Adversary Infrastructure Report – Insikt Group
Insikt has released her 2022 Adversary Infrastructure Report. The report is based on its findings on the development of new harmful infrastructure for a variety of post-exploitation toolkits, custom malware, advanced persistent threat (APT), botnet families, open-source remote access trojans, as well as the modification of existing malicious infrastructure (RATs), and other commodity tools.
Reduction in notification downtime in the identification of a malicious command-and-control event can proactively improve defenders’ response to threats. Before a C2 server can be activated, threat actors have to either compromise or acquire a legitimate infrastructure, register a domain (if required), install and configure necessary software including TLS if applicable, and add files to the server. Also, the TA will have to access the server via SSH or RDP and expose the malware controller to a port to allow data transfer to the victim and administer commands to infections. (Although, additional action may be required depending on the operation).
However, during setup, installation and access of the server, the TA leaves artefacts that are observable prior to using the server to conduct a phishing campaign or any malicious intent.
These artefacts include software versions, login panels, TLS certificate patterns, etc. which provide detection opportunities for defenders.
Detecting C2 servers from creation to weaponization brings insight into how adversaries carry out malicious campaigns.
This includes:
- Comparing C2 detections to reports of intrusions related to those families can identify how many intrusions are caught and potentially how many events remain unknown in the public domain.
- Measuring the tempo of server creation can provide insight into forthcoming surges or drawdowns of activity
- Capturing indicators and intelligence otherwise unavailable in the public domain
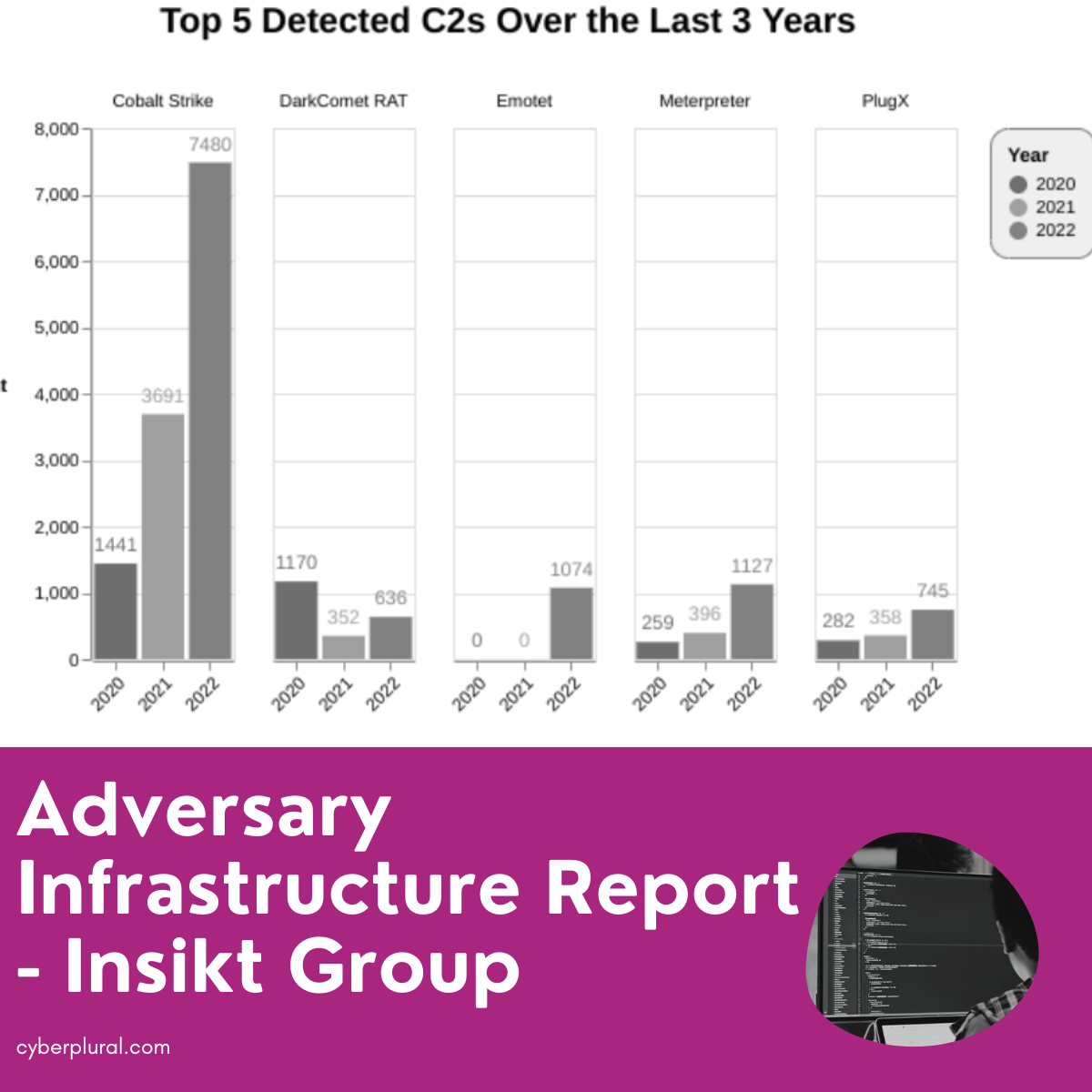
Inskit identifies the top 5 C2 families over the last 3 years including (Cobalt Strike), remote access tools/backdoors (PlugX, DarkComet), and botnets (Emotet).
