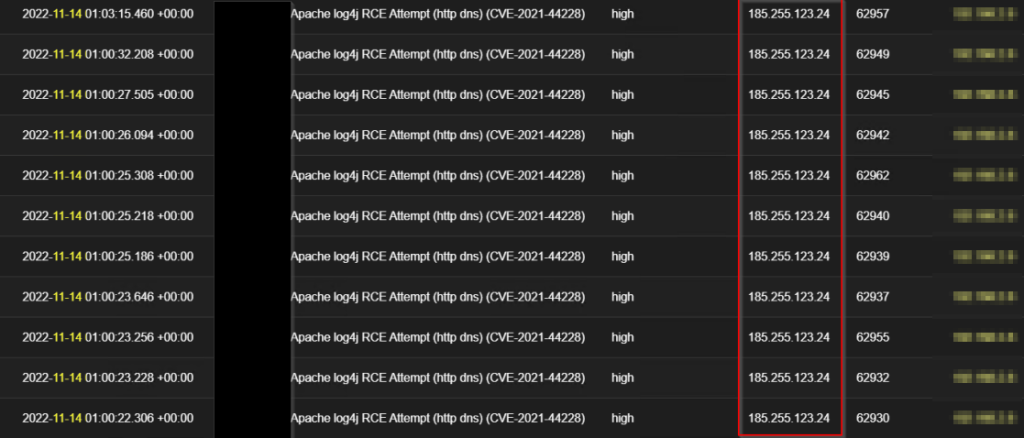
At first, we observed the following foreign IPs; 185.255.123[.]24 and 77.42.253[.]2 to be scanning and attempting exploitation of initial access vulnerabilities like Apache Log4j on some internet-facing servers, where it majorly focused on one server for persistent scan and attempts; where we noticed the TA to have been consistent with his attempt all through the week.
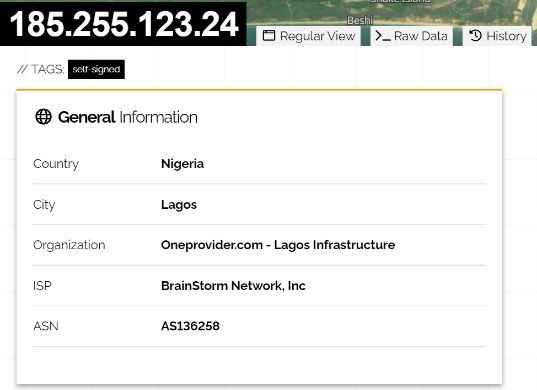
The most interesting thing with one of these foreign IPs is that it was indicating Nigeria as its origin when we decided to have a look into it, but we will tell you what the attacker was trying to do with that. We observed attacker