Web Application Firewall – Mitigating Risk Pose to Web Apps

Many businesses today depend on web applications to complement their services. But only a few consider the risk pose by this and even only fewer go further to mitigate this risk. One of the ways to mitigate this risk is through the use of a Web application firewall. This and other means can protect from an attack.
What is a WAF?
A web Application Firewall (WAF) is an application firewall that protects web applications against HTTP application attacks. It protects against attacks such as SQL injection, cross-site scripting, malicious file execution. WAF works at the application layer.
WAF inspects web traffic and analyzes this traffic, it inspects both GET and POST requests. A WAF sits in between a WEB application /WEB server and the WEB clients. It can detect and drop any malicious traffic.
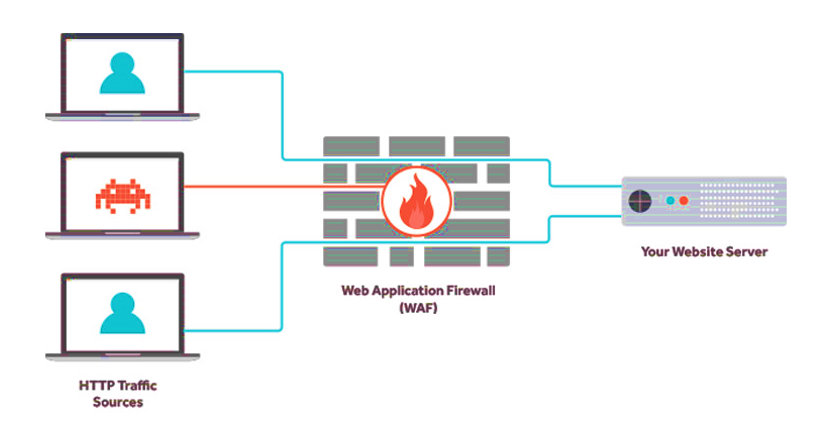
WAF protects against known vulnerabilities and the OWASP Top Ten which include
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting XSS
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging & Monitoring
WAF Configuration Model
There are different configuration models for a WAF with each having its pros and cons. Organizations can decide which one fits their organizations objective.
- Blocklist WAF model: This model works based on known vulnerabilities or specific signature as such this prevent traffic with such signature and behavior. The downside to this form of implementation is that new malicious signature emanate everyday, this will require regular update of the rules.
- Whitelist WAF model: This model allows only the signature you wants it to, that is those in use by the organization and blocks out every other traffic that does not fall into the allow list. The flip side to this is that whenever there is a new application to be used the signature needs to be updated.
- Hybrid WAF Model: This model combines the functionalities of both Blocklist and Whitelist model. This provides a more stronger defense.
WAF Implementations
WAF can be implemented in several forms depending on the needs. This implementation is explained below;
Host Base
This kind of implementation is implemented on the individual web application. It works as a standalone. Imagine an organization with ten(10) web applications using this form of deployment, which makes the task of updating and keeping track tedious. Although smaller organizations who lack the financial strength of implementing other forms can still use this deployment method. Some solutions in this category include ModSecurity and AQTRONIX WebKnight and many others.
Network Base
This is hardware-based and sits in data centres. This deployment allows for more flexibility in configuration and customization. Network-based WAF is faster in speed and high performance. This model is a massive investment and is used majorly by large organizations. One of the solutions for this deployment is Waaples
Cloud Base
