Nigeria is ranked third most traded cryptocurrency country after the US and Russia. This is due to many factors such as currency sustenance, unemployment, high […]
Can Gig Workers Pose a Hidden Cybersecurity Risk To Your Organization?
What is commonly referred to as the Gig workforce has massively revolutionized global work culture over the last few years, especially in the tech industry […]
How Legacy Systems have become Soft Landing for Threat Actors.
A legacy VPN system gave access to the ransomware gang that breached Colonial Pipeline and made them pay a whooping sum of $4.4 million dollar […]
Defense Evasion – Malware In Bitmap
Defense Evasion consists of techniques that adversaries use to avoid detection throughout their compromise. Techniques used for defense evasion include uninstalling/disabling security software or obfuscating/encrypting […]
Top Breaches of the last 5 years.
Cyberattacks have become a common feature of today’s interconnected world. As more organizations transition their data operations online, the sheer volume of attacks has increased […]
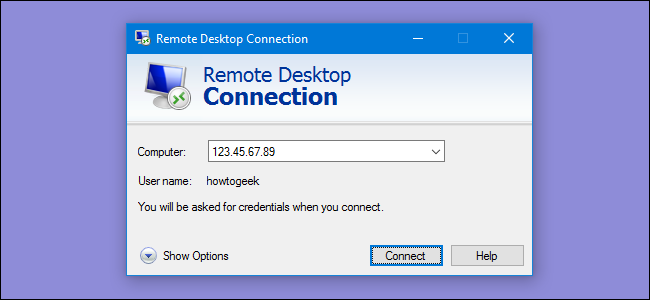
Attackers Abusing Windows RDP servers to amplify DDoS attacks
Researchers from Netscout reported that attackers could be abused to launch UDP reflection/amplification attacks with an amplification ratio of 85.9:1 when enabled on UDP/3389, “When […]