Adopting Encrypted DNS in Enterprise Environments

Use of the Internet relies on translating domain names (like “cyberplural.com”) to Internet Protocol addresses. This is the job of the Domain Name System (DNS). In the past, DNS lookups were generally unencrypted, since they have to be handled by the network to direct traffic to the right locations. DNS over HTTPS (DoH) performs remote Domain Name System (DNS) resolution via the HTTPS protocol. A goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data by man-in-the-middle attacks by using the HTTPS protocol to encrypt the data between the DoH client and the DoH-based DNS resolver. By March 2018, Google and the Mozilla Foundation had started testing versions of DNS over HTTPS. In February 2020, Firefox switched to DNS over HTTPS by default for users in the United States.
What is DNS over HTTPs (DoH)?
Domain Name System (DNS) over Hypertext Transfer Protocol over Transport Layer Security (HTTPS), often referred to as DNS over HTTPS (DoH), encrypts DNS requests to provide privacy, integrity, and “last mile” source authentication for DNS transactions with a client’s DNS resolver. It is useful to prevent eavesdropping and manipulation of DNS traffic.
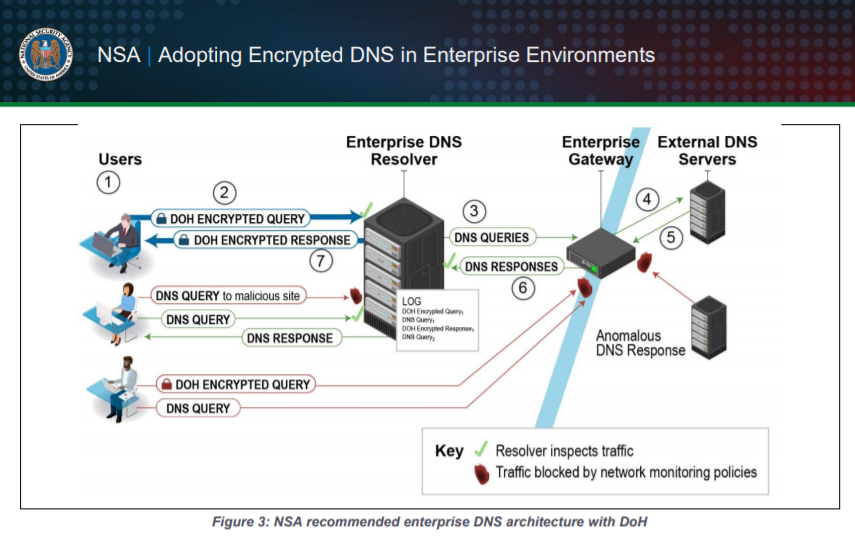
While DoH can help protect the privacy of DNS requests and the integrity of responses, enterprises that use DoH will lose some of the control needed to govern DNS usage within their networks unless they allow only their designated DoH resolver to be used. These essential protective DNS controls can prevent numerous threat techniques used for initial access, command and control, and exfiltration, such as phishing links to malicious domains, connections using dynamic name resolution, and commands hidden in DNS traffic.
Benefits of DoH
DoH protects DNS traffic between a client and a DNS resolver from unauthorized access to its information by cyber threat actors. Since the traffic is encrypted and blends in with other HTTPS traffic to websites, it is difficult for cyber threat actors to determine which packets contain DNS requests or responses and see which domains and IP addresses were requested. The responses from the DNS resolver are also authenticated and protected from unauthorized modification. In contrast, traditional DNS transactions occur in plaintext on a port that is exclusively used for DNS, so cyber threat actors can easily read and modify the traditional DNS traffic.
What are the issues with using DoH?
DoH provides the benefit of encrypted DNS transactions, but it can also bring issues to enterprises, including a false sense of security, bypassing of DNS monitoring and protections, concerns for internal network configurations and information, and exploitation of upstream DNS traffic. In some cases, individual client applications may enable DoH using external resolvers, causing some of these issues automatically.
For further reading, click here

Leave a Reply