Stay updated on the latest cyber threats and incidents in Nigeria and globally with CyberPlural ‘s Q3 2023 quarterly report. The report covers critical CVEs, threat intelligence, […]
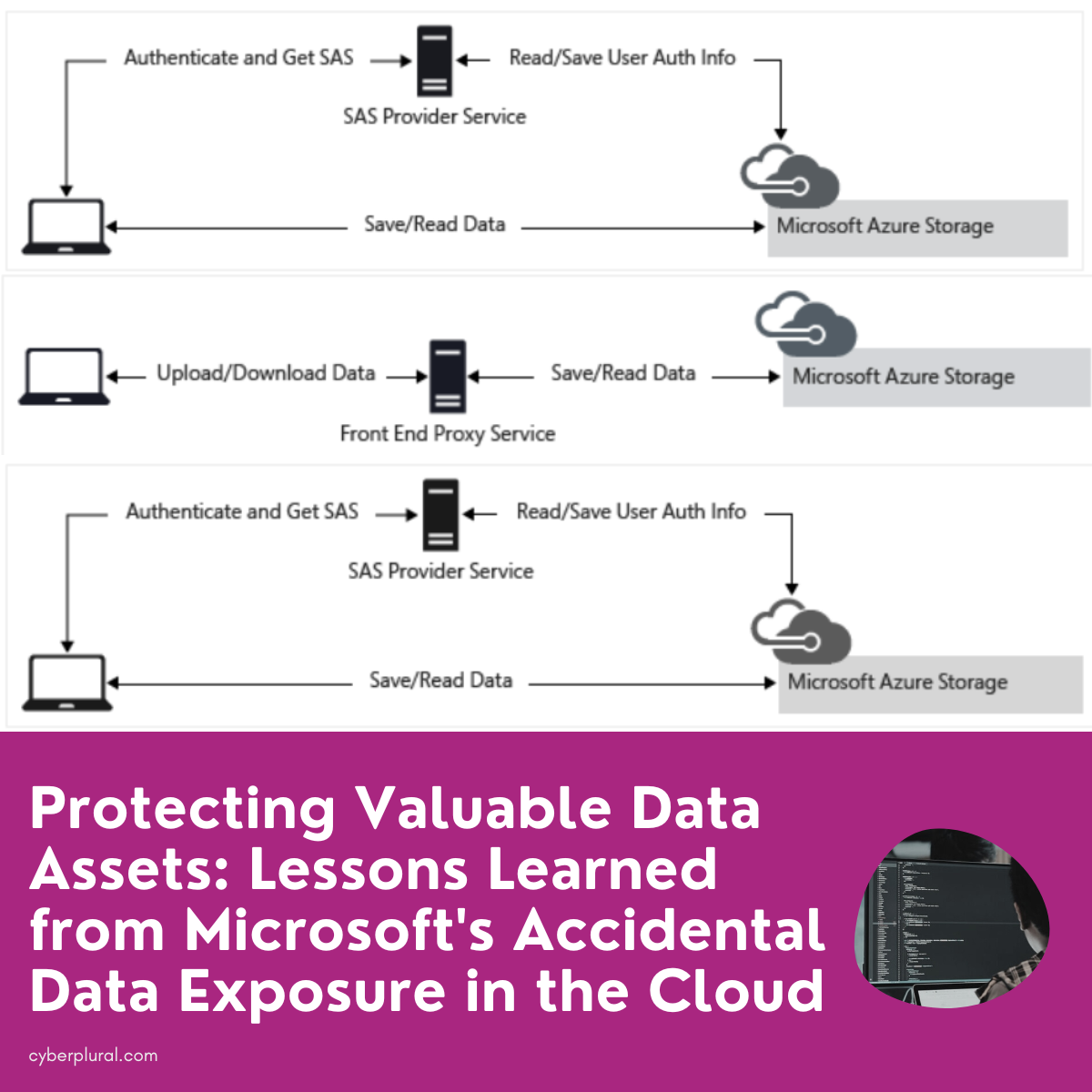
Protecting Valuable Data Assets: Lessons Learned from Microsoft’s Accidental Data Exposure
In the ever-evolving landscape of cloud technology, data security remains paramount. Recent events have shed light on the critical importance of safeguarding sensitive information, and […]