brought part of its infrastructure closer to the target to remain undetected by leveraging cloud infrastructure with assets in Nigeria.
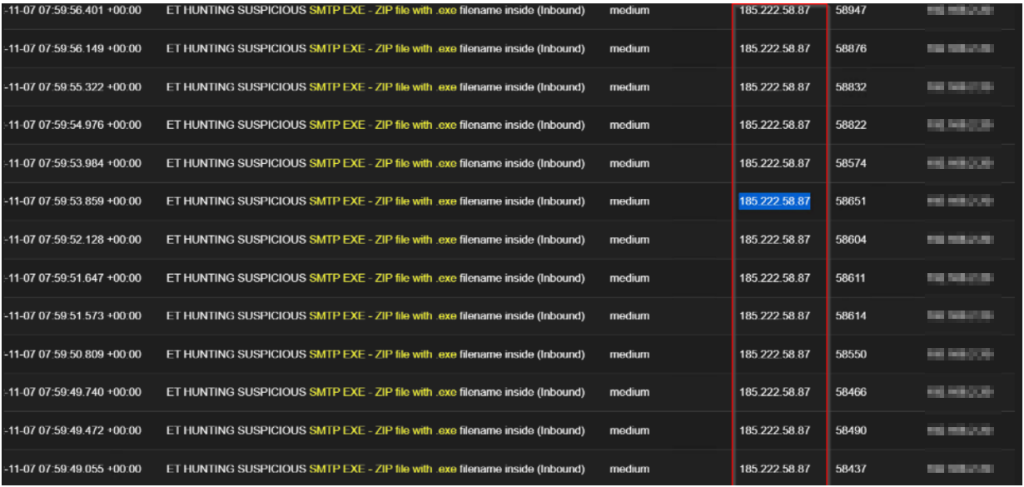
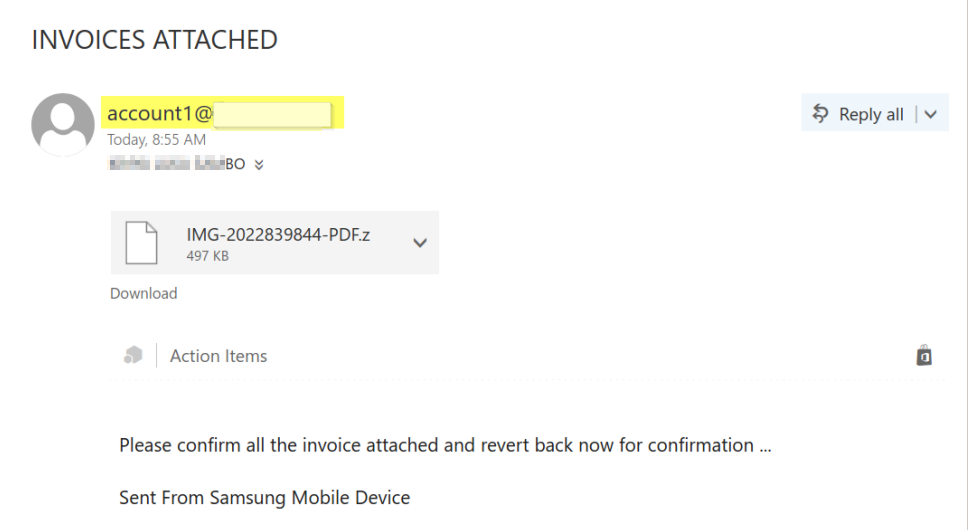
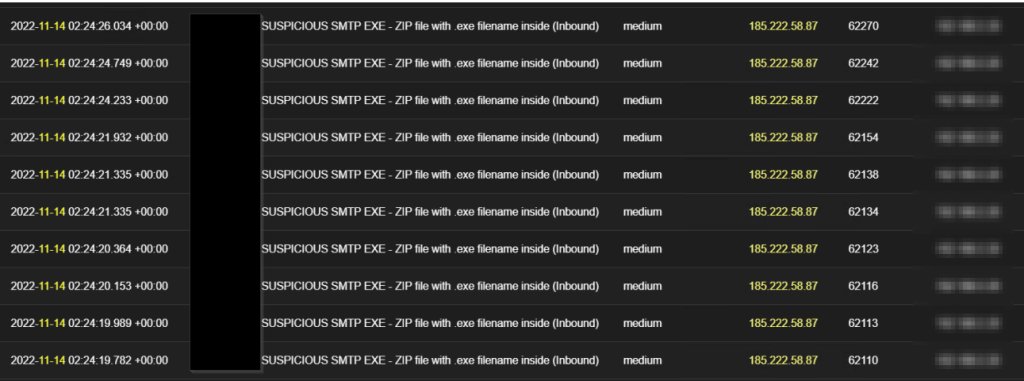
The first series of emails were received on the Monday 7th November 2022 the first week, where we observed this foreign IP 185.222.58[.]87 as captured in the image below to have sent suspicious attachments in a phishing email from info@target-org-domain to various users’ inbox (18 different users email received this email) as listed below.

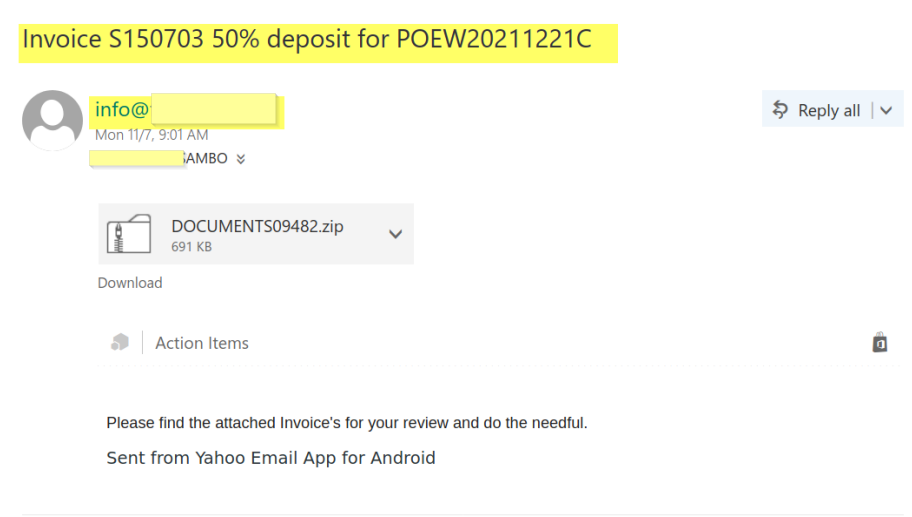
Here is what the first email looks like below.
