Ransomware – Inhibiting System Recovery.
We saw a lot of incidents that caught major headlines in 2021 to be ransomware. And not just that, many ransomware RAAS operators groups emerged from the dark web community hereby hitting up the competition between these different threat actor groups, and TTPs were seen to be more prevalent and targeted throughout the year.
The beginning of 2022 sees the arrest by law enforcement of gang members of a prominent ransomware group whose activities throughout 2021 shocked the world as a big player in that space, through national collaborations, and this is expected to bring more deterrence to other players in the field, although we have new gangs coming up with new names which several researchers claimed as just rebranding approach to those old names we know as operators are found to still be from retired/abandoned / shutdown groups.
Aside from encryption of files and making them unreadable for victims, ransomware is also designed to first inhibit system recovery of the victim system. Such that going back in time to restore such affected system will not bring the files back unless a ransom is paid which is also not certain, as the double-extortion scheme is now a tactic and MO of Ransomware Groups.
Dynamic Analysis
Here is a look into a ransomware sample to understand this context of identifying the malicious activity, investigating the threat and aiding containment and removal; according to the sample analyzed dynamically and statically, we observed the following;
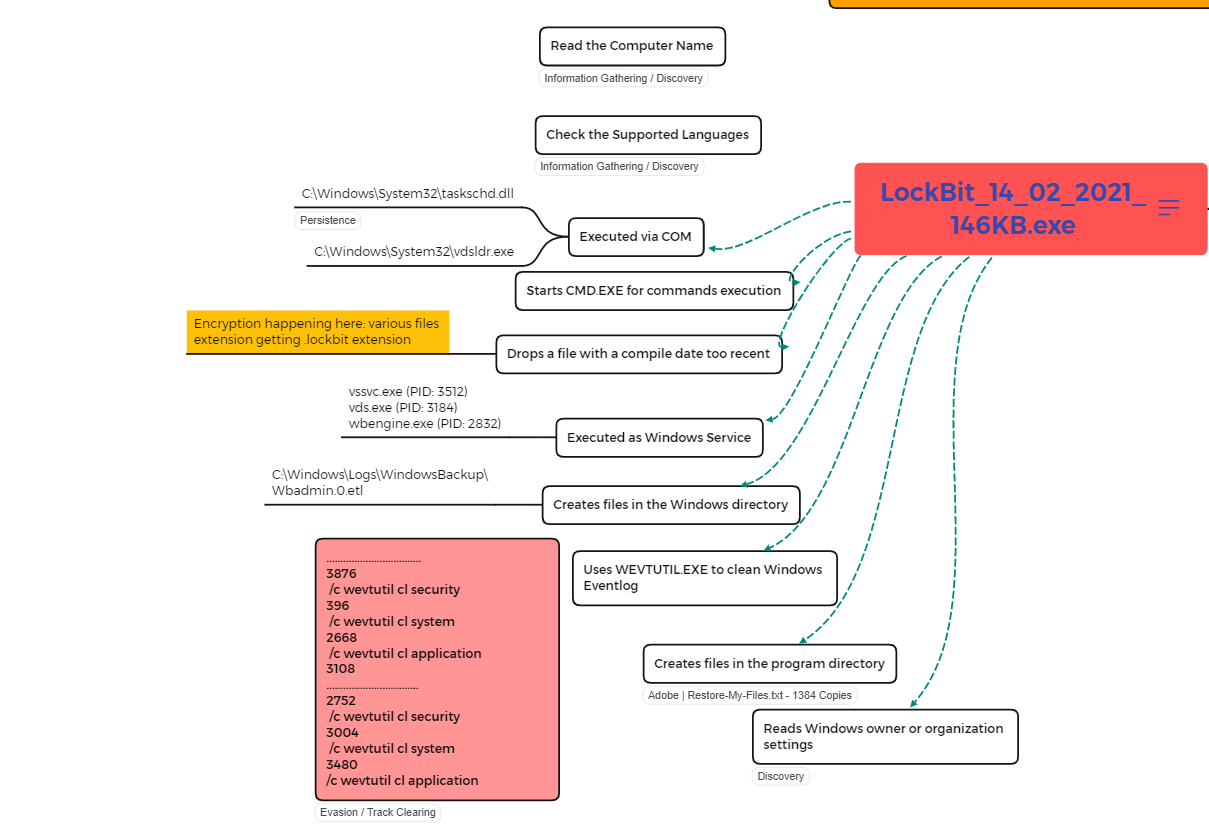
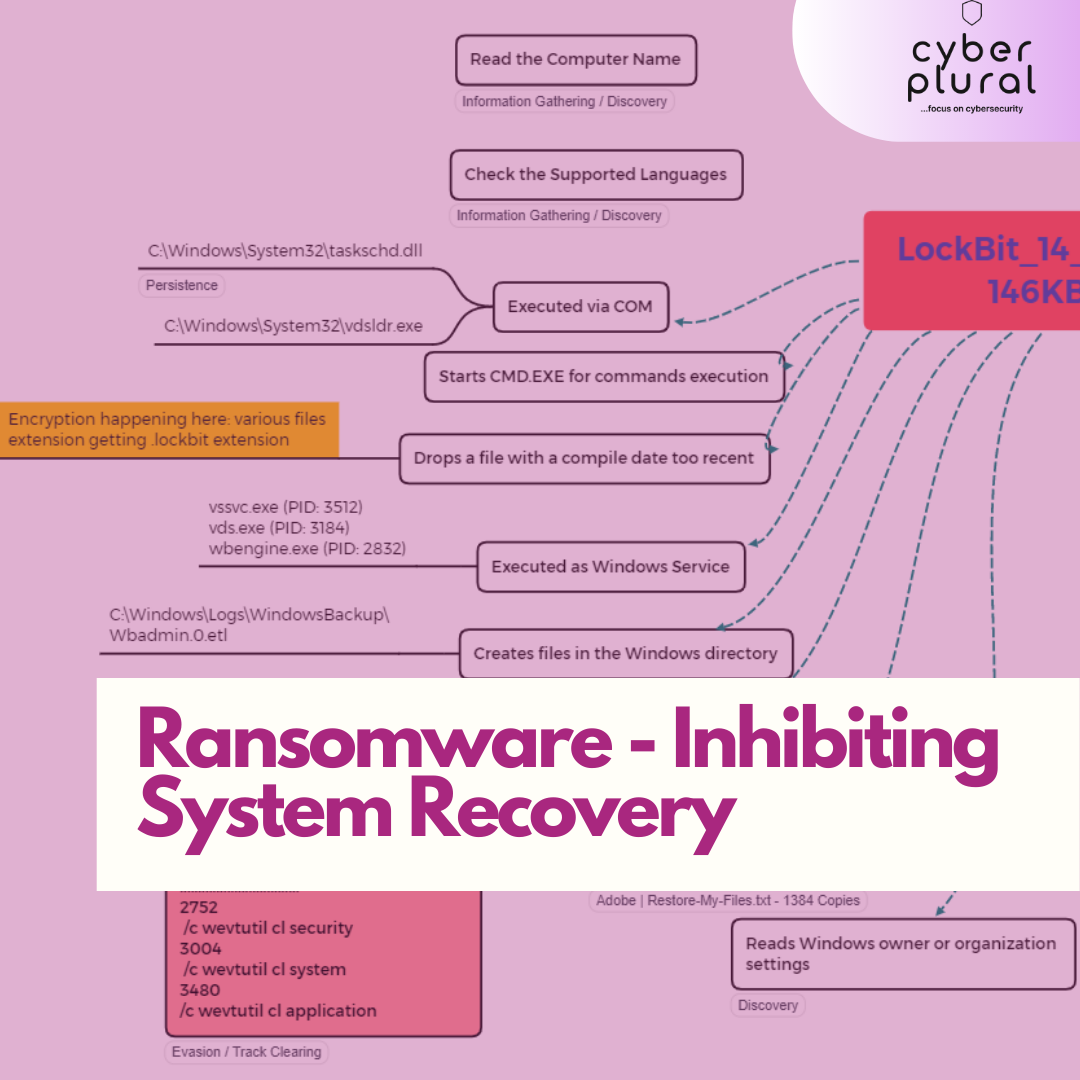
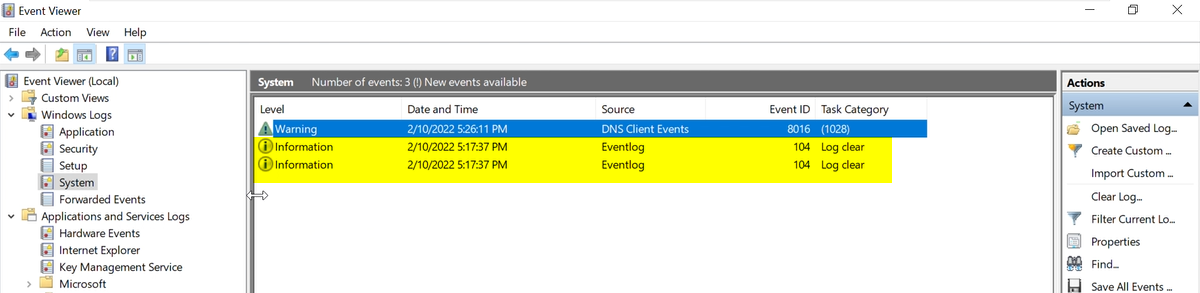
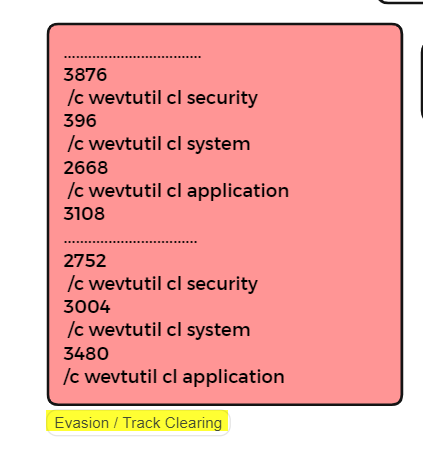
The executable was found to start by doing some discovery on the infected PC by reading the Computer Name from the registry and trying to capture the supported language (as this is a well-known MO ransomware group to be sure of the system they are on, as some have a preference to not encrypt system reading languages from the CIS Region). Several new files were created after the encryption took place, noted to be files compiled recently, with .lockbit