This deployment works as SaaS. The organization using this service needs not worry about installation and configuration all this is handle by the service provider, all that is required is to subscribe to their service. The good side to this is the flexibility and it is not capital intensive as the Network base deployment. But any organization that needs full control of its WAF can not use this model as the control is handed over to the cloud service provider. This model can be used by both small and medium businesses. Examples of Service providers include Cloudfare WAF, Wallarm Cloud WAF, Radware Cloud WAF, SWAP with many more in the market.
WAF Explained with ModSecurity
To implement this we will create a login page vulnerable to SQL injection.
<html>
<body>
<?php
if(isset($_POST['login']))
{
$username = $_POST['username'];
$password = $_POST['password'];
$con = mysqli_connect('host','username','your_mysql_password','db name');
$result = mysqli_query($con, "SELECT * FROM `users` WHERE username='$username' AND password='$password'");
if(mysqli_num_rows($result) == 0)
echo 'Invalid username or password';
else
echo '<h1>Logged in</h1><p>This is text that should only be displayed when logged in with valid credentials.</p>';
}
else
{
?>
<form action="" method="post">
Username: <input type="text" name="username"/><br />
Password: <input type="password" name="password"/><br />
<input type="submit" name="login" value="Login"/>
</form>
<?php
}
?>
</body>
</html>
Created a MySQL database for our login page
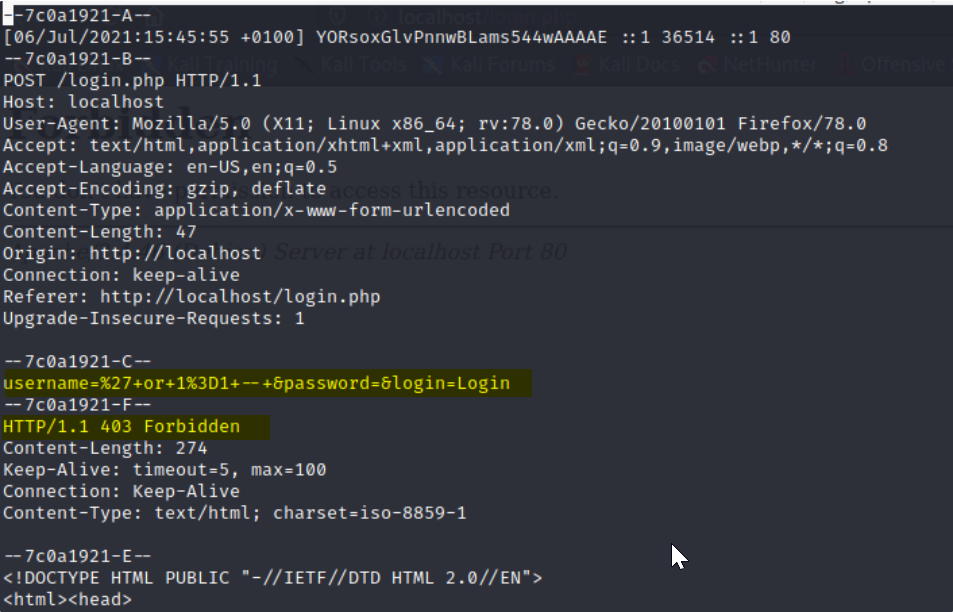
We now proceed to manually test SQL injection on this site with ‘ or 1=1 — With this injection the login was successful. Note that there is a space after —With ModSecurity turned on.

With ModSecurity, the SQL injection was not successful. There is a log file where all the activities of the WAF are stored. Which shows what happened at each instance. What is logged depends on the configuration that was done in your ModSecurity configuration file.
Conclusion
WAF has proven in many ways to provide resilience as part of an organizations security suite. Having a WAF can keep you in line with regulations such as PCI-DSS, HIPAA, GDPR, NDPR. A successful SQL injection will allow your users’ data will be exposed putting you in the eyes of the regulators.
To get the full benefit of WAF the ruleset needs to be configured properly if not it is just as not having a WAF installed.
Using a WAF does not mean web applications should remain vulnerable because the WAF can be bypassed therefore leaving a vulnerable web application at the mercy of the attacker. There are several WAF bypasses that the vendors and opensource community constantly try to patch but it’s a daunting task to keep up with the bypasses.
WAF is a good defense measure for web applications but just like in other areas of IT security, one security measure is not enough.
A holistic approach needs to be taken in order to ensure the security of web applications because WAFs themselves are assets that can be targeted and compromised.
The services of a fully functional SOC is necessary for continuous monitoring of events generated by the web applications and related assets.
Written by Faith Ariyo

Leave a Reply