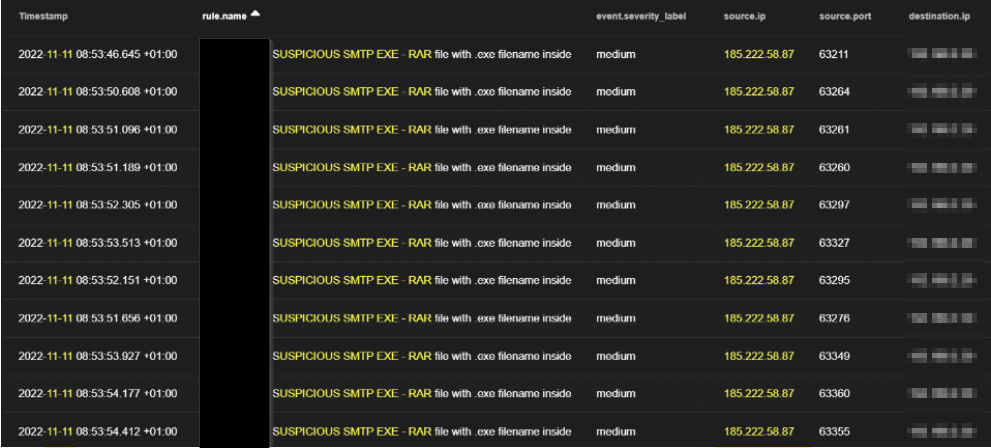
In the continuous effort to break in through social engineering, the TA also sent another series of emails on Friday 11th, November 2022 to the same set of users with different attachments this time coming from account1@target-org-domain, and from the same IP 185.222.58[.]87 as the one received on Monday.
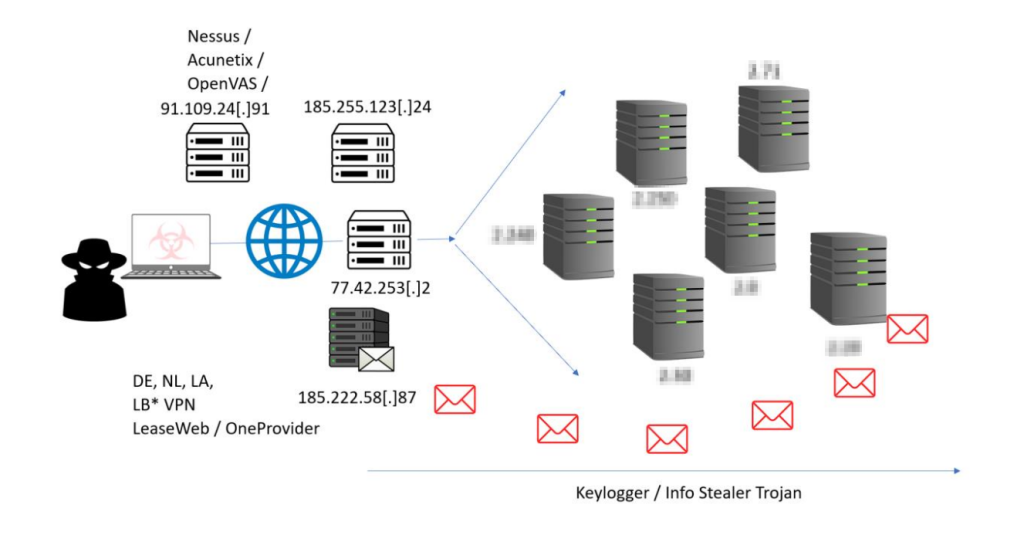
By the end of the first week, the Monitoring OPs have been able to perfectly come up with the draft of the threat group/attacker’s infrastructure using observation from close monitoring of the targeted environment as shown below;
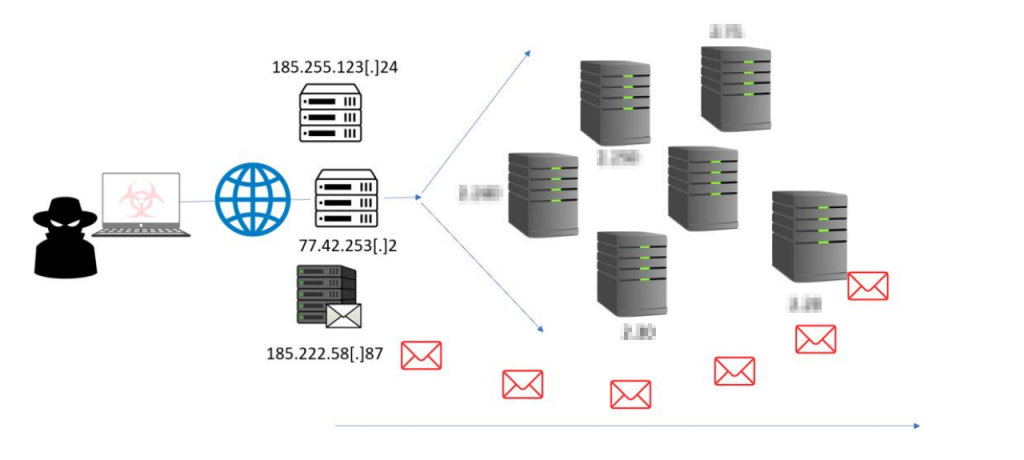
and the following hypotheses were also reached and the potential tempo drafted
- TA send email Monday and Friday (within the week)
- Scans and attempt exploitation throughout the week focusing on two servers majorly; scanning others as well.