extension. Log of those malicious actions was clearly removed from the infected PC as WEVTUTIL command got called twice as can been seen in the image above, and all security, system and application logs got deleted for track clearing. Restore-My-Files.txt was also dropped which contained the ransom note educating the victim how to get to pay the ransom.
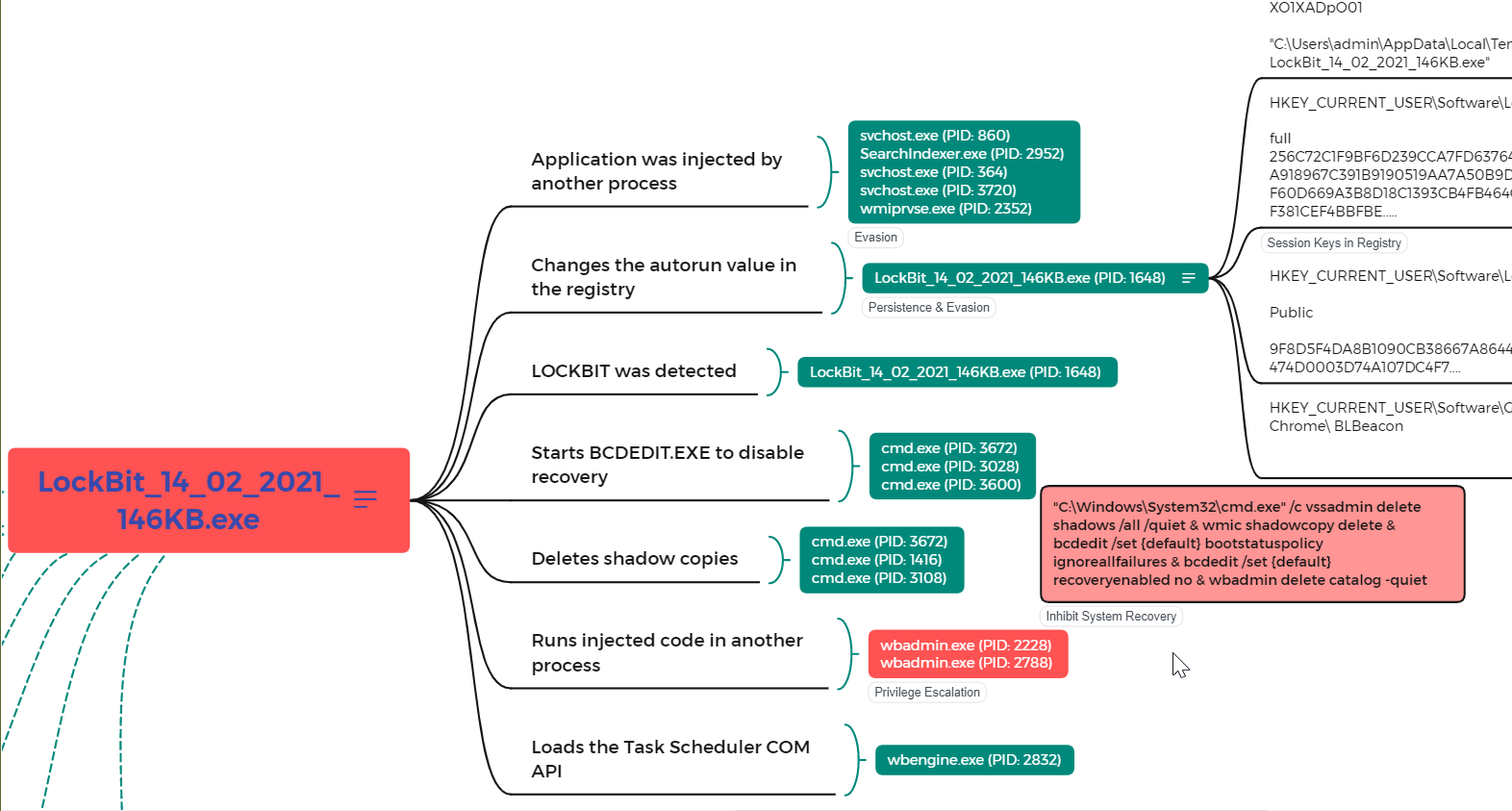
It was observed to have spawned a series of malicious activities using some valid Windows Applications & Processes (cmd.exe, wbadmin.exe, wbengine.exe, bcdedit.exe) such as processes getting injected into another for privilege gain, at the same time execution of the BCDEDIT.EXE to disable recovery, shadow copies were seen to have also been deleted, and loading of Task Scheduler through COM API to maintain persistence. Changes were also made to the registry for the same reason of persistence (addition of autorun data) and some creation of public and full session keys for the encryption. Beacon was also created in Chrome for continuous redirection of the user to the ransom page.
