Phishing Campaign Leveraging IPFS
Certain threat actors or groups are now going around with phishing campaigns targeted at businesses /organizations in Nigeria. The interesting thing about this campaign is how the threat actor hosted their novel script that will harvest unsuspecting users’ credentials on IPFS.
For many who might be hearing of IPFS for the first time, let us find out what it is.
IPFS stands for InterPlanetary File System, it is a peer-to-peer hypermedia protocol designed to host data from multiple nodes at once enabling substantial bandwidth saving. In simple terms, IPFS power the distributed web, and content can be moved around using content id (CID) and other peers can find and request the content from any node that has it using a distributed hash table (DHT).
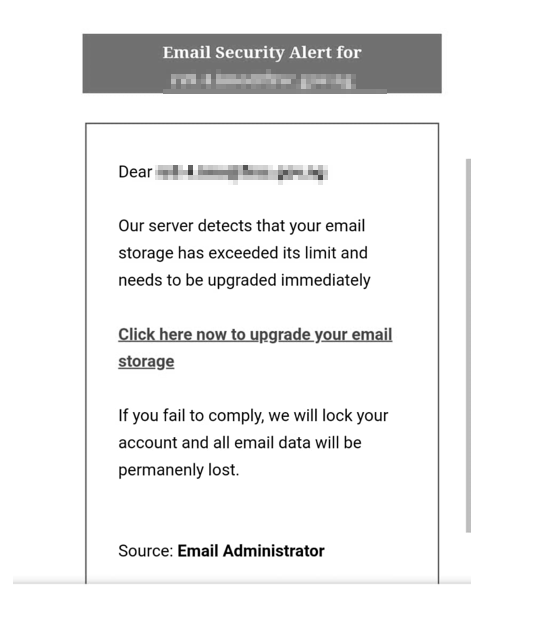
The Threat Actor (TA) was able to deliver the email to the target and a sample of the email is shown below,
The hyperlink in the email body reveals is pointing to this address you have below
What we observed is that when you supply any email address with the domain at the back where we have the hash (#) sign, you get the platform to load the organization’s website in the background and automatically fit in the logo to make it more believable to unsuspecting users at the sign-in box as shown below.
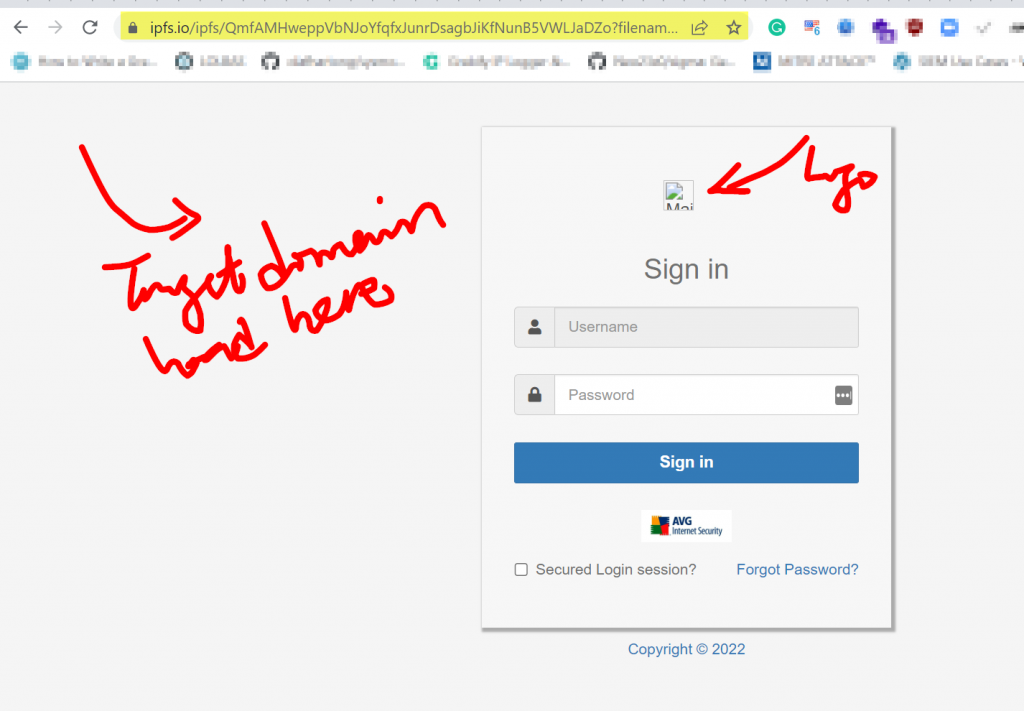
Breaking down the URL, you can be able to see the following:
Seated on –
Content ID on IPFS
/ipfs/QmfAMHweppVbNJoYfqfxJunrDsagbJiKfNunB5VWLJaDZo?
Malicious Script Running for the Campaign –
filename=kelvoblaze.html
Supplied Email from an Organization Domain (Target)
#target_user@target_domain
Hours later, we observed the attacker had removed the content from the CID on IPFS and the phishing script is no longer available as shown below.
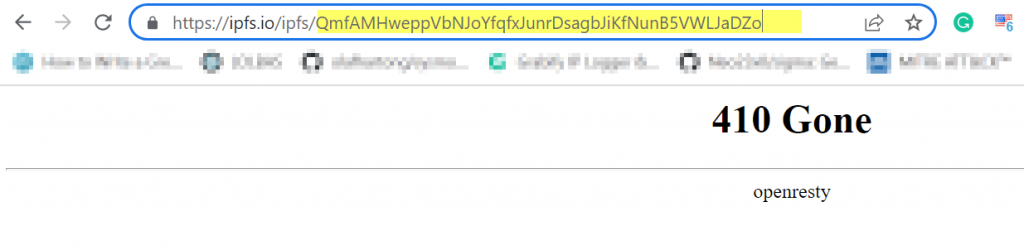
With the IPFS, that means the Threat Actor can always move around the malicious script by placing it on a new content ID (CID) or multiple CID can be hosting them at the same time while targeting different organizations.
IPFS makes malicious content like phishing pages take down harder. When it only requires reporting a phishing page to a hosting company or a DNS provider to have it shut down when it is stored on the usual web, it requires addressing all IPFS gateways which leads to the fraudulent content to have it shut down.
We should expect to see more of this abuse due to its advantage to the attackers, and organizations should also take the appropriate course of action to ensure malicious emails are not able to get to their users in the first place, and appropriate awareness about this type of tactics.

Leave a Reply