- No scan on days emails were sent
- Brought part of its infrastructure closer to the target to remain undetected by leveraging cloud infrastructure with assets in Nigeria.
- A big infrastructure like this and the persistence might imply a bigger motivation and action on objectives on the part of the TA.
- Attachments in emails received were analyzed to understand the intent which was to steal credentials from any compromised users. Attachment comes in two extensions .RAR and .ZIP but both were found to be containing the same info stealer malware.
- The possible root cause of the invitation of TA towards the target already identified
- A necessary course of action (CoA) has been taken relating to the curated list of users the TAs was trying to get to through social engineering.
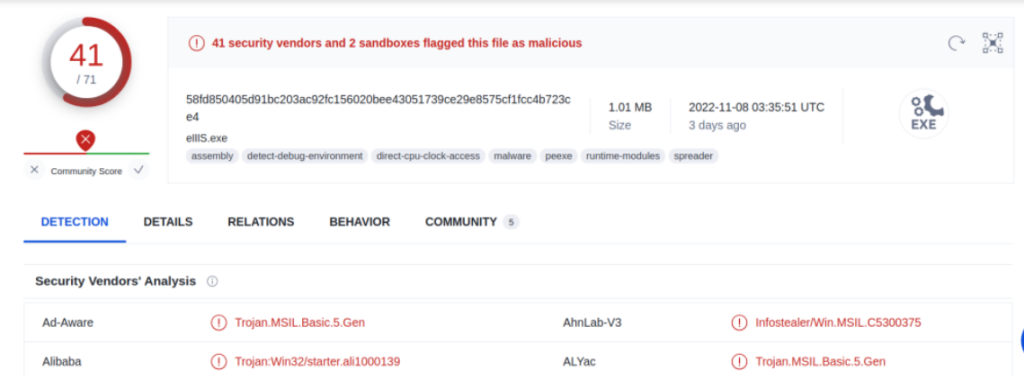
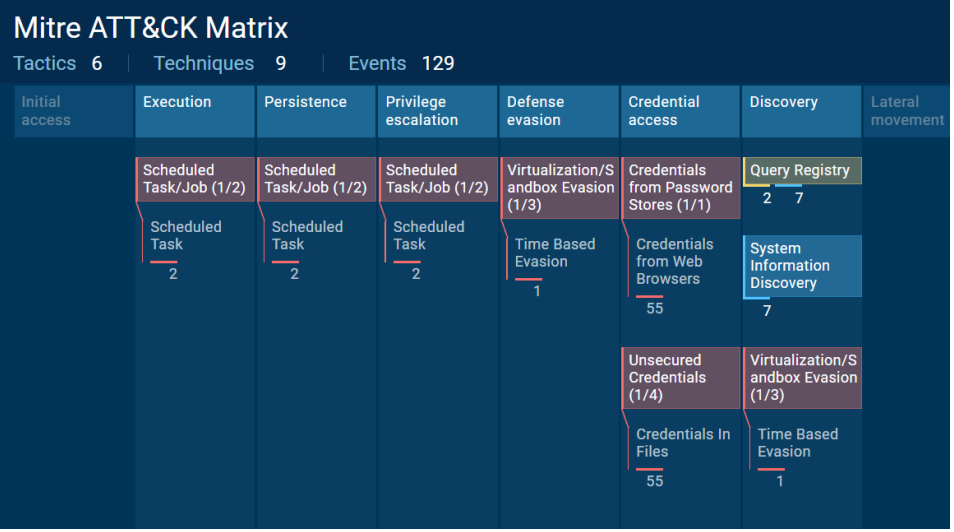
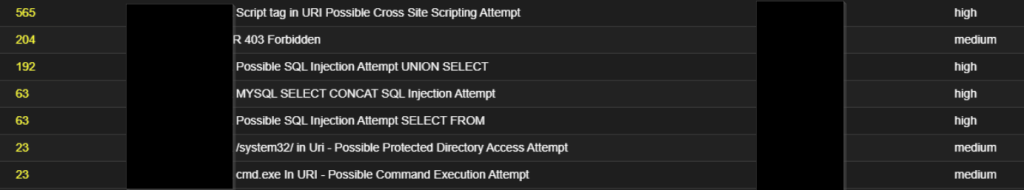
