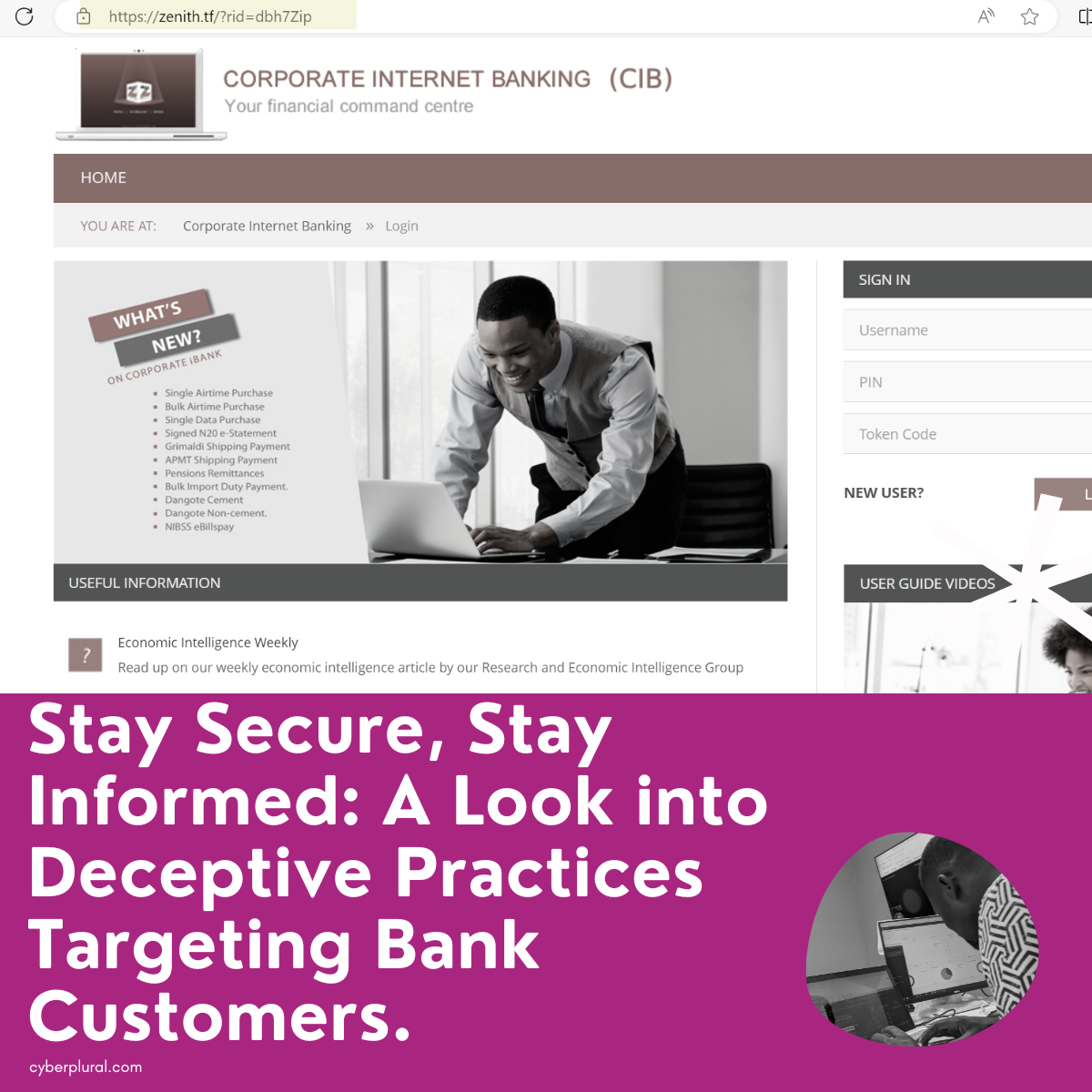
In the current landscape of digital banking, a concerning trend has emerged that puts account holders at risk of falling victim to sophisticated cyber scams. […]
Category: Cyber Attack
Anonymous Sudan Launches Cyberattacks on Nigeria’s Vital Information Systems
On August 1, 2023, Anonymous Sudan announced on their Telegram channel that they would be launching cyberattacks on Nigeria’s vital information systems. This announcement was […]
2023 | Q2 Report – Incident Reports, Major CVEs & Threat Intel
