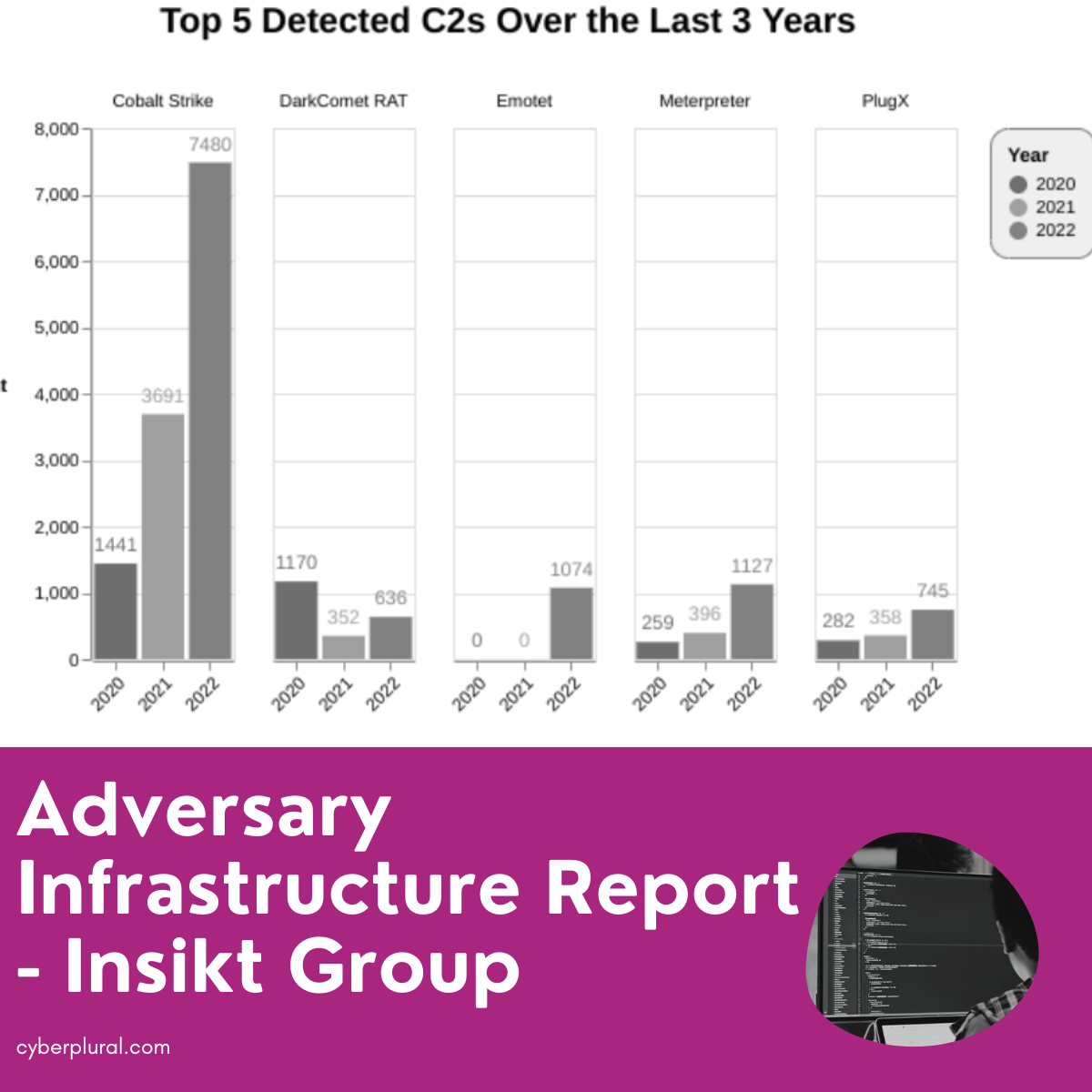
Insikt has released her 2022 Adversary Infrastructure Report. The report is based on its findings on the development of new harmful infrastructure for a variety […]
Category: Cyber Attack
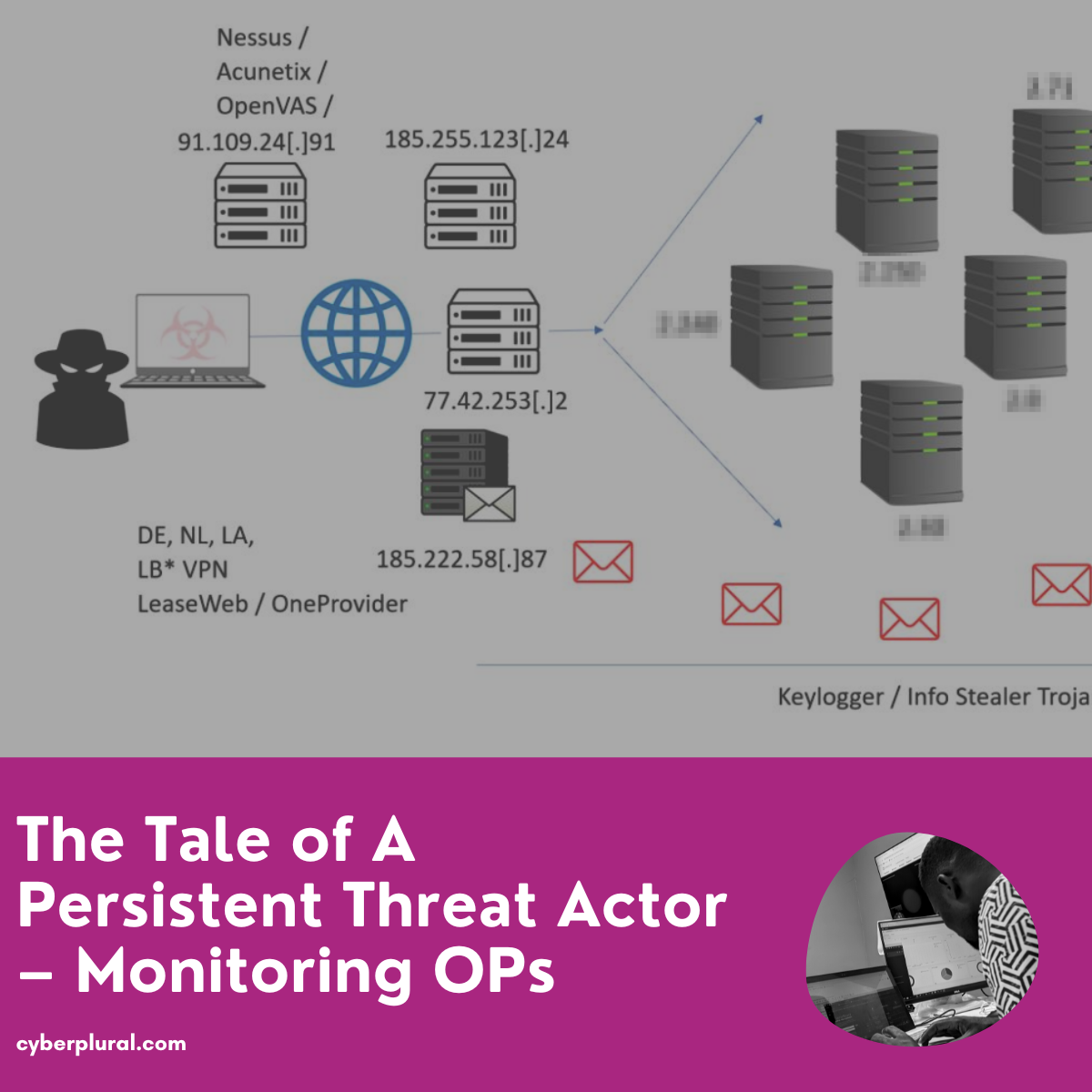
The Tale of A Persistent Threat Actor – Monitoring OPs
The benefit that comes with having visibility (proactive monitoring) in and around your organization’s network perimeter cannot be underestimated in cyber defense and understanding the […]
Crypto Stealer Campaign – Targeting Crypto Platforms Extension in Browsers
What an unbelievable event for this user, who became a victim of a crypto stealer campaign when a sum of $900 worth of USDT meant […]