A glance through the dynamic analysis of the attachment using VT engines and attached is the ATT&CK matrix of behaviours
Into the Second Week
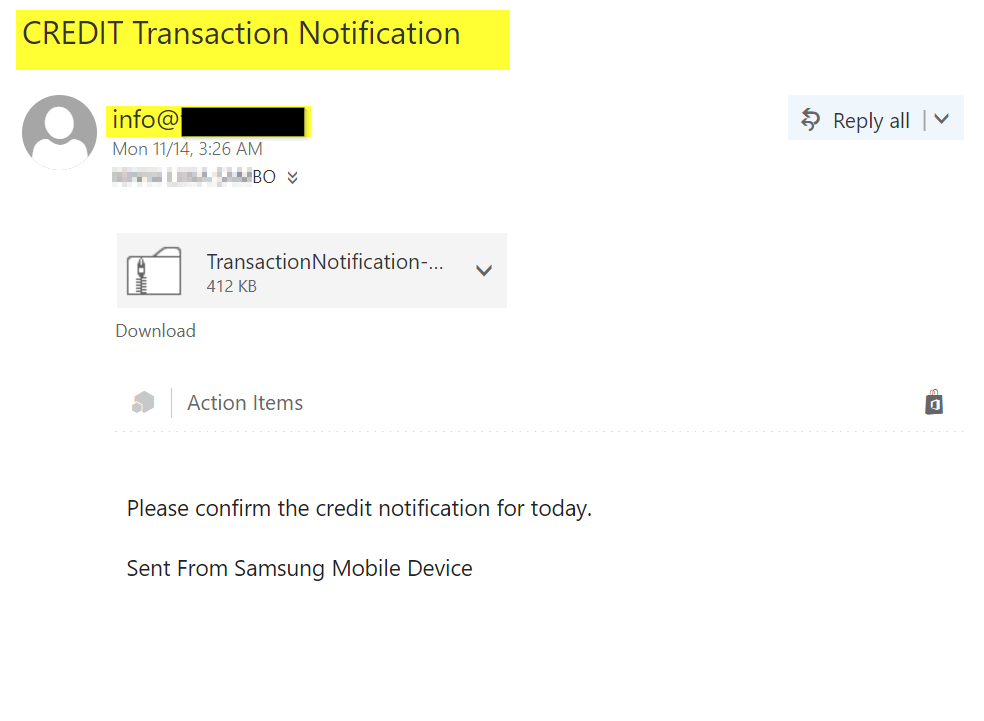
Jumping into the second week, we are already expecting to have an email on a Monday and it came in from the same IP responsible for emails from the TA’s infrastructure this time around using the info@target-org-domain again as it was from the first series of emails
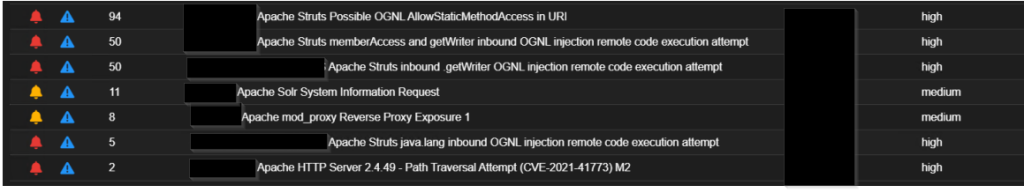
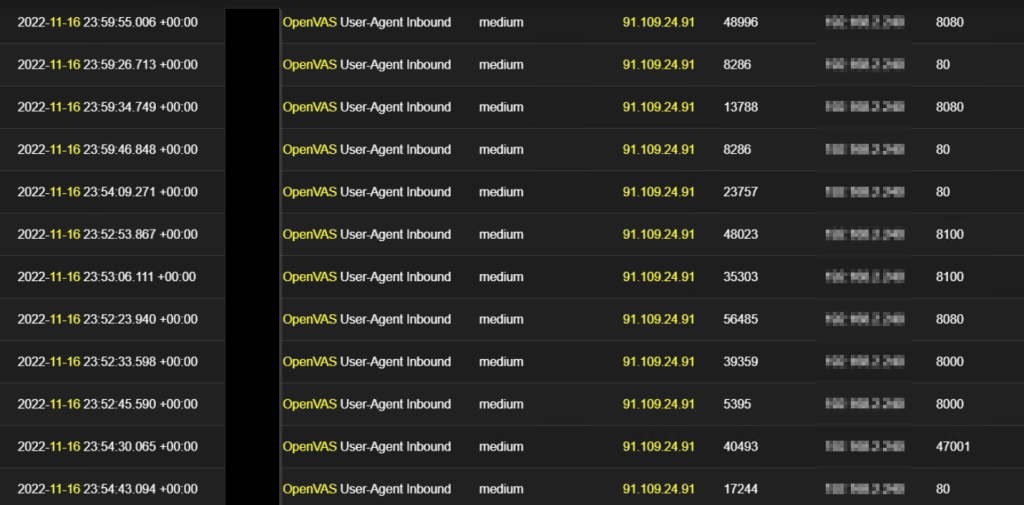
Along with this, the scan continues on Tuesday 15th November, where the TA was able to introduce another server to their infrastructure hosting series of web application scanners, network and host-scanning commercial tools such as Nessus, Acunetix and OpenVAS directed against the internet-facing server on the target org for related vulnerabilities such as Log4J and other web application attacks as shown below;
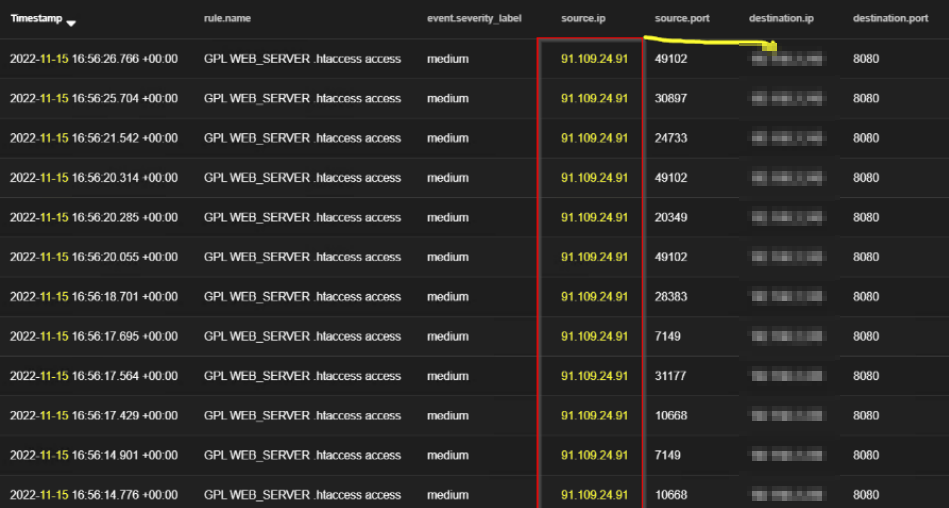