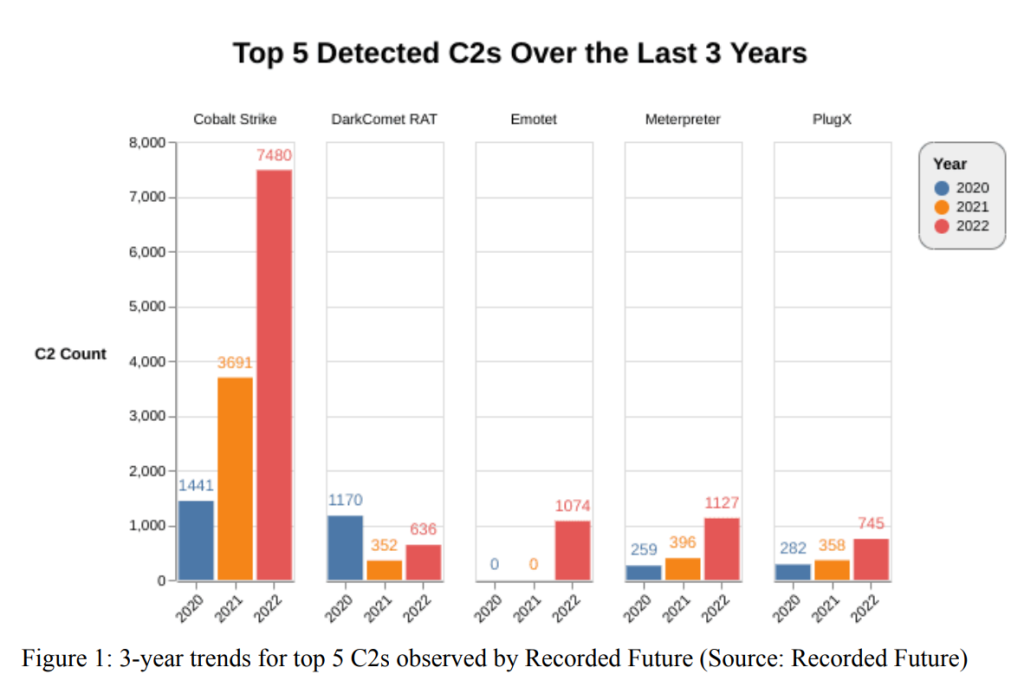
The number of C2s that Insikit detected for tools outside of the top 5 and top 20 increased significantly this year. Most of the rise may be attributed to a wider range of actors using “established” tooling like PlugX, Remcos, DarkComet, and QuasarRAT. The top 6 tools in our
data collection that had an increase in usage between 2021 and 2022 were as follows
- PlugX (51% increase)
- Remcos (51% increase)
- DarkComet (44% increase)
- QuasarRAT (40% increase)
- Mythic (33% increase)
- AsyncRAT (24% increase)
Inksit made the comment that the widespread usage of commodity tools may be a sign that a growing number of threat actors prefer to blend in and be untraceable to being undetected, or that they have simply decided that their targets are unlikely to notice even these widely used tools.

Leave a Reply