This behaviour has been taken to be an MO of ransomware presence on systems, which make it easier for anti-malware such as EDR and XDR detection to take place and future changes/manipulations in behaviour can also be considered.

Static Analysis
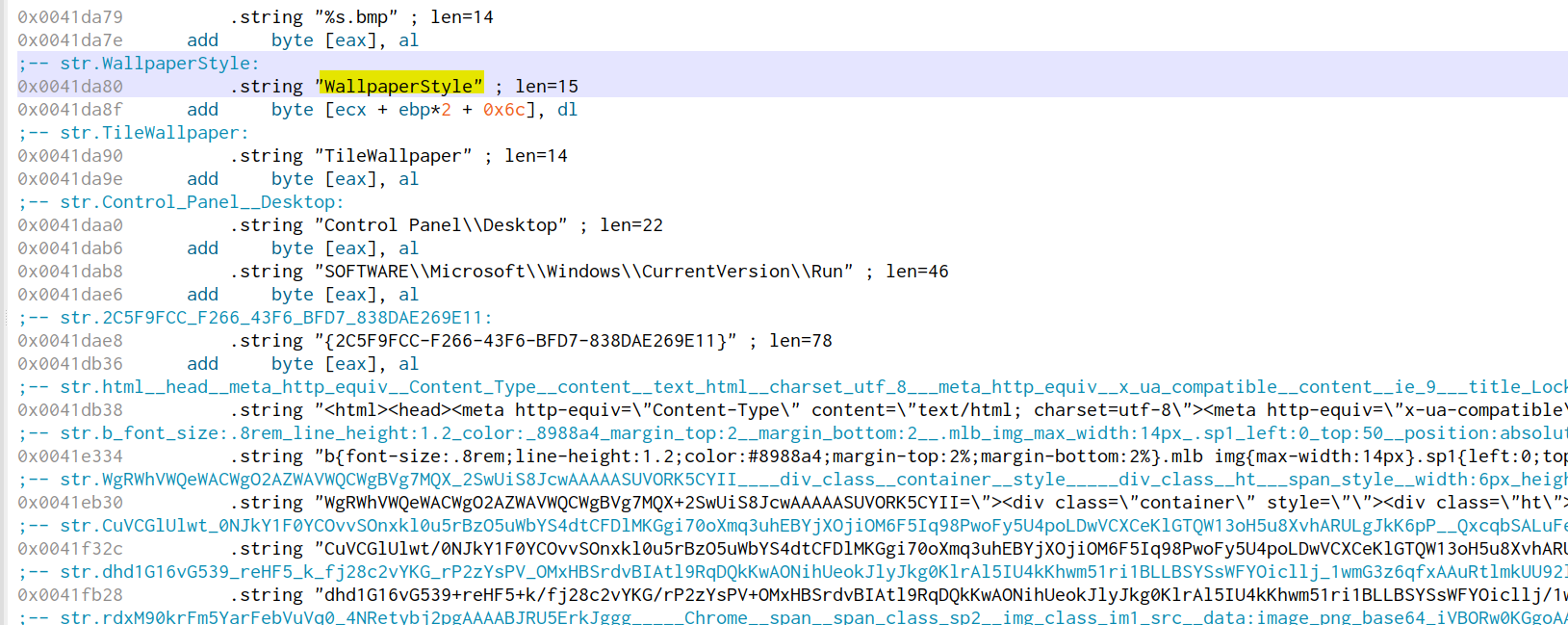
During the static analysis, we found out that some parts of the malware did not run in the test environment, which may be as a result of conditions that will trigger them that are not available on our test system. Some of those are shown below;

Infected systems are also made to have their desktop wallpaper changed to inform the users of the complete encryption of their system, which was captured during static analysis as shown below.