Phishing Campaign Leveraging IPFS
Certain threat actors or groups are now going around with phishing campaigns targeted at businesses /organizations in Nigeria. The interesting thing about this campaign is […]
2022 | Q2 Report – Lessons Learnt
Our 2022 | Q2 Report takes a look at the #lessons learnt from significant #cyber incidents reported in this quarter, reported CVEs and Threat #Intel and what we can do better […]
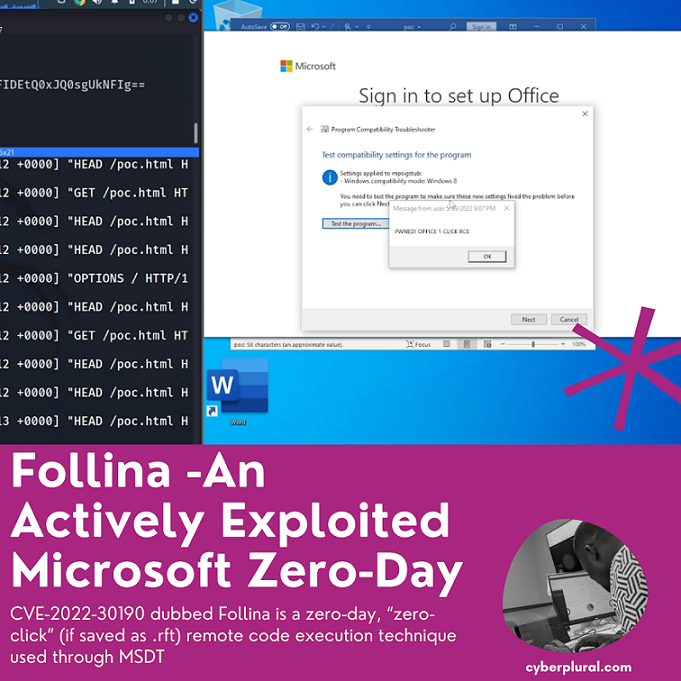
Follina – An Actively Exploited Microsoft Zero-Day
CVE-2022-30190 dubbed Follina is a zero-day, “zero-click” (if saved as .rft) remote code execution technique used through MSDT (Microsoft Diagnostics Tool) and Microsoft Office utilities […]