Exim Zero-Day Vulnerabilities: A Critical Risk to Your Mail Servers

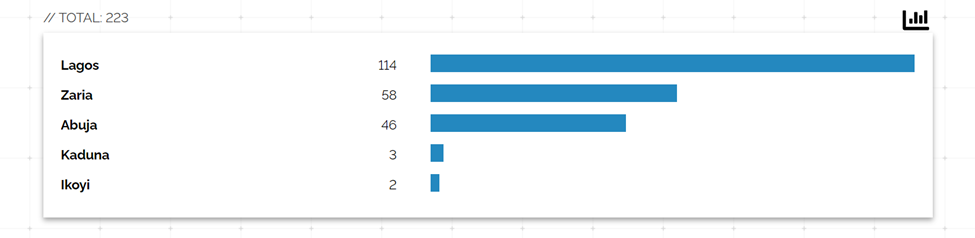
Our threat intelligence team has recently investigated vulnerable servers within our domain in light of the Exim zero-day vulnerabilities. A total of 223 servers running outdated versions of Exim (specifically version 4.96 and earlier) were identified. Additionally, we noticed that a security service provider’s honeypot was also running an old version of Exim.
The Exim Mail Transfer Agent (MTA) has been affected by multiple vulnerabilities, which were publicly disclosed by the Zero Day Initiative (ZDI). One critical vulnerability, CVE-2023-42115, allows unauthenticated attackers to remotely execute code on internet-facing Exim servers with “External” authentication enabled. This vulnerability is a result of improper input validation, leading to arbitrary code execution.
Exim is a widely used mail server, particularly as it comes preinstalled as the default MTA on Debian and other Linux distributions. According to a recent Mail Server Survey, Exim is the most popular MTA software globally, installed on over 56% of the 602,000 reachable mail servers on the Internet, totalling more than 342,000 Exim servers.
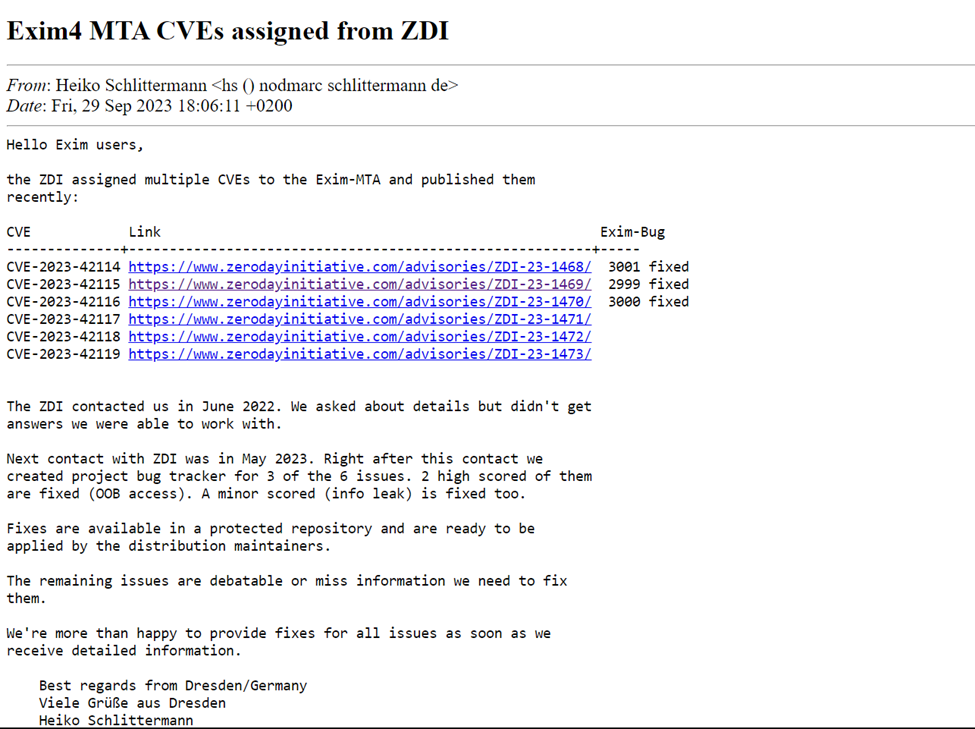
It is important to note that ZDI reported all these vulnerabilities to the Exim project maintainers in June 2022. Due to the lack of security patches being developed, the Zero Day Initiative decided to publish the advisories as zero-day vulnerabilities. The published CVEs include CVE-2023-42115, CVE-2023-42116, CVE-2023-42117, CVE-2023-42118, CVE-2023-42114, and CVE-2023-42119.
These vulnerabilities pose a significant risk, ranging from remote code execution to the exposure of sensitive information. Among them, CVE-2023-42115 is particularly critical as it allows remote execution without authentication.
Three of these zero-day vulnerabilities have been fixed so far, as confirmed by Exim developer Heiko Schlittermann on the Open-Source Security (oss-sec) mailing list. Workarounds have also been suggested by various security researchers and vendors, including Wiz.
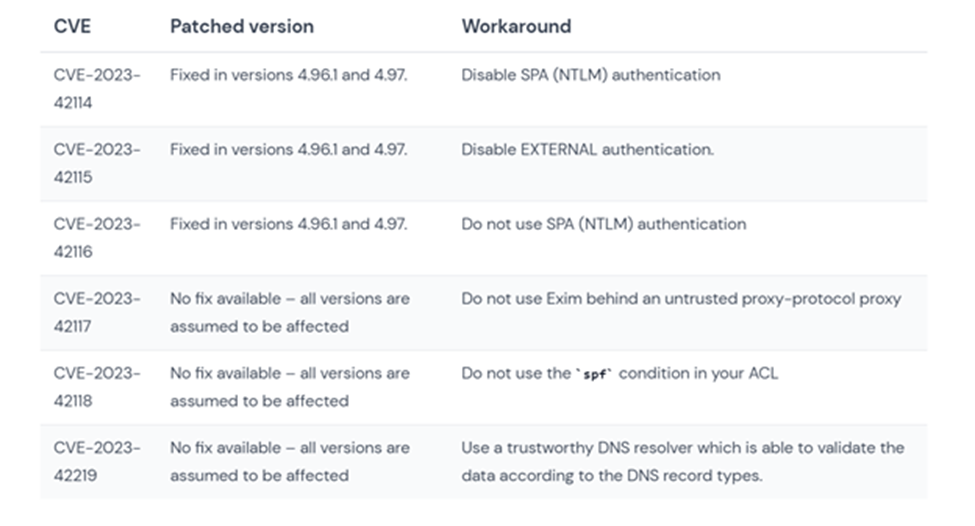
To ensure security, it is crucial for organizations and individuals to promptly address these vulnerabilities by applying patches and implementing recommended security measures. If you need assistance in fixing or implementing a workaround for your Exim server, feel free to contact CyberPlural.

Leave a Reply