What is Defense in Depth Defense in Depth is a cybersecurity strategy that employs multiple layers of security controls throughout an organization’s IT environment to […]
Category: Security Products
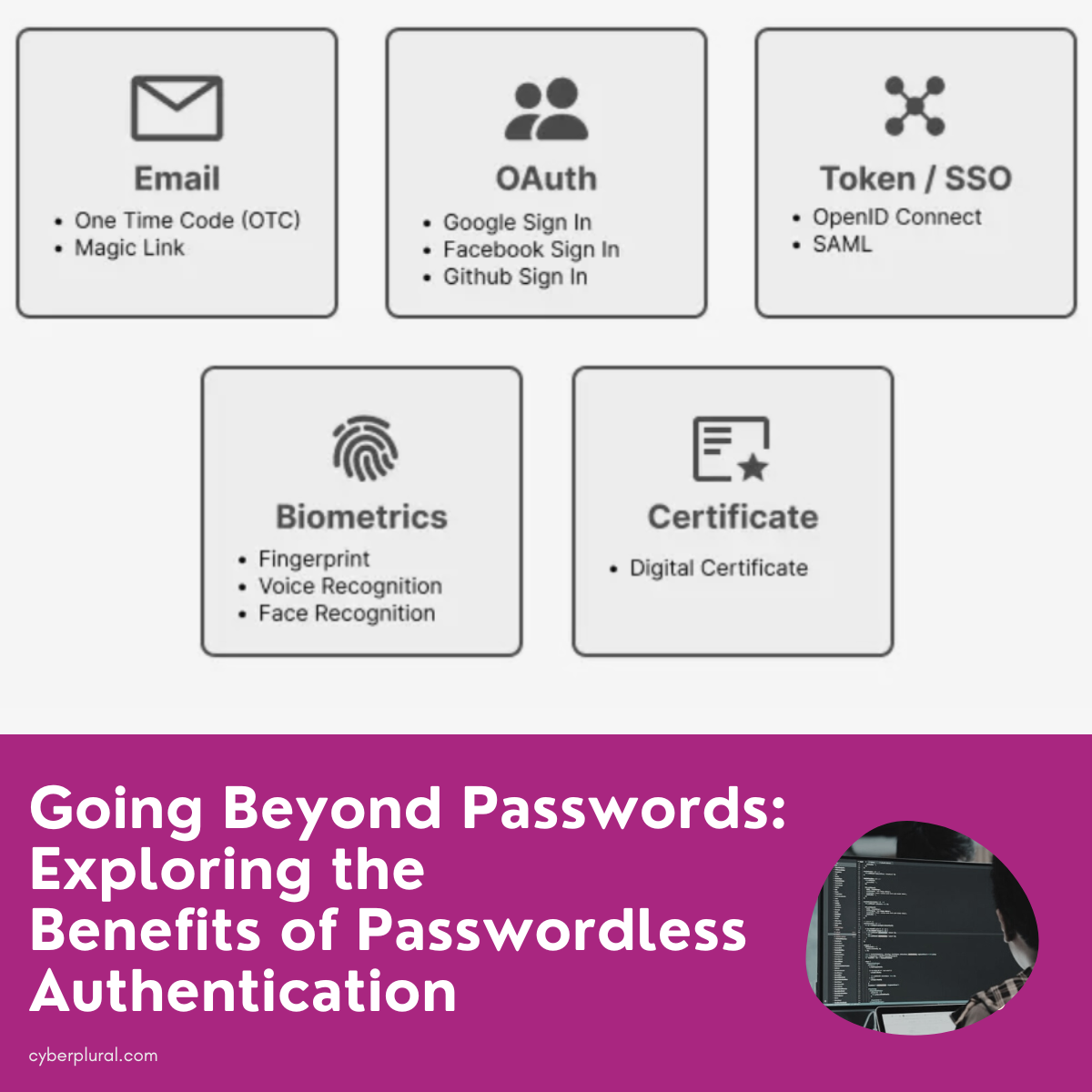
Going Beyond Passwords: Exploring the Benefits of Passwordless Authentication
Passwordless authentication is an increasingly popular method of securing online accounts and devices. As the name suggests, this approach eliminates the need for passwords, instead […]
How Deception Technology Adds Value To Security Operations.
Deception technology is a cybersecurity defense practice that aims to deceive attackers by distributing a collection of traps and decoys across a system’s infrastructure to […]
A Walkthrough of DARPA SSTIH Program-Mitigating Hardware Issues from Source.
DARPA and Galois Inc. DARPA is an agency of the U.S. Department of Defense with a mission to make pivotal investments in breakthrough technologies for […]
Web Application Firewall – Mitigating Risk Pose to Web Apps
Many businesses today depend on web applications to complement their services. But only a few consider the risk pose by this and even only fewer […]
Intel partner with Cybereason to build anti-ransomware defences into new chips.
Intel and Cybereason have partnered to build anti-ransomware defenses into the chipmaker’s newly announced 11th generation Core vPro business-class processors. The hardware-based security enhancements are baked into […]