Enhancing Security Resilience with Breach & Attack Simulation
In the ever-evolving landscape of cybersecurity, organisations face an ongoing battle to stay one step ahead of threat actors. Traditional security approaches often fall short in preparing for the real-world tactics, techniques, and procedures (TTPs) used by sophisticated attackers. This is where Breach & Attack Simulation (BAS) emerges as a powerful tool to enhance security operations and strengthen an organisation’s overall resilience.
Breach & Attack Simulation: A Proactive Approach
Breach & Attack Simulation is a cybersecurity technique that involves mimicking the actions of real-world attackers to test the effectiveness of an organisation’s security controls and incident response capabilities. By simulating a wide range of attack scenarios, security teams can identify vulnerabilities, validate the efficacy of their security measures, and refine their strategies to better defend against potential breaches.
Open-Source BAS Tools
The cybersecurity community has developed several open-source BAS tools that organisations can leverage to assess their security posture. These tools often provide a cost-effective way to conduct comprehensive security assessments and emulate advanced attack techniques.
Atomic Red Team: Developed by Red Canary, Atomic Red Team is a collection of small, highly focused, and automated tests that can be used to test security controls and validate incident response. It covers various attack techniques and can be easily integrated into an organisation’s security testing workflow.
Caldera: Caldera is an open-source, adversary emulation platform developed by MITRE. It allows security teams to create and execute complex attack scenarios based on real-world threat actors’ TTPs, enabling them to assess their security controls and identify potential gaps.
Infection Monkey: Infection Monkey is an open-source breach and attack simulation tool that helps organisations assess their network security by simulating various attack vectors, including lateral movement, privilege escalation, and data exfiltration.
Commercial BAS Solutions
While open-source tools provide a flexible and cost-effective option, some organisations may prefer commercial BAS solutions’ comprehensive capabilities and support. These tools often include advanced features, such as customisable attack scenarios, detailed reporting, and security orchestration and automation platform integration.
Infection Monkey
Infection Monkey is an open-source adversary emulation platform designed to help organisations validate their existing security controls and identify potential exploitation pathways that attackers might use to penetrate their network security defences. By simulating real-world attack scenarios, Infection Monkey provides valuable insights into network vulnerabilities and helps improve overall security posture.
Infection Monkey consists of two main components:
- Agent: The Agent is a configurable network worm capable of infecting machines, stealing data, and delivering payloads. It emulates the behaviour of sophisticated malware and advanced persistent threats (APTs), allowing security teams to see how an attacker might move laterally through the network, escalate privileges, and access sensitive information.
- Monkey Island: Monkey Island serves as the command and control (C2) server for Infection Monkey. It is used to manage and monitor the progress of the Agent throughout the simulation. Monkey Island provides a visual interface that allows security teams to control the infection process, track the Agent’s movements, and visualise the results of the attack simulation.
Using InfectionMonkey to Simulate an Attack.
For this test, We configured Infection Monkey on a Windows system, details on how to do this can be found here
We will be running it from the same system we have the island installed (The C2 server). This tool can be used to attack any system on the network just like an adversary will.
Note: For this operation, you will need to turn off your Windows Defender or any security tool you have installed if you just want to learn how it works, But if you are accessing your security you will need to power them on to see if it detects such attacks or not. In our case, we turned it off and executed the attack
Ransomware Attack
Simulates a ransomware attack on your network using a set of configurable behaviours.
To simulate ransomware encryption, you’ll need to provide Infection Monkey with files that it can safely encrypt. Create a directory with some files on each machine where the ransomware simulation will run. No files will be encrypted if a directory is not specified or if the specified directory doesn’t exist on a victim machine. For this test, we created two files as seen in the image below. After creating the directory and the files, we then copied the path to the infection money ransomware configuration tab.
After pasting the path, we clicked on the big green submit button headed to the run monkey tab and ran the attack. This tool then went ahead to perform the encryption and as seen in the picture below, it returned a report on the number of files it was able to encrypt.
Infection Monkey has lots of capabilities, if we are to show all of them we might end up writing a book on this tool.
Security Reports
After executing all your attacks, this tool can produce a report showing the attacks executed and the target system. On the report tab, you can see the successful attacks and you also have an option to print the report.