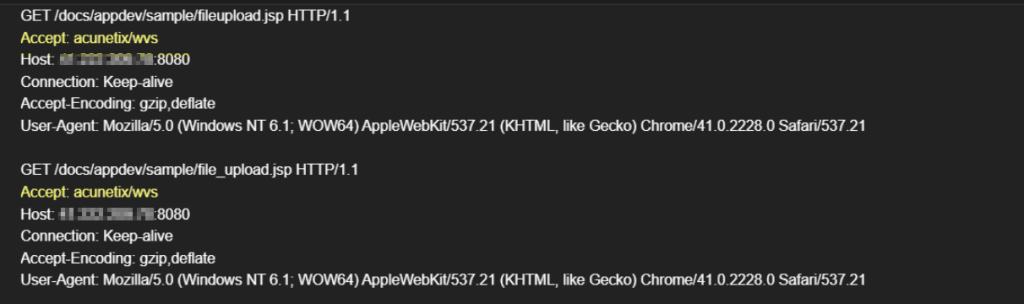
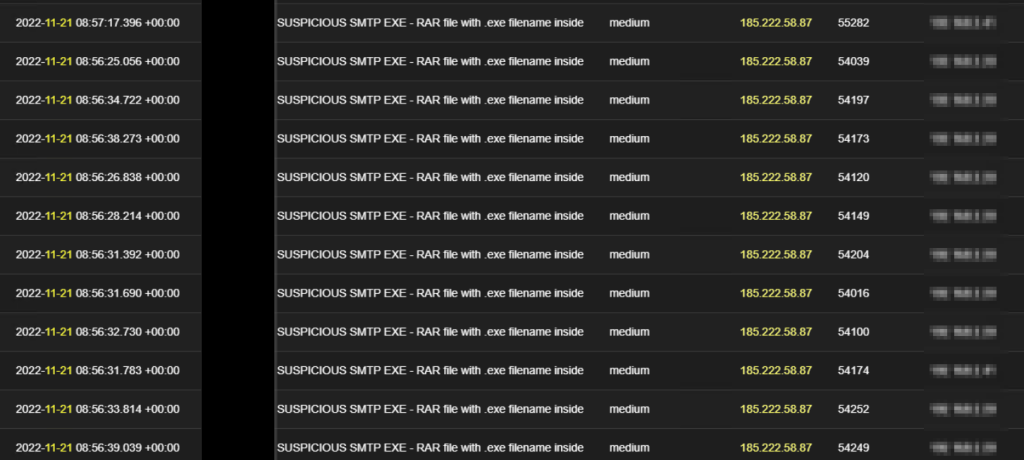
These scans also continue throughout the week and come with more intensity than what we were getting earlier as shown below; the tempo changed to email on interval + scans every day
but another email got in on Wednesday 16th November as captured below;
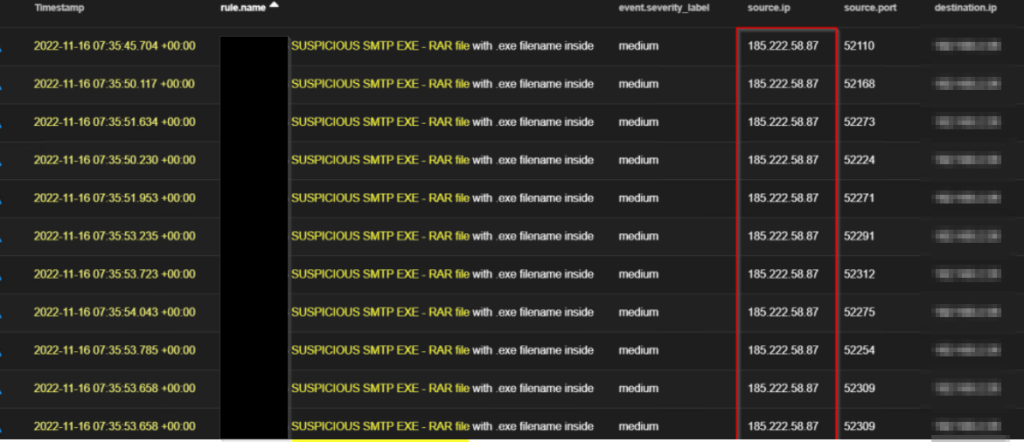
This email happened to be the first with a more official body structure and a different source domain other than the target-org-domain; indicating a possible change of mind for the TA with the hope that the previous email might not have been clicked because they look less official. But one thing that was still giving them away was that they were still coming from the server 185.222.58[.]87 responsible for email on their infrastructure and they all contain similar info stealer malware after being analyzed.