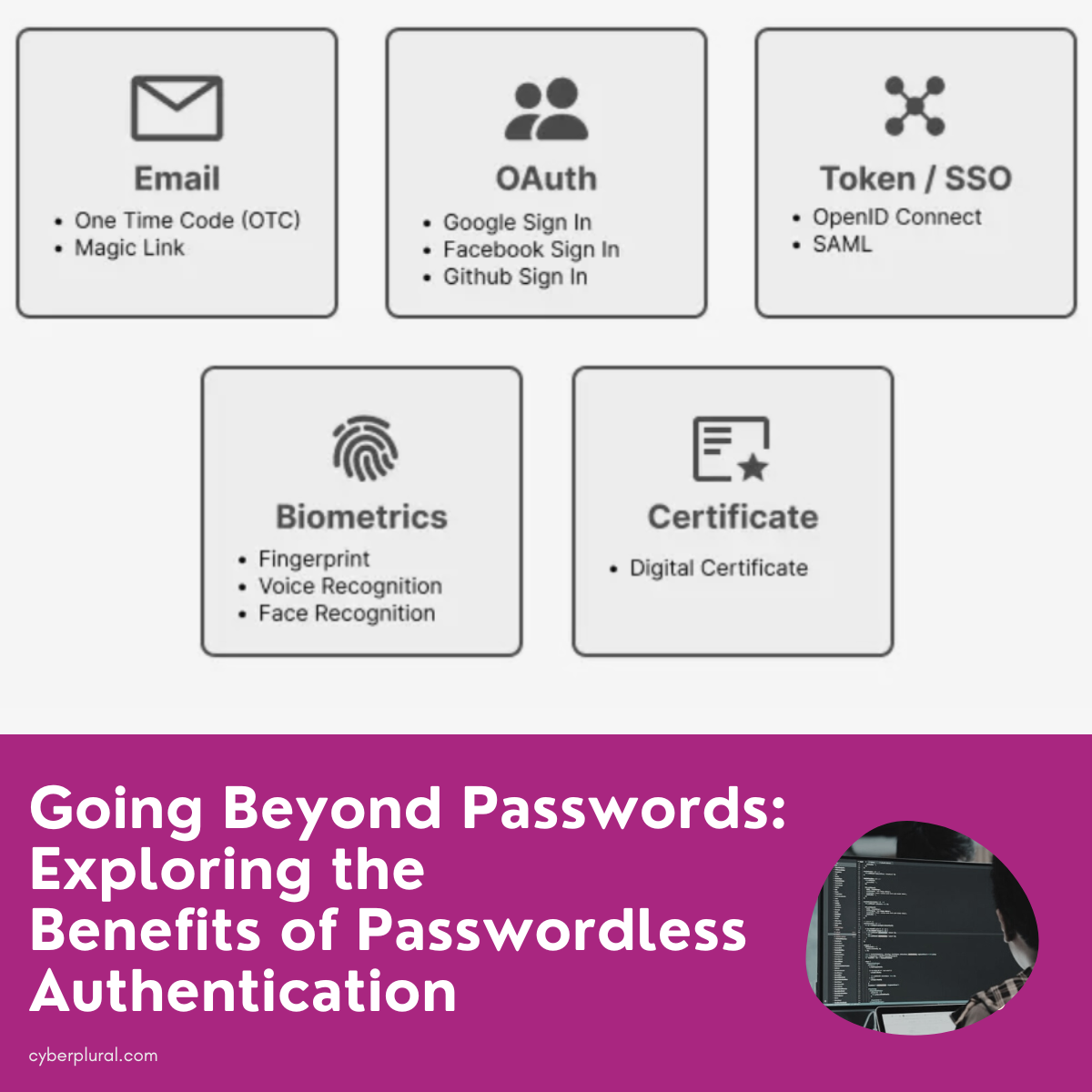
Going Beyond Passwords: Exploring the Benefits of Passwordless Authentication
Passwordless authentication is an increasingly popular method of securing online accounts and devices. As the name suggests, this approach eliminates the need for passwords, instead […]
Preventing Race Conditions in FinTech: Mitigating Security Vulnerabilities
Race conditions are a common security vulnerability that can affect financial technology (FinTech) systems. A race condition occurs when two or more processes access and […]
