Active Directory Explained: Part 2 – Best Practices and Pitfalls to Avoid

Understanding IPv6 Threats in Active Directory
In today’s digital world, where businesses rely on networks to operate smoothly, it’s crucial to understand how new technologies like IPv6 and Active Directory (AD) can impact security. Let’s break down the basics and explore how these technologies intersect and what threats they might bring to your network.
IPv6: Think of it as a new type of address system for devices connected to the internet. It’s like a phone number for your computer, but much longer than the old system (IPv4), allowing for more devices to connect. IPv6 offers numerous benefits, including expanded address space and improved network efficiency
However, as organizations transition to IPv6 to accommodate the growing demand for internet-enabled services, the convergence of IPv6 and AD introduces new challenges and vulnerabilities that demand heightened vigilance such as Man-in-the-Middle (MitM) Attacks via IPv6.
Understanding MitM Attacks
MitM attacks occur when an attacker intercepts and potentially alters communication between two parties without their knowledge. By inserting themselves between the sender and receiver, the attacker can eavesdrop on sensitive information, manipulate data, or even impersonate one of the parties involved.
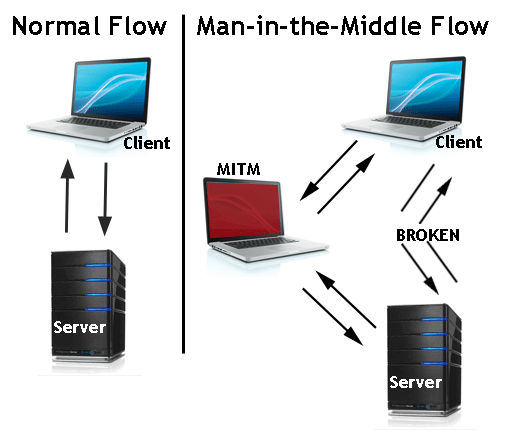
IPV6 Attack: It’s possible that networks may not be actively using IPv6. On most machines, IPv6 might be ON by default, but they primarily rely on IPv4. In such instances where IPv6 is enabled, there’s often no designated DNS server for IPv6. This gap presents an opportunity for attackers to step in and act as a DNS server for IPv6 on the network, allowing them to intercept and listen for IPv6 traffic.
Leveraging the DNS Server Role for Unauthorized Authentication
When the attacker takes on the role of a DNS server for IPv6, they can exploit this position to gain access to the domain controller (DC) through protocols like LDAP or SMB. With this access, they can extract valuable information, even if they don’t have administrative privileges. They simply wait for someone to log in or use their credentials, which provides the attacker with the NTLM hash through a responder. Using this hash, the attacker can perform LDAP Relaying to the Domain Controller with the acquired credentials. If the compromised account happens to be a domain administrator, a tool like mitm6 can create a new account with elevated privileges.
Mitigations
Exploiting IPv6 poisoning takes advantage of the behaviour in Windows where it queries for an IPv6 address even in environments that only support IPv4. To safeguard against potential mitm6 attacks in IPv4-only setups, the most secure approach is to block DHCPv6 traffic and incoming router advertisements in Windows Firewall using Group Policy. Completely disabling IPv6 could lead to unintended consequences. Should be turned off on machines that don’t require IPv6.
If WPAD isn’t being utilized, deactivate it through Group Policy and turn off the WinHTTPAutoProxySvc service.
Implement LDAP Signing and LDAP Channel Binding for added security.
Additionally, include Administrative users in the protected users’ group to mitigate risks of impersonation and delegation.
By Damian Pine and Amao Abdullateef

Leave a Reply