Our 2023 Q2 Report speaking to incident reports, major CVEs and threat intel is here again. In this report, we have The report summarizes the […]
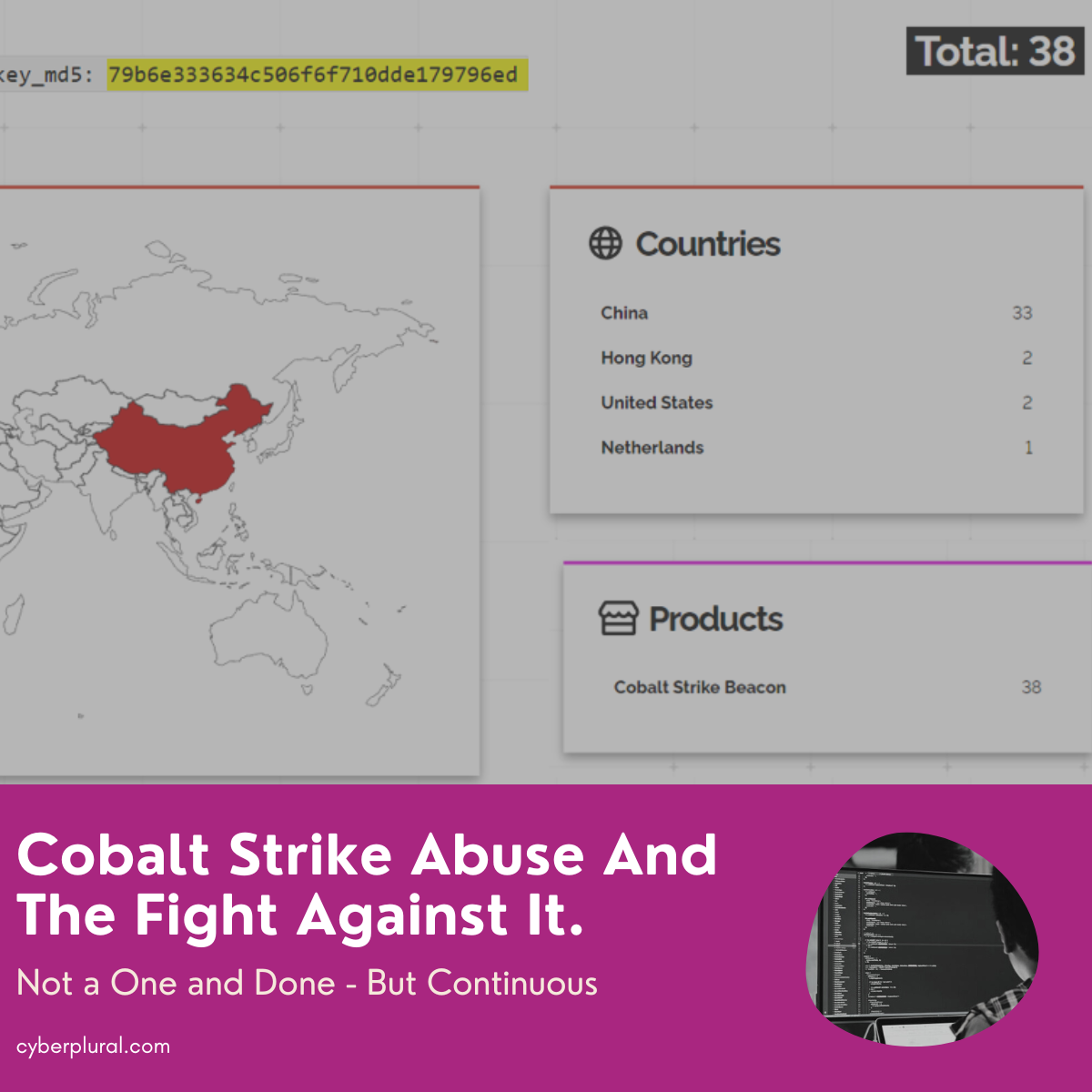
Cobalt Strike Abuse And The Fight Against It
Just last week Microsoft’s DCU, Fortra and Health-ISAC moved to go legal and technical to disrupt cracked, legacy copies of Cobalt Strike and abused Microsoft […]
Incident Reporting – A Major Concern in the Africa CyberThreat Assessment Report 2023 by Interpol.