By the end of the second week, the Monitoring OP updated the attacker infrastructure draft they had by including the new server housing the commercial scanner tools and more information on this infrastructure has been identified
and the following hypothesis was also reached and the potential tempo drafted
- TA might want to re-strategize going forward as the phishing attempt is not working
- Look like TA is willing and has the budget to expand on infrastructure to get to their goal
- TA is intensifying activities for scan and using commercial tools to aid successful recons.
- Possibly Human-Driven and targeted
- All attachments in all new emails after being analyzed remain to be the info stealer malware just change of name
- Most of what we hypothesised in the first week was validated going forward during analysis and with new observations.
What happened in Week Three
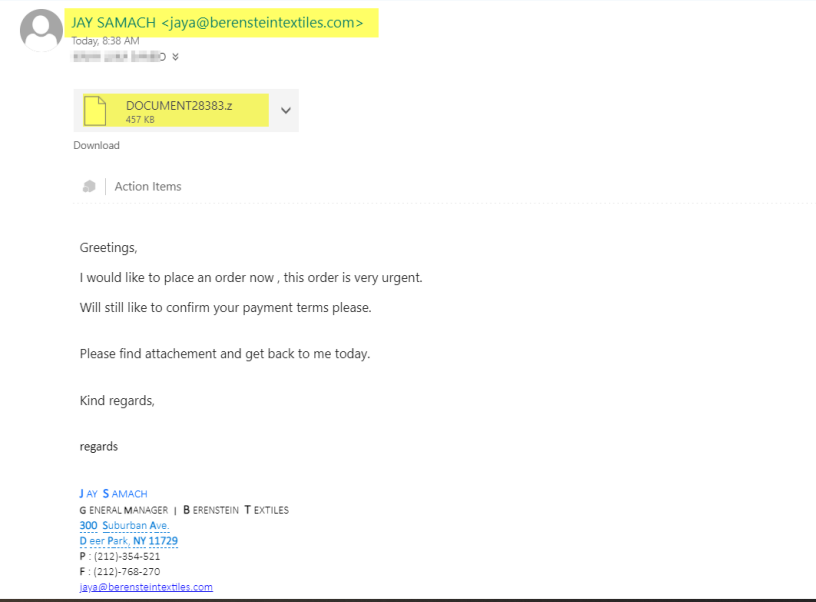
Then we jumped into Week Three where we got our first email, also came in an official body structure as shown below.