API Security Best Practices: Protecting Your Organization’s Digital Strategy
API security is a crucial aspect of any organization’s digital strategy, but it can be challenging to implement and maintain. In this blog post, we […]
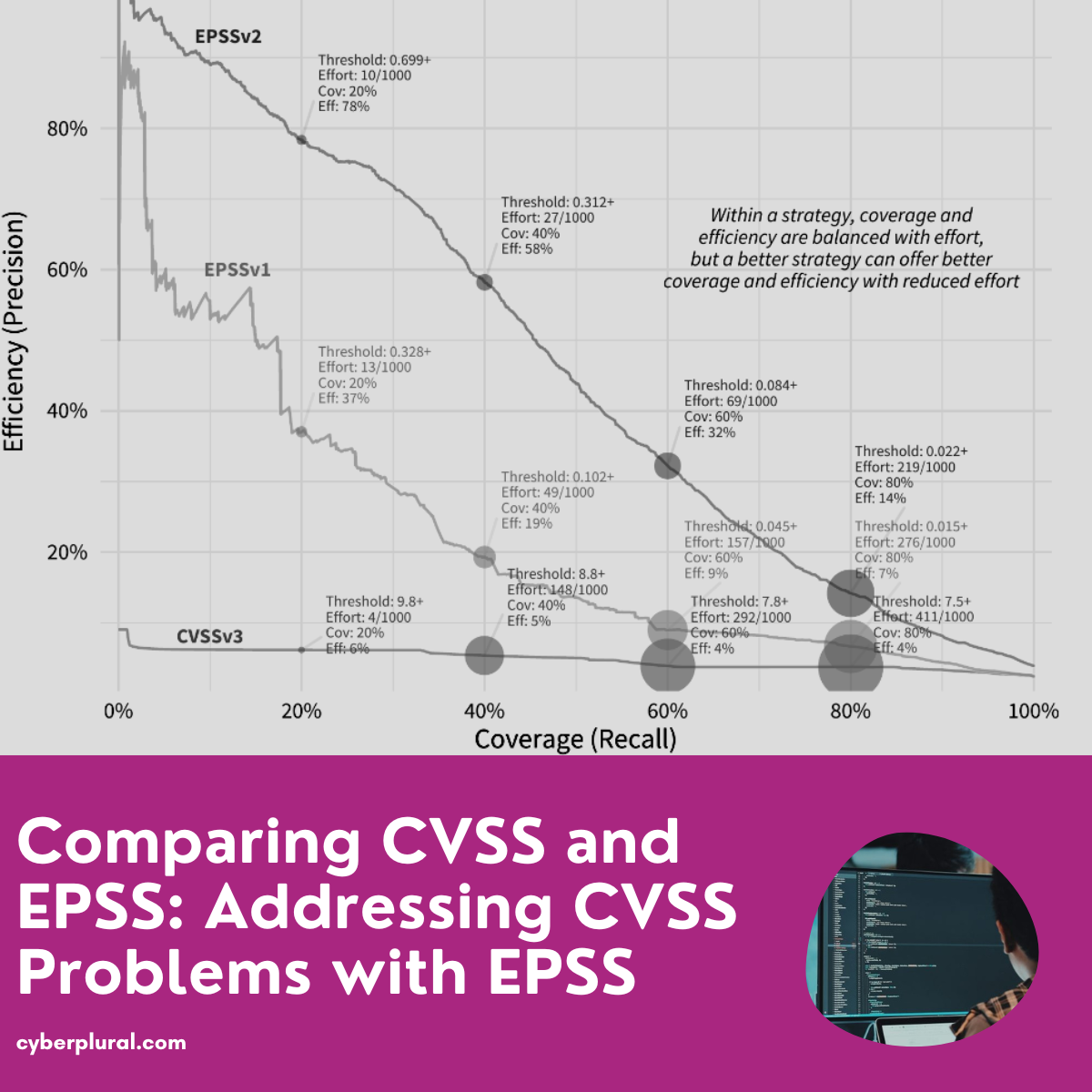
Comparing CVSS and EPSS: Addressing CVSS Problems with EPSS
What is CVSS? CVSS, or the Common Vulnerability Scoring System, can be viewed as the weather forecast for cybersecurity professionals. CVSS a free and open […]