Having taken a thorough look at the African Cyberthreat Assessment Report 2023 by Interpol’s African Cybercrime Operations Desk with data drawn from Interpol’s member countries […]
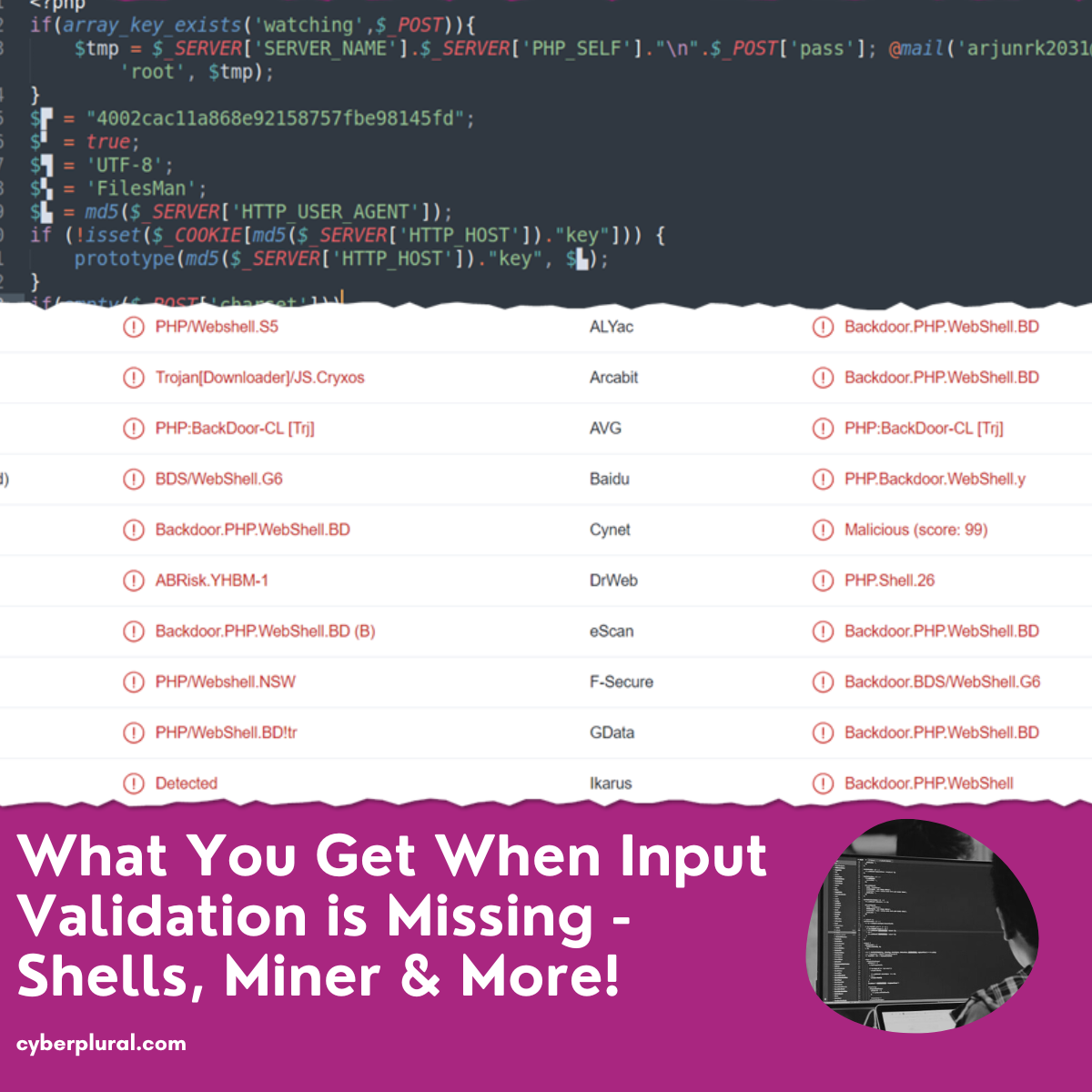
What You Get When Input Validation is Missing – Shells, Miner & More
Web applications and software frequently need user interaction to function properly. Users must be able to provide their email addresses and other personal information at […]