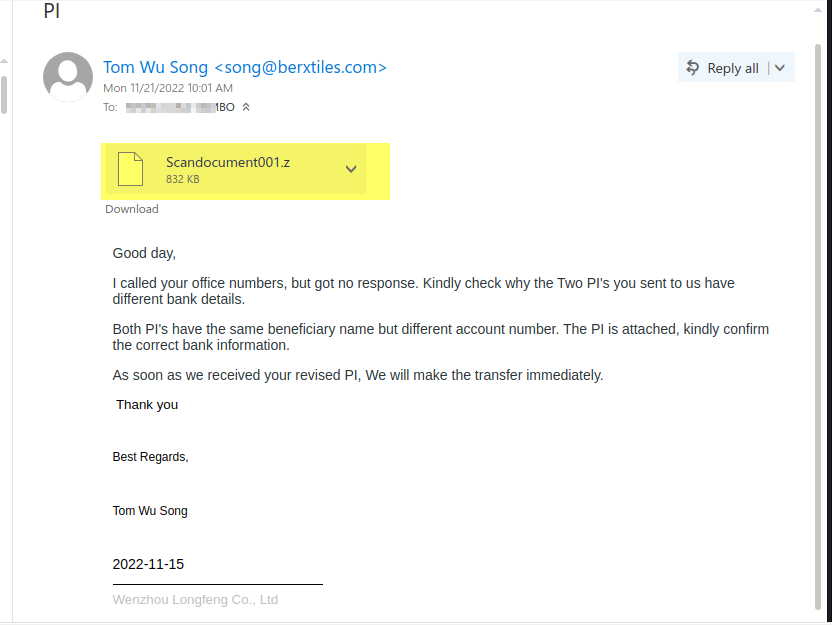
We watched the scans fade away in the third week as well as the tempo of the email just concentrating now on a single email and eventually the TA stopped sending (possible withdrawal for an easy target or planning a better kill chain that will work). This pushes our team into the watching phase to ensure we are not caught up with any surprises with whatever the re-strategized plans of the TA might be.
In conclusion, we have succeeded in frustrating the threat actor/group after watching them suffer for the past three weeks scanning and sending emails to the mostly retired inboxes as contained in the report.
Indicator of Compromise (IOC)
185.255.123[.]24
77.42.253[.]2
185.222.58[.]87
IMG-2022839844-PDF.z | INVOICES ATTACHED
DOCUMENTS09482.zip | Invoice S150703 50% deposit for POEW20211221C
Scandocument001.zip | PI
DOCUMENT28383.zip | URGENT ORDER
TransactionNotification-pdf.zip | CREDIT Transaction Notification
9b56161c9f937a22c8e27b5243dbf837 (MD5)
80c54c8308d7819d4620f84ffc14c8c3 (MD5)
58fd850405d91bc203ac92fc156020bee43051739ce29e8575cf1fcc4b723ce4 (SHA256)
3d06cd1430771df1de9948c5f1e0b75eb9f8fe61fe2d7765ddaf916e8d59950c (SHA256)
95f56fb182812795848d78ba412d42c76ee717945a57b0389b24e53e6fbbee04 (SHA256)
Snake Keylogger [Info Stealer]
132.226.247[.]73:80 (TCP), 158.101.44[.]242:80 (TCP), 20.99.133[.]109:443 (TCP)
23.216.147[.]76:443 (TCP)
http://checkip.dyndns[.]org/
https[:]//api.telegram[.]org/bot5387999448:AAENk6Reb2hxJqqD2rN6fIet7kanu0isfWg/se
ndDocument?chat_id=1413074050&caption=%20Pc%20Name:%20WALKER%20|%20Sna
ke%20Keylogger%0D%0A%0D%0APW%20|%20WALKER%20|%20Snake
9e8575cf1fcc4b723ce4/behavior

Leave a Reply