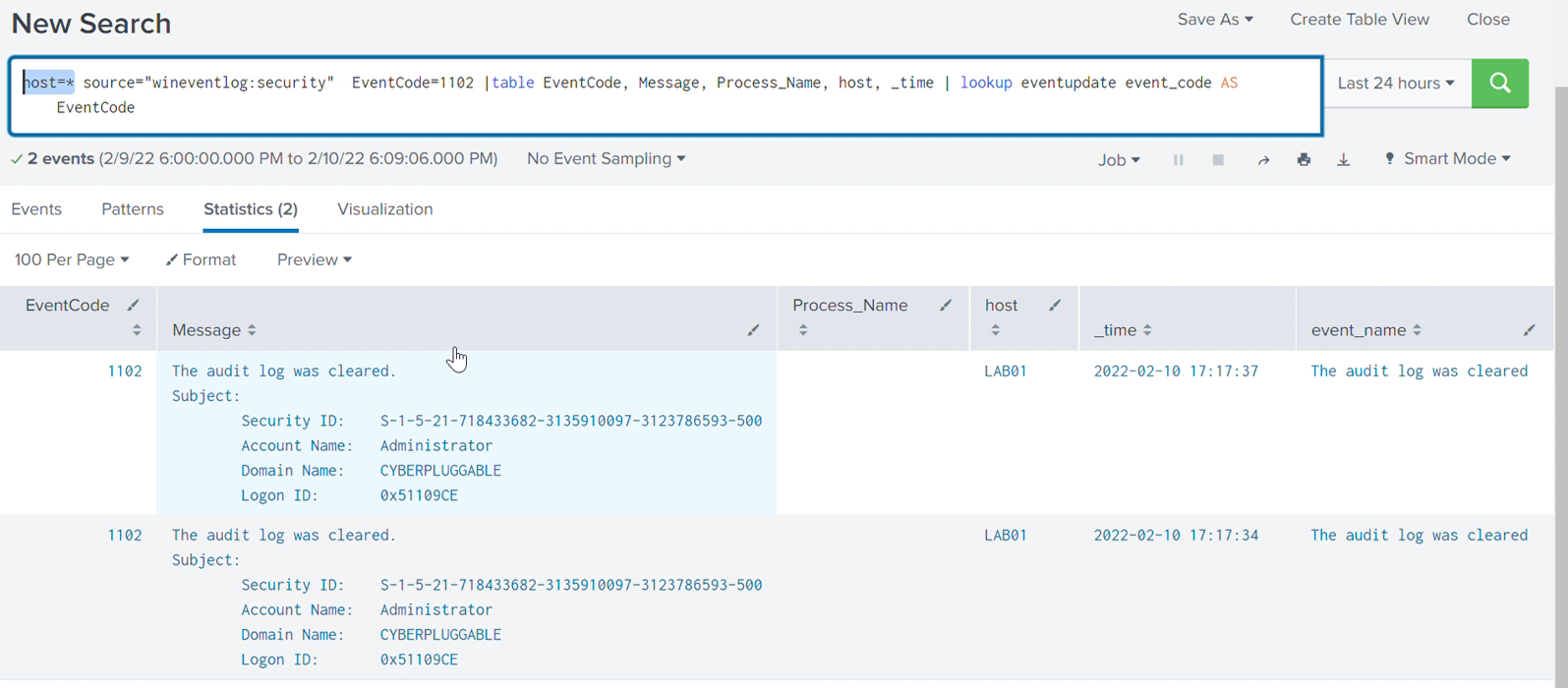
Understanding the ransomware file using static analysis to be capable of manipulating logs on endpoints, the test system was initially configured to send all its logs to the SIEM environment, which enabled us to identify and understand all of the activities during the dynamic analysis.
We would recommend the following to stay proactive against this type of incident;
- Implementation of the 3-2-1 Backup rule which allows you to have a backup in several locations to avoid a single point of failure and not to be caught by surprise.
- Keep your operating system and software up-to-date with the latest patches. Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker.
- Continous education of user on cyber awareness for them to stay proactive.
By Emmanuel Akobe-Ajibolu & Hamzah Lateef.

Leave a Reply