FreakOut Malware Exploiting Critical Bugs to Infect Linux Hosts

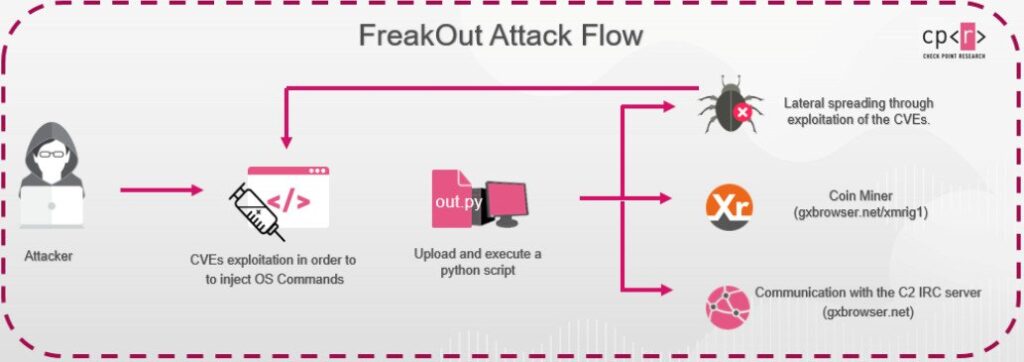
An ongoing malware campaign has been found exploiting recently disclosed vulnerabilities in network-attached storage (NAS) devices running on Linux systems to co-opt the machines into an IRC botnet for launching distributed denial-of-service (DDoS) attacks and mining Monero cryptocurrency.
The attacks deploy a new malware variant called “FreakOut” by leveraging critical flaws fixed in Laminas Project (formerly Zend Framework) and Liferay Portal as well as an unpatched security weakness in TerraMaster, according to Check Point Research’s new analysis published today and shared with The Hacker News.
Attributing the malware to be the work of a long-time cybercrime hacker — who goes by the aliases Fl0urite and Freak on HackForums and Pastebin at least since 2015 — the researchers said the flaws — CVE-2020-28188, CVE-2021-3007, and CVE-2020-7961 — were weaponized to inject and execute malicious commands in the server.
Check Point discovered the attack on January 8, 2021, when they noticed the malicious script being downloaded from hxxp://gxbrowser[.]net. Since then the researchers observed hundreds of attempts to download the code.

Leave a Reply