Your Kindle Could Have Let Hackers Hijack Your Account by Sharing eBook

Amazon has addressed a number of flaws in its Kindle e-reader platform that could have allowed an attacker to take control of victims’ devices by simply sending them a malicious e-book.
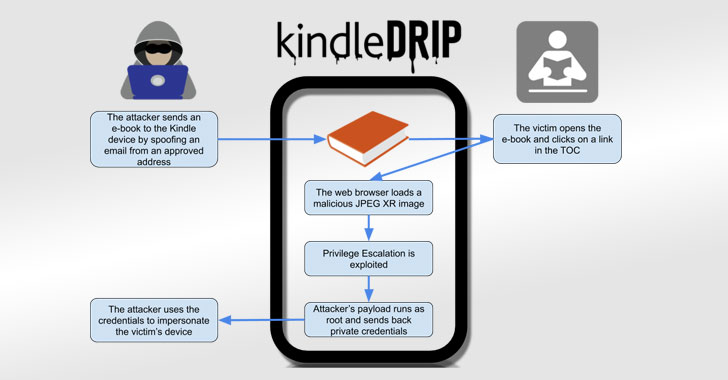
Dubbed “KindleDrip,” the exploit chain takes advantage of a feature called “Send to Kindle” to send a malware-laced document to a Kindle device that, when opened, could be leveraged to remotely execute arbitrary code on the device and make unauthorized purchases.
“The code runs as root, and the attacker only needs to know the email address assigned to the victim’s device,” said Yogev Bar-On, a security researcher for Readlmode Labs, in a technical write-up on Thursday.
The first vulnerability lets a bad actor send an e-book to a Kindle, the second flaw allows for remote code execution while the e-book is parsed, and a third issue makes it possible to escalate privileges and run the code as the “root” user.
When linked together, these weaknesses could be abused to swipe device credentials and make purchases on e-books sold by the attackers themselves on the Kindle store using the target’s credit card.
Amazon fixed the flaws on December 10, 2020, for all Kindle models released after 2014 following Bar-On’s responsible disclosure on October 17. He was also awarded $18,000 as part of the Amazon Vulnerability Research Program.

Leave a Reply