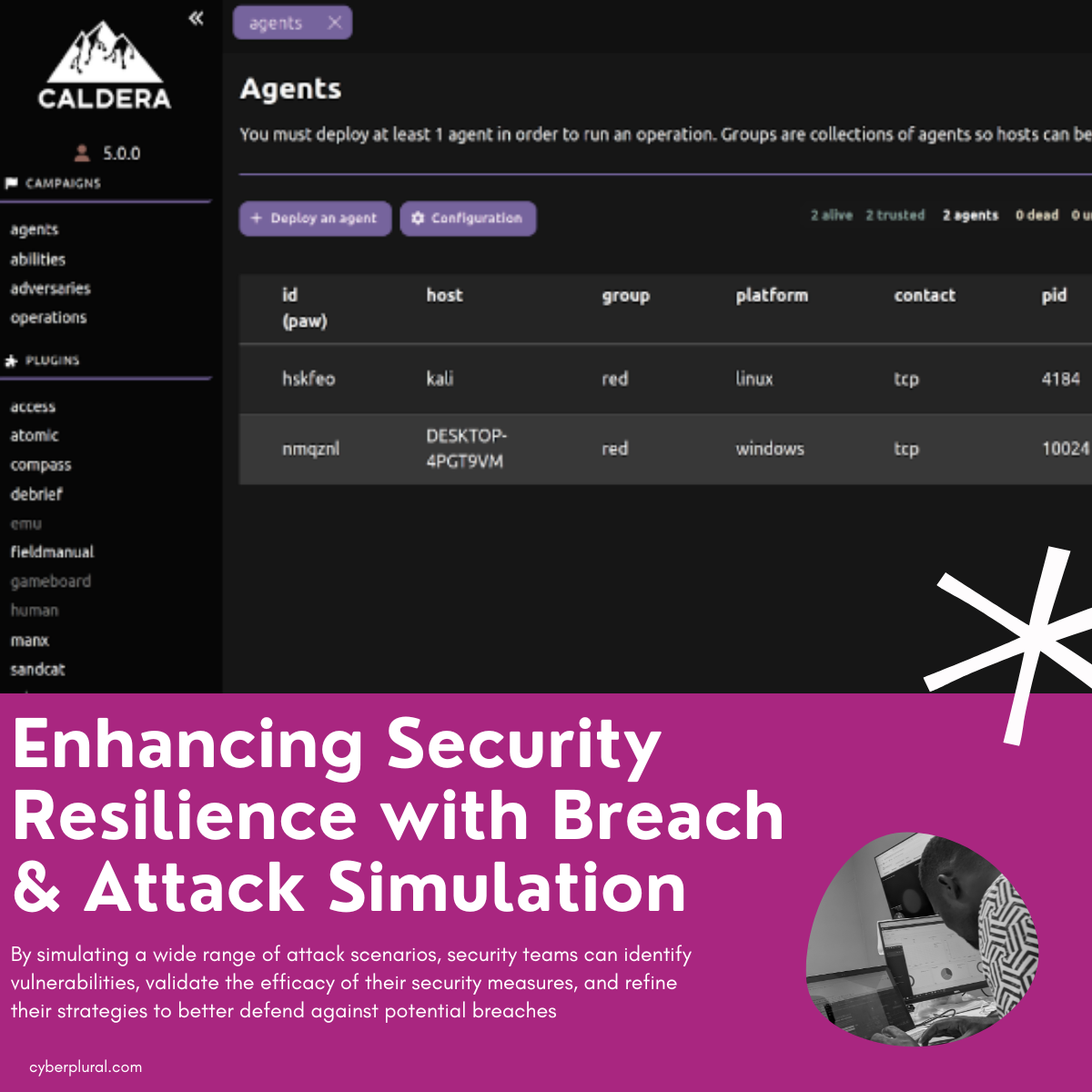
Caldera
Caldera is an open-source automated adversary emulation platform developed by MITRE, designed to simulate real-world cyber attacks to test and improve security defences. It provides a comprehensive framework for executing and managing red team operations with a focus on using the MITRE ATT&CK framework.
Essential Terminology
An Ability is an implementation of a specific ATT&CK tactic or technique that can be executed on agents, including the necessary commands, platforms, payloads, and modules for parsing output. An Adversary profile comprises a set of abilities representing the tactics, techniques, and procedures (TTPs) of a threat actor, used in operations to determine executable abilities. Agents are software programs installed on target hosts that communicate with the Caldera server to receive and execute instructions, categorised into Groups based on operating systems or functions for organising and managing operations.
Our Setup
To use Caldera, we set up a virtual lab with three operating systems: Ubuntu Linux as the Caldera server, and Kali Linux and Windows 10 as target systems. The Ubuntu server was configured with 8 GB RAM, 100 GB storage, and 4 CPUs, while the Kali Linux and Windows 10 targets were configured with 3 GB RAM, 100 GB storage, and 2 CPUs each. After setting up the lab, we installed necessary dependencies (NodeJS, Python 3, npm, GoLang) on the Kali Linux server, cloned the Caldera repository, and installed its dependencies to prepare the server for running Caldera.
Caldera has many capabilities, including command and control operations, red team automation, and real-time visibility, among others. These capabilities provide a comprehensive toolkit for simulating various cyber threats. For this exercise, we will demonstrate creating a reverse shell on both Windows and Linux systems. After setting up the reverse shells, we will execute an attack on the target systems.
Configuring an Agent
After we had successfully created a Caldare server instance on our Ubuntu system, we then moved to configuring an agent by clicking on the agent tab. suc
To deploy an agent simply click on agents at the lets sidebar, then click on the configuration to configure the agent you will be presented with a window that looks like this:
As mentioned earlier we configured an agent capable of creating a reverse shell on our target. Having selected this we click on the save button and this is saved then we go back and click on the deploy button. Here we will need to ensure that the IP address is the same as the IP of our Caldera server, by default, the IP address is 0.0.0.0:8888 but we changed it to the IP of our VM running the Caldera server as seen below.
Attacking the target
Now that our agent is ready, we only need to copy and paste the command on the target OS. Starting with Windows, the command was copied and pasted into a PowerShell prompt and the terminal on our target OS.
We did the same on the Linux target and it created a reverse shell on both targets.
Installing PSTools on the target
Using the reverse shell we then created, we then downloaded PS tools on both targets. To do this, we click on Accessibility and then click on Run ability, this presents us with options of the ability to configure, we configured this ability to download PS tools to the target and executed it.
Clicking on the execute button, the attack successfully downloaded PStools on the Windows target however, it failed to download on the Linux target.
The reason for this failure is that PStools is meant for the Windows platform and not Linux, this shows that the attack was not only successful but accurate
Conclusion
Breach & Attack Simulation is a crucial component of a robust security operations strategy. By leveraging both open-source and commercial BAS tools, organisations can proactively identify vulnerabilities, validate the efficacy of their security controls, and enhance their overall resilience against evolving cyber threats. By continuously testing and refining their security measures, organisations can stay one step ahead of adversaries and protect their valuable assets.

Leave a Reply