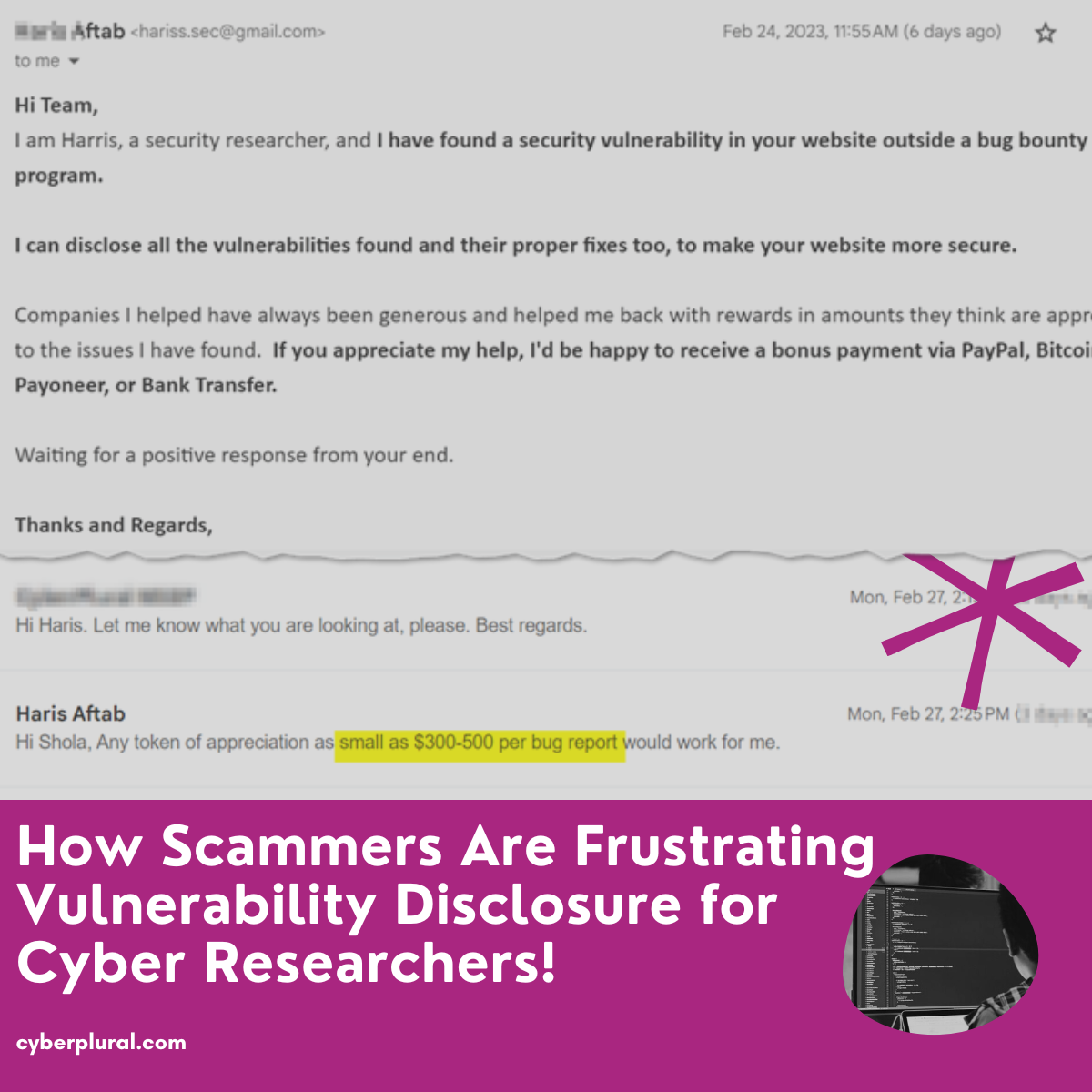
How would you react if you found this in your company inbox? You may want to ignore and many will take the fear bait and […]
Category: Threat
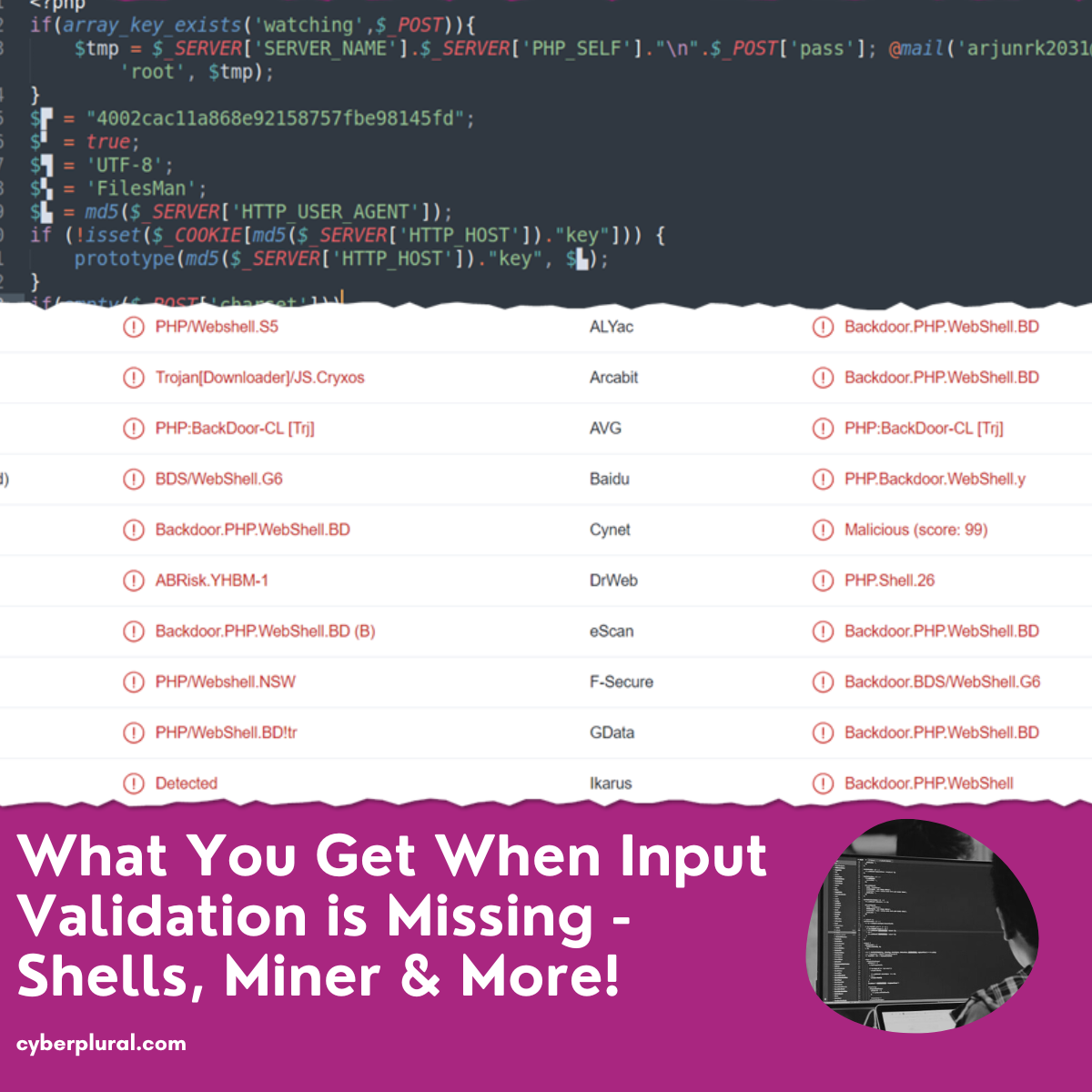
What You Get When Input Validation is Missing – Shells, Miner & More
Web applications and software frequently need user interaction to function properly. Users must be able to provide their email addresses and other personal information at […]
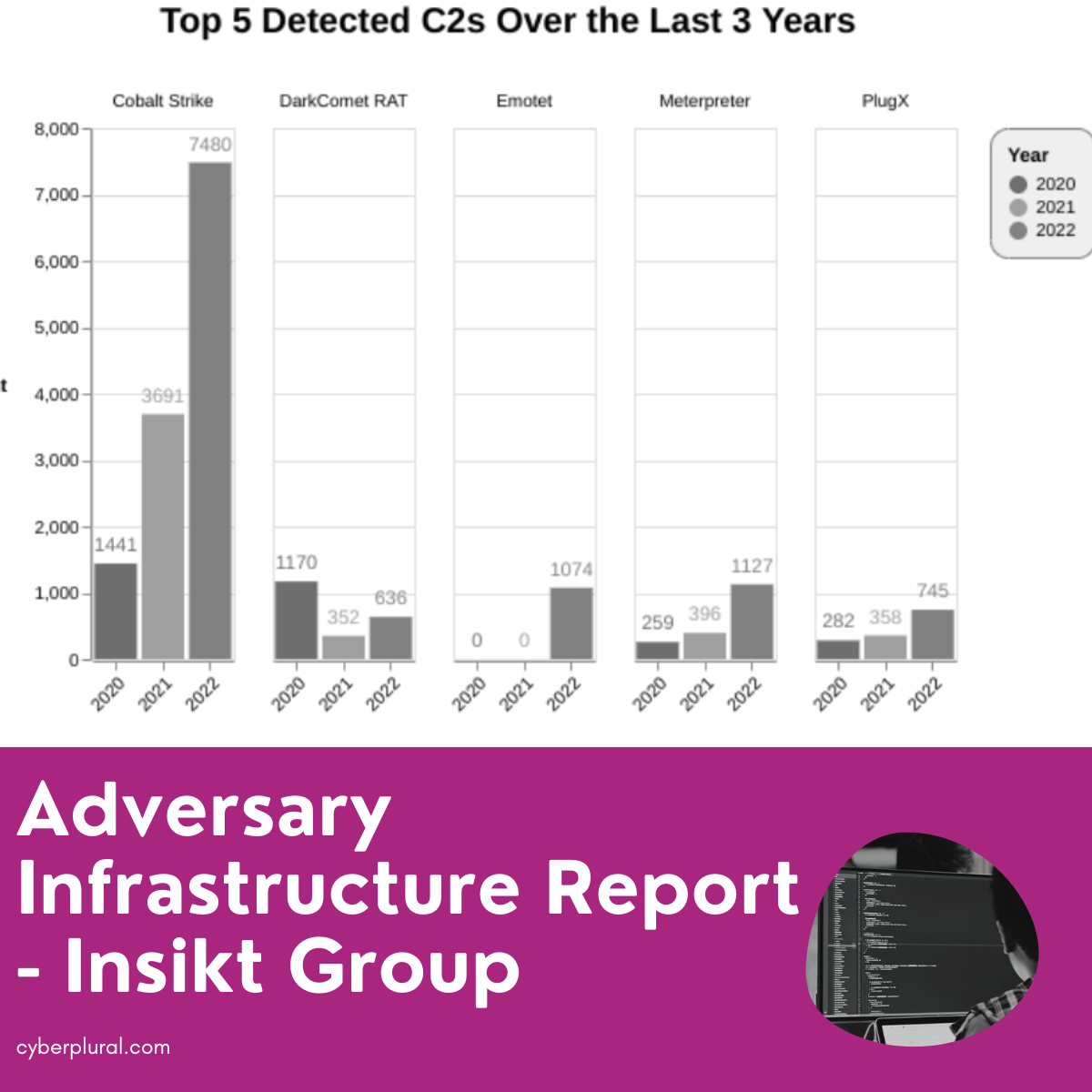
Adversary Infrastructure Report – Insikt Group
Insikt has released her 2022 Adversary Infrastructure Report. The report is based on its findings on the development of new harmful infrastructure for a variety […]
Beyond Fake INEC Portal, Threat Actor Targeting Users In 3 African Countries
Just some days ago, a fake INEC recruitment portal shows up in our space. And several media houses have reported INEC issuing a disclaimer around […]
Key Takeaways from Mandiant Cyber Security Forecast 2023
Key findings from the Mandiant Cyber Security forecast 2023-which shared forward-looking thoughts on the Global cyber security trends in areas such as Russia’s Cyber and […]
Threats Targeting Linux-Based Multi-Cloud Environments
In this blog post, we will be looking at the VMware Threat Analysis Unit Report which is focused on exposing malware in Linux-based multi